This week: weak creds open the door for Mirai, malvertising campaigns compromise enterprise targets, and it looks like big companies aren’t the first target of ransomware gangs. In our latest Cyber Intelligence Brief, we look at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading MDR provider, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- Aqua Security: Tomcat Under Attack: Exploring Mirai Malware and Beyond
- Sophos X-Ops: Into the tank with Nitrogen
- Proofpoint: Out of the Sandbox: WikiLoader Digs Sophisticated Evasion
- Picas Security: CVE-2023-2868: Barracuda ESG Vulnerability Actively Exploited by UNC4841
- Cyble: Sneaky XWorm Uses Multistage Attack
- Trellix: Uncover the Hidden Story of Ransomware Victims – They’re Not Who You Think
- The Latest Additions from Data Leak Sites
- CISA Adds 3 CVEs to its Known Exploited Vulnerabilities Catalog
Understanding these threats and taking action on our suggested mitigation strategies will prepare you to bolster your organization’s defenses.
Weak Credentials in Apache Tomcat Deliver Mirai Botnet
According to a 2023 Weak Password Report, the top base word in leaked Nvidia passwords is “Nvidia.” We all know weak passwords aren’t just the sin of office workers, they’re also a problem for people with critical access to networks.
A recent blog post from Aqua Security provides analysis of the TTPs employed by threat actors to infect Apache Tomcat servers with the Mirai malware to enroll the servers into the Mirai botnet. Apache Tomcat servers feature a manager application accessible from the internet, making them valuable targets for threat actors.
Threat actors used a brute force attack to guess the password of an account with weak credentials, accessing the web application manager of an Aqua Tomcat honeypot. They then deployed a WAR file containing a web shell, enabling remote code execution. The threat actors then downloaded and executed a shell script, which downloaded and ran the Mirai malware.
The threat actors targeted and gained access to the Apache Tomcat manager application interface by scanning for internet-exposed Apache Tomcat servers and logging in using weak usernames and passwords with the manager-gui role listed in the configuration file tomcat_users.xml. Their objectives included gaining initial access, deploying a web shell, and enrolling servers into a variant of the Mirai botnet, and they have shown a low to moderate degree of knowledge, skill, and resources. Threat actors can use the botnet to offer DDoS services or mine cryptocurrency.
Given the widespread usage of Apache Tomcat in the cloud, big data, and website development, it’s highly likely that organizations using Tomcat with manager-gui role accounts using weak credentials will be affected by this threat.
The impact of this threat can be severe. Once the threat actor gains access to the server, they have complete control. They can deploy webshells, execute remote commands, and download and execute malware. Hosts infected with the Mirai botnet malware can be used as a base for further malicious activity, ranging from cryptomining to using infected devices to conduct Distributed Denial of Service (DDoS) attacks.
Threat Actors Employ Malvertising and Impersonation Techniques for Enterprise Compromise
A Nitrogen malvertising campaign is abusing Google and Bing Pay-per-Click (PPC) advertisements to mimic legitimate software distribution websites and deceive users into downloading malicious Windows Installer files. Targeting IT users, the campaign impersonates widely-used software such as AnyDesk, WinSCP, and Cisco AnyConnect VPN installers.
When users download the trojan-ized installers, they appear as ISO images containing the msiexec.exe Windows tool, renamed to install.exe or setup.exe, and when executed, it sideloads a malicious msi.dll (NitrogenInstaller) file.
Analysis from Sophos X-Ops and comments from ATI cover threat actors’ intentions, adaptability, potential risks, and estimated future behavior.
Overall, analysis reinforces the importance of downloading software from officially approved sources. Regular training sessions should raise awareness of the prevailing risks and tactics employed by the threat actors.
