Midnight Blizzards, BlueCharlies, STRRAT Rats and QakBot, Plus Surprising Research on Ransomware Victim Size
This week: Midnight Blizzard uses Microsoft Teams to phish organizations, Russian APT BlueCharlie alters domain name structure, RATS and Bots are on the rise, and turns out ransomware groups are more likely hitting small to medium businesses. In our latest Cyber Intelligence Brief, we look at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading MDR provider, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- Microsoft Threat Intelligence: Midnight Blizzard conducts targeted social engineering over Microsoft Teams
- Recorded Future: BlueCharlie, Previously Tracked as TAG-53, Continues to Deploy New Infrastructure in 2023
- Cyble: STRRAT’s Latest Version Incorporates Dual Obfuscation Layers
- Team Cymru: Visualizing Qakbot Infrastructure Part II: Uncharted Territory
- Guidepoint Security: Tunnel Vision: CloudflareD AbuseD in the WilD
- Proofpoint: Cloud Account Takeover Campaign Leveraging EvilProxy Targets Top-Level Executives at over 100 Global Organizations
- Latest Additions to Ransomware Data Leak Sites
- CISA Adds 2 CVEs to its Known Exploited Vulnerabilities Catalog
Midnight Blizzard Compromises Small-Business Microsoft 365 Tenants for Targeted Teams Phishing Campaign
Microsoft 365 Teams – Phishing – Passwordless – MFA Credential Theft – Cyber Espionage
According to Microsoft Threat Intelligence, Midnight Blizzard, a Russia-based threat actor attributed to the Foreign Intelligence Service of the Russian Federation (SVR), has conducted a targeted social engineering campaign using Microsoft Teams. The campaign involves compromising Microsoft 365 tenants owned by small businesses to create phishing lures, engaging users with multi factor authentication (MFA) prompts to steal credentials. We believe the threat poses a significant risk to targeted organizations and potentially the broader governmental landscape, with potential national security implications.
The likelihood that organizations were affected by Midnight Blizzard’s campaign is limited, primarily impacting 40 organizations globally, indicating a focused and deliberate approach. However, other threat actors could incorporate the techniques into their operations, targeting additional sectors. Using common platforms like Microsoft Teams and the Microsoft Authenticator app further increases the likelihood that a broad range of organizations could be susceptible to this threat. The threat actor’s objective and ability to compromise Microsoft 365 tenants owned by small businesses raise the risk for small businesses in future operations.
The impact of Midnight Blizzard’s campaign on the affected organizations was likely considerable, with potential national security implications. The threat actors accessed sensitive resources, including email, files, and contacts. This access can lead to intellectual property theft, personal information, and confidential business data. The potential addition of a device to the organization as a managed device could further enable lateral movement within the organization, possibly leading to more extensive breaches. Overall, the threat posed by Midnight Blizzard represents a significant risk to the targeted organizations and potentially the broader governmental landscape.
Russian APT Group Significantly Alters Domain Name Structure, Prefers NameCheap Registration
BlueCharlie Cyber – Espionage – Phishing & Credential Theft – NameCheap – Let’s Encrypt
Recorded Future issued a report about BlueCharlie, previously tracked as TAG-53, a Russia-linked threat group known for its persistent phishing and credential theft campaigns. Looks like these threat actors have significantly altered their domain name structure and shifted its preference to NameCheap registration, reflecting its highly adaptive nature and ability to evade detection.
BlueCharlie represents a significant and multifaceted risk to targeted regions and sectors, including NATO nations, Ukraine, government, higher education, defense, and political sectors. The group’s alignment with Russian state interests and its strategic focus on these areas demonstrate a well-coordinated state-sponsored threat.
BlueCharlie’s persistent campaigns and the creation of fraudulent profiles demonstrate a preferred approach to gathering intelligence. The risk here is twofold: the potential loss of sensitive information and the possibility of further exploitation based on the gathered intelligence. The impact could include intellectual property theft, strategic advantage loss, and considerable national security implications.
The group’s ability to evade detection and change tactics poses a risk to organizations relying on static defense measures, as BlueCharlie’s evolving tactics can bypass traditional security controls. The impact of this risk includes potential breaches and ongoing undetected infiltration.
BlueCharlie’s calculated approach to their infrastructure and security means their activity could blend in with legitimate traffic, making detection and mitigation more complex. The impact could include a delayed response to incidents and increased exposure to breaches.