WikiLoader Phishing Campaign: Characteristics, Infection Mechanisms, and Payload Analysis
Proofpoint has identified a new malware tool WikiLoader, a malware loader used by TA544 and TA551. It is delivered through phishing emails and employs various evasion techniques, including sandbox detection. The malware has targeted Italian organizations and shows sophisticated evasion methods and a custom encryption algorithm, making it a notable threat.
TA544 is known for its phishing campaigns and malware distribution. The group has been observed targeting various sectors, including finance, healthcare, and government organizations. The primary objective of TA544 is to steal sensitive information, such as login credentials, financial data, or personal information, which can then be used for various malicious purposes, including identity theft, financial fraud, or even ransomware attacks. TA551 (Shathak) primarily targets English-speaking victims through email phishing campaigns. It has been active since at least February 2019. Initially, TA551 distributed different malware families, including Ursnif (Gozi/ISFB), Valak, and IcedID.
To mitigate the risk posed by the malware WikiLoader delivered in phishing campaigns by TA551 and TA544, organizations should implement the following mitigation measures within the normal business cycle:
- Conduct regular cybersecurity awareness training for employees to educate them about phishing attacks, suspicious emails, and the importance of not clicking on unknown links or downloading attachments from untrusted sources.
- Utilize advanced email filtering solutions to detect and block phishing emails containing WikiLoader.
- Prevent users from launching embedded files in Microsoft OneNote files, like .cmd, through Group Policy settings using the “Embedded Files Blocked Extensions” template available from Microsoft here.
Additional threat hunting guidance and general mitigation guidance can be found in our full report.
UNC4841’s Exploitation of CVE-2023-2868: Risk and Impact Analysis and Outlook
A blog post from Picus Security details a critical remote command injection vulnerability (CVE-2023-2868) found in Barracuda Email Security Gateway (ESG). This zero-day vulnerability, with a CVSS score of 9.8, has been actively exploited by the Chinese cyber threat group UNC4841 since October 2022. The vulnerability allows adversaries to execute arbitrary commands remotely, and despite an initial patch, it continues to be exploited. Barracuda estimates that 5% of their 11,000 devices worldwide are impacted, and mitigation measures include isolating and replacing affected products.
UNC4841 is a cyber espionage group primarily supporting the Chinese government. Their campaigns have been mainly directed toward organizations in the Americas, with a third of the targets being governmental organizations. Individuals working within government or research institutes have also been targeted, likely due to their access to political or strategic information. UNC4841’s exploitation of CVE-2023-2868 involves sending emails with malicious files crafted to exploit the vulnerability using file extensions like TAR, JPG, or DAT. Once delivered, the crafted malicious file executes a reverse shell payload, allowing control over the affected system.
This specific exploitation of Barracuda ESG is part of a broader pattern of sophisticated and aggressive cyber operations by UNC4841, reflecting their ongoing commitment to cyber espionage and their evolving tactics, techniques, and procedures.
The likelihood of organizations being affected by the exploitation of CVE-2023-2868 is significant, particularly for those utilizing Barracuda Email Security Gateway (ESG). With a CVSS score of 9.8 (Critical), this zero-day vulnerability has been actively exploited by UNC4841 since October 2022. Barracuda estimates that 5% (550) of their 11,000 devices worldwide are impacted, indicating a notable risk to organizations using these versions of Barracuda ESG.
UNC4841 will likely continue targeting organizations that align with their known objectives, such as governmental organizations and research institutes. Given their focus on political or strategic information, they may also extend their targets to include other sectors holding valuable intelligence, such as defense contractors, manufacturing, and energy. The exploitation of CVE-2023-2868 could be a part of a broader campaign, and UNC4841 may seek to exploit other vulnerabilities in systems commonly used within their target industries.
The impact that organizations face from the exploitation of CVE-2023-2868 is severe. The vulnerability allows threat actors to execute arbitrary commands remotely, potentially leading to unauthorized access to sensitive information, lateral movement within the network, and further exploitation of internal systems. The ability of UNC4841 to circumvent initial patches adds to the complexity of mitigation.
Threat Actors Are Using Legitimate Binaries in Malware Infection Chains
Cyble Research and Intelligence Labs (CRIL) conducted an in-depth analysis of XWorm, uncovering a novel and concerning trend. The multistage attack chain employed by XWorm involves using Living Off the Land Binaries (LOLBins) and legitimate software coupled with WebDAV servers for code execution and downloads. XWorm is versatile, with capabilities ranging from data theft to DDoS attacks and ransomware deployment.
The infection chain of the XWorm malware is a complex, multistage process. Based on the sample analyzed by Cyble, it can start with a .lnk file suspected to be attached to phishing emails. Upon opening, it triggers a PowerShell process with the “ExecutionPolicy Bypass” option, accessing a remote PowerShell script from a web server using the WebDAV protocol. This script downloaded a zip file containing a batch script, which is then executed on the victim’s machine.
This batch script acts as the primary loader for the final payload. Unlike previous delivery techniques, this attack employed a multi-file approach, incorporating .ps1, .vbs, and .bat files. The BAT file copies a legitimate “PowerShell.exe” file, renames it with a “.scr” extension, and executes obfuscated PowerShell code. It also drops two additional files in the %AppData% folder, including a self-copy of the original BAT file and a VBScript, which is then executed to run the BAT file, effectively evading detection by antivirus products.
Once the XWorm malware is successfully delivered and executed, the threat actor has a wide array of post-compromise activities at their disposal. XWorm is designed to be versatile, with capabilities including stealing sensitive data, executing Distributed Denial of Service (DDoS) attacks, acting as a clipper, deploying ransomware, and downloading additional malware into the compromised system. The malware’s multifaceted functionality allows the threat actor to perform various malicious activities depending on their specific goals and targets.
The likelihood of organizations being affected by the XWorm malware is relatively high. The infection chain begins with a deceptive .lnk file, which could be distributed through spam emails, a common attack vector that can reach a wide range of targets. Using Living Off the Land Binaries (LOLBins) and a multi-file approach, including .ps1, .vbs, and .bat files, adds complexity to the attack and helps evade detection by antivirus products. The fact that XWorm is classified as commodity malware, available for purchase by various threat actors, further increases the potential reach of this threat. The availability of XWorm as commodity malware makes it plausible that all sectors could be at risk.
The impact of the XWorm malware on organizations can be severe and multifaceted. The malware’s capabilities could lead to financial loss, identity theft, and reputational damage. Its ability to execute Distributed Denial of Service (DDoS) attacks can disrupt services and operations. The malware’s functionality as a clipper to alter cryptocurrency addresses and its capability to deploy ransomware can lead to direct financial loss. Additionally, the ability to download further malware into the compromised system can lead to extended and escalated intrusions, potentially affecting various aspects of an organization’s infrastructure.
Using LOLBins and legitimate software as vehicles for delivering the malicious payload complicates detection and mitigation, potentially prolonging the duration of the compromise and exacerbating the overall impact. The recommendations provided in the blog post, such as using security products to detect phishing emails, refraining from opening untrusted links, and educating employees, highlight the need for robust cybersecurity strategies to mitigate these risks.
Defining the Ransomware Victim: Most Victims Are Small and Mid-Sized Businesses
A blog post by Trellix Advanced Research Center, titled “Uncover the Hidden Story of Ransomware Victims – They’re Not Who You Think,” sheds light on the misconception that ransomware threat actors primarily target large corporations. Through an extensive analysis of nearly 9,000 global ransomware victims, the research reveals that small to mid-sized businesses are significant targets.
The data spans 97 different ransomware groups over two years and includes insights into the distribution of victims based on company size, revenue, and sector. The findings emphasize the need for organizations to recognize their vulnerability and allocate resources toward intelligent and comprehensive security protections.