BlueCharlie’s specific targeting focus underscores a broader geopolitical risk. The group’s activities may be part of a larger state-sponsored effort to influence, disrupt, or gain an advantage over targeted nations and sectors. The impact of this risk extends beyond cybersecurity, potentially affecting diplomatic relations, national security strategies, and regional stability.
Remote Access Trojan, STRRAT, Updated, Delivered in Phishing Email PDF Attachments
STRRAT – RAT – Phishing – JavaScript – ZIP File – JAR File
Developers of the Java-based Remote Access Trojan (RAT), STRRAT, have been busy. The RAT uses a new infection technique, initiated through a spam email containing a PDF file attachment, and employs two-string obfuscators to evade detection. STRRAT can execute a range of commands once connected to its Command and Control (C&C) server, posing a significant threat to organizations.
STRRAT now in version 1.6, has undergone modifications compared to previous variants. The class names, which were gibberish in prior variations, have been modified. The malware now utilizes two string obfuscators, “Allatori” and “Zelix KlassMaster (ZKM),” whereas the previous variants used only the “Allatori” obfuscator. The deobfuscation process involves two steps, first for “Zelix KlassMaster” and then for the “Allatori” obfuscator.
The infection process of STRRAT 1.6 initiates through a spam email disguised to appear as if it’s from an electronics-based company. The email contains a PDF file attachment, presented as an invoice. Upon opening the PDF, a download image is displayed, which, when clicked, downloads a zip file from a URL. The downloaded zip file contains a JavaScript file containing the encrypted STRRAT payload.
When executed, the JavaScript file decrypts the payload and drops a zip (JAR) file disguised as a “txt” file in the “\AppData\Roaming” directory. The deobfuscated JAR file contained a new version of STRRAT malware (version 1.6), which has been actively distributed since March 2023 through various infection chains. Over 70 samples of this version have been identified in the wild.
There is a moderate to high probability that organizations will be affected by the STRRAT malware, given the sophistication and continuous evolution of the threat. The malware has been actively distributed since March 2023, with over 70 samples of version 1.6 identified in the wild, suggesting an ongoing and active campaign. However, whether this is from one or multiple threat actors is unknown.
The impact of a STRRAT infection on an organization can be severe. The malware can steal sensitive information, which could lead to significant data breaches. The stolen information could include login credentials, email data, financial data, and other sensitive personal or corporate information. This could result in financial loss, reputational damage, and potential regulatory penalties for the affected organization. Moreover, STRRAT’s level of control over an infected system can disrupt business operations and further compromise the organization’s network.
QakBot Takes a Break, Updates Infrastructure with 15 New C2s, Expected to Resume Operations in September
QakBot – New C2s – Tiered Infrastructure
Looks like the developers of Qakbot are taking their usual summer break to refine and update their infrastructure. Team Cymru identified 15 new command and control (C2) servers this year. In their report, they highlight unusual outbound communication traffic from the Tier 2 (T2) servers to a large pool of IP addresses, including Tier 1 C2 servers.
Qakbot, also known as QBot or Pinkslipbot, is a Trojan active since 2007. Primarily spread through email hijacking and social engineering tactics. Operators often use malicious email attachments, links, or embedded images to access a victim’s machine. Once Qakbot is executed on a victim’s machine, it performs various actions such as profiling the system and the network, exfiltrating emails for later use in malware distribution campaigns, and establishing backdoors for unauthorized access.
Qakbot communicates with its command and control (C2) infrastructure through encoded messages sent via HTTPS GET and POST requests. Moreover, Oakbot can elevate infected machines to C2 servers, ensuring a continuous supply of C2s and updating its list of C2 servers as its infrastructure is identified and acted upon. This allows the operators to maintain a large and diverse pool of C2 servers, making it difficult for security solutions to block or take down the entire infrastructure.
The likelihood of organizations being affected by the QakBot threat is high, given the malware’s history and its operators showing adaptability and a willingness to target a broad range of industries. The malware’s sophisticated evasion techniques and its operators’ ongoing efforts to refine and update their infrastructure make it a persistent and pervasive threat.
The impact that organizations face from the QakBot threat is significant. If QakBot compromises an organization’s systems, the malware can steal sensitive data, including login credentials and sensitive information, leading to financial loss and reputational damage. Furthermore, QakBot’s ability to distribute other types of malware, such as ransomware, can lead to additional direct and indirect costs, including disrupting business operations and requiring significant resources to remediate. The outbound traffic from QakBot-infected machines could lead to an organization’s IP address being blacklisted, further disrupting business operations.