The most prolific ransomware groups, as identified by Trellix’s research, present a significant threat to organizations of various sizes and industries. Leading the list is Lockbit, responsible for approximately 27% of publicly extorted victims, followed closely by Clop at 14.57%. Other notable groups include Alphv (4.09%), Conti (3.72%), Pysa (3.43%), Hive (2.16%), Blackbasta (2.12%), Royal (2.12%), and Vice Society (2.11%).
Of note is that these numbers were collected before the Clop MOVEit attack at the end of June 2023, which would have pushed Clop far above Lockbit. These groups have demonstrated a capacity to target a wide range of victims, from small businesses to large corporations, across different sectors. Their TTPs vary, but their collective impact underscores the urgent need for organizations to enhance their security posture and implement robust defenses against the ransomware threat. The data also suggests that the landscape is diverse, with many groups actively engaging in ransomware activities, highlighting the complexity and persistence of this cyber threat.
In the United States, the ransomware threat landscape exhibits a distinct pattern of targeting, with specific industries facing a higher risk. The industrial sector leads the way, accounting for 35.65% of incidents, followed by consumer services at 19.90%, and the financial and technology industries also being significantly impacted, accounting for 9.50% and 9.47% of the cases, respectively.
Globally, the data reveals a similar focus on specific industries, with the industrial sector bearing the brunt of the attacks, accounting for 24.61% of incidents, and the consumer services sector following at 14.28%. Other sectors, such as technology, healthcare, and finance, have also experienced notable attacks. Interestingly, a substantial portion of the data, 27.28%, falls into an “unknown” category, indicating instances where the victim’s sector was not specified or remains undisclosed. This concentration of attacks within specific industries, both in the U.S. and globally, provides valuable insights into the preferences of threat actors and demonstrates the broad reach of ransomware activities, emphasizing that no industry is immune.
Over 100 Victims Posted This Week on Ransomware Data Leak Sites
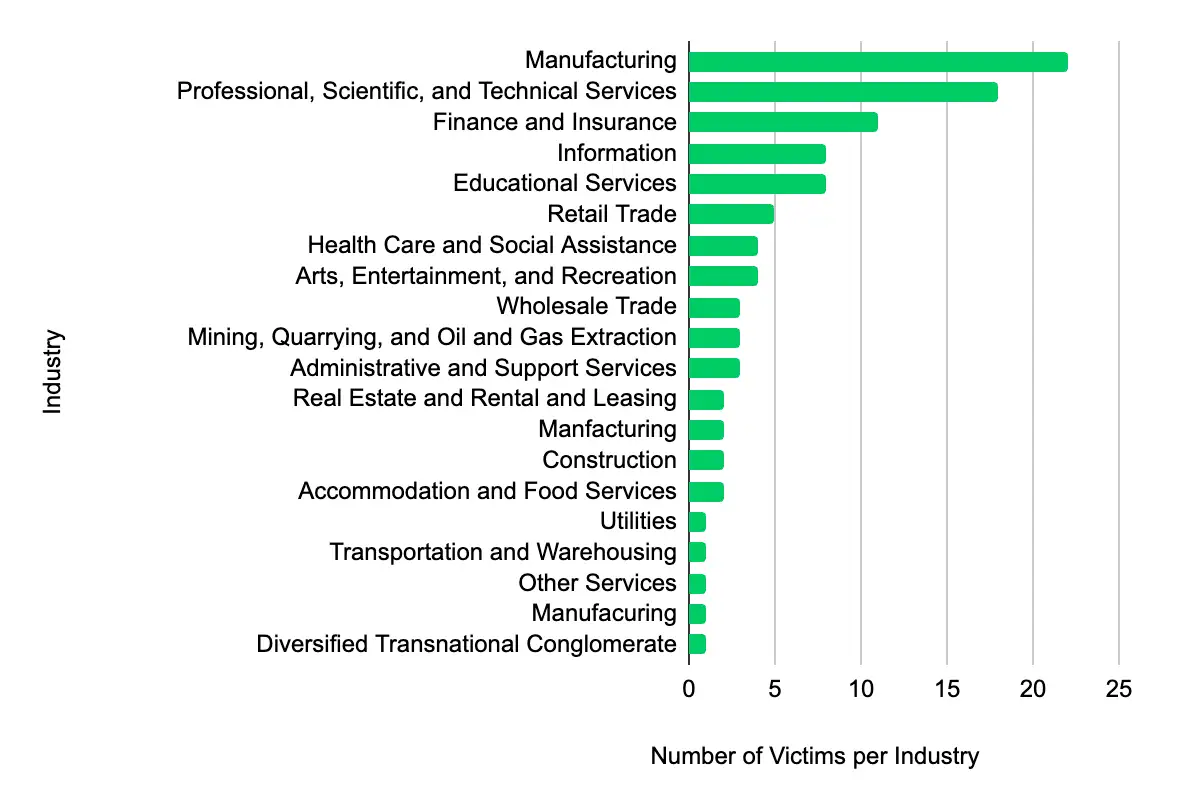
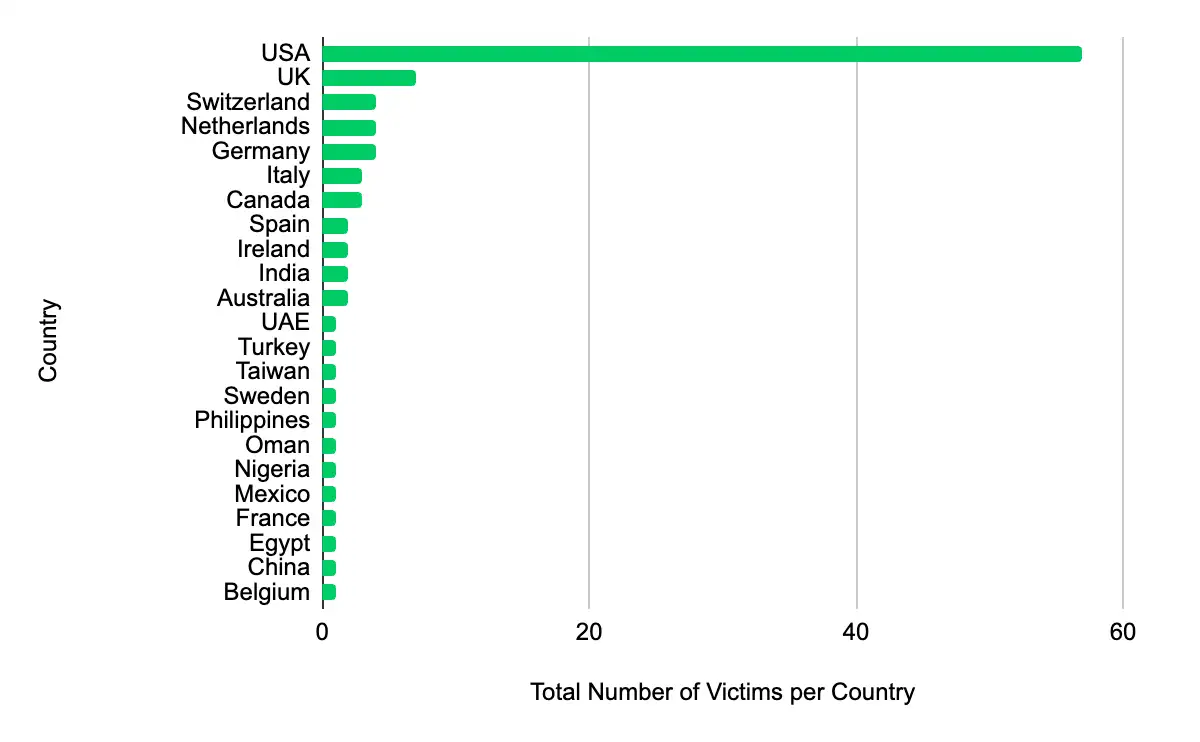
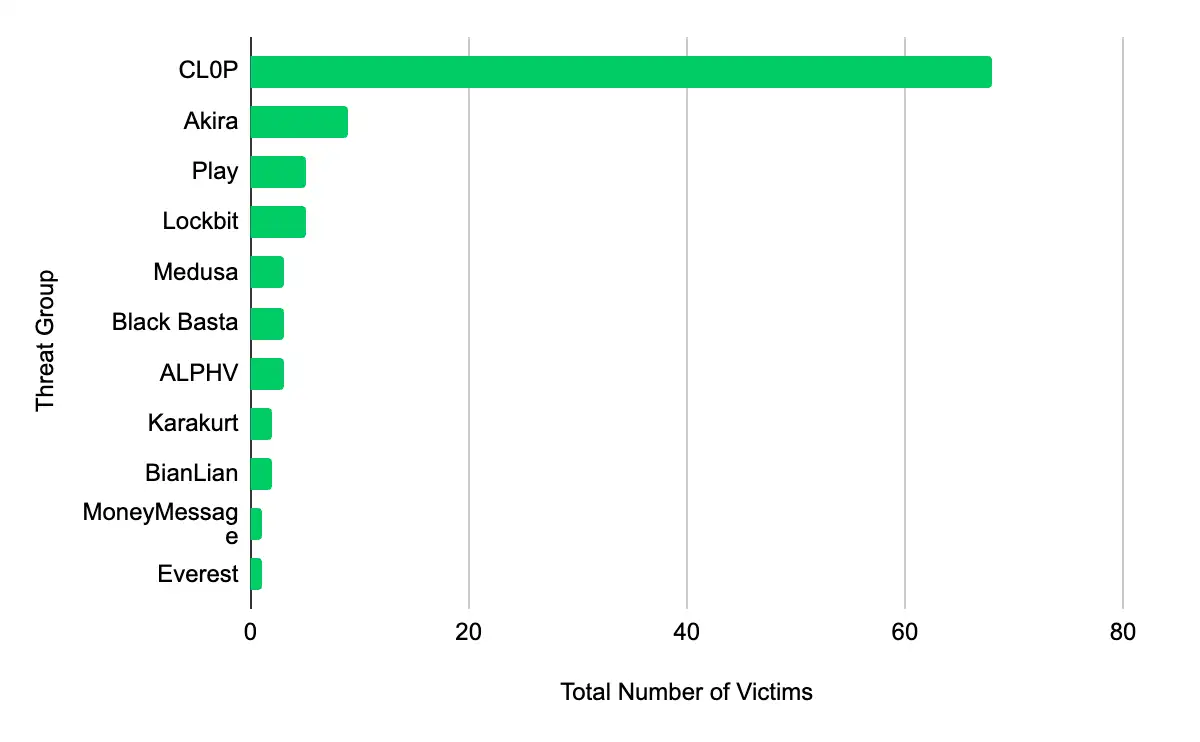
In the past week, monitored data extortion and ransomware threat groups added 102 victims to their leak sites. Of those listed, 57 are based in the US. The most popular industry listed was Manufacturing, with 22 victims. They were followed by 18 in Professional, Scientific, and Technical Services, 11 in Finance and Insurance, eight each in Information, and Educational Services. This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds 3 CVEs to its Known Exploited Vulnerabilities Catalog
Within the past week, CISA added three CVEs to its Known Exploited Vulnerabilities Catalog. These vulnerabilities affect vendors and projects from Ivanti, Zimbra, and Apple. The vulnerabilities allow for authentication bypass or cross-site scripting. The Common Vulnerabilities and Exposures (CVE) identifiers assigned to these vulnerabilities are CVE-2023-35081, CVE-2023-37580, and CVE-2023-38606. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with a CISA due date set between 16 August 2023 to 21 August 2023.
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share