Threat Actors Leveraging Cloudflare Tunnel, Likely Adoption in Espionage and Ransomware Operations
Cloudflared – Data Exfiltration and Extortion – RDP/SMB – Private Network Access – Limited Artifacts
Recently, GuidePoint’s DFIR and GRIT teams responded to multiple engagements involving a relatively new, legitimate tool being used by threat actors: Cloudflare Tunnel, also known by its executable name, Cloudflared. Multiple threat actors have misused the Cloudflare Tunnel, also known as Cloudflared, to create outbound connections for malicious purposes. The tool is functionally similar to ngrok, is free, and threat actors can easily modify and immediately update tunnel configurations.
Threat actors could establish a foothold in a victim’s machine or access an entire CIDR range through the tunnel for data exfiltration. Moreover, threat actors can use the TryCloudflare feature to carry out malicious activities without leaving any attributable artifacts. Recommendations to counter this threat include blocking related domains, blocking outbound connections to port 7844, alerting or isolating unauthorized hosts executing Cloudflared-related commands, and establishing clear policies to prevent the execution of Cloudflare without manual approval.
The probability that threat actors will incorporate Cloudflare Tunnel in their operations is high. The blog post reveals that some TAs have already started using Cloudflare Tunnel, a legitimate tool, to further their exploitation efforts against target networks. The ease of tunnel establishment and management and the ability to quickly change the configuration make it an attractive option for threat actors.
The traffic generated by the Cloudflare Tunnel makes it challenging to detect by traditional anti-virus, EDR, and other defensive processes. Threat actors can use it to access important services like SSH, RDP, SMB, and more. TAs can easily modify the tunnel configuration, enabling or disabling functionality to prevent exposure of their infrastructure. This adaptability adds complexity to the defense. Cloudflare Tunnel also supports providing access to an entire CIDR range through the tunnel, allowing an actor to interact with any device in the private network as though they were physically collocated.
The ability of actors to cover their tracks and the lack of default logging on the tunnel server means that post-breach analysis is severely limited. The availability of a persistence mechanism and the capability to exfiltrate data enhances the threat it poses. While there are ways to monitor and detect unauthorized use of Cloudflared, such as DNS queries and non-standard port monitoring, the tool’s broad use cases and control by the tunnel administrator make defense challenging.
Threat Actors Use EvilProxy to Send 120,000 Phishing Emails
Account Compromise – MFA Bypass – Phishing – C-Level Executives – Phishing Kit
A cloud account takeover campaign between March and June 2023, leveraging the EvilProxy phishing kit, has targeted top-level executives at over 100 global organizations. It’s believed the threat actors sent around 120,000 phishing emails to high-value individuals, including C-level executives, employing complex redirection chains and impersonating trusted services.
EvilProxy is a phishing-as-a-service (PhaaS) toolkit that can bypass two-factor authentication (2FA) protections employed by online services. It was first mentioned in early May 2022 when the actors behind it released a demonstration video showcasing its capabilities. The toolkit is designed to generate phishing links that mimic the login pages of popular brands and services. Using a reverse proxy, EvilProxy leads targets to these cloned pages allowing the actors to intercept the traffic and harvest valid session cookies and bypassing the need for authentication credentials or 2FA tokens. The toolkit’s subscription-based pricing model offers different durations for accessing the kit.
It’s reasonable to expect high-value individuals (C-Level executives and managers) will receive phishing emails associated with this campaign in the coming months. The campaign’s spread has been impressive, with approximately 120,000 phishing emails sent to approximately 100 organizations across the globe between March and June 2023. The actors’ redirection chain was complex, and they employed automation to identify high-level targets and gain immediate access to accounts. The use of open-source kits and MFA Phishing as a Service (PhaaS) has made the process accessible to actors of varying technical skills, further increasing the likelihood of organizations being affected.
The impact of this threat on organizations is severe, particularly for those with high-level executives who may have access to sensitive data. The actors have focused on “VIP” targets, including C-level executives, CFOs, Presidents, and CEOs. The consequences include financial fraud, data exfiltration and extortion, and unauthorized access to sensitive resources within the organization’s cloud environment. The actors’ ability to study target organizations’ culture, hierarchy, and processes to prepare their campaigns further amplifies the potential impact. The threat’s sophistication makes it a potent and concerning risk, with the potential for significant financial and reputational damage.
The Latest from Ransomware Data Leak Sites
Professional, Scientific, and Technical Services – Manufacturing – Construction – Wholesale Trade – Educational Services – Ransomware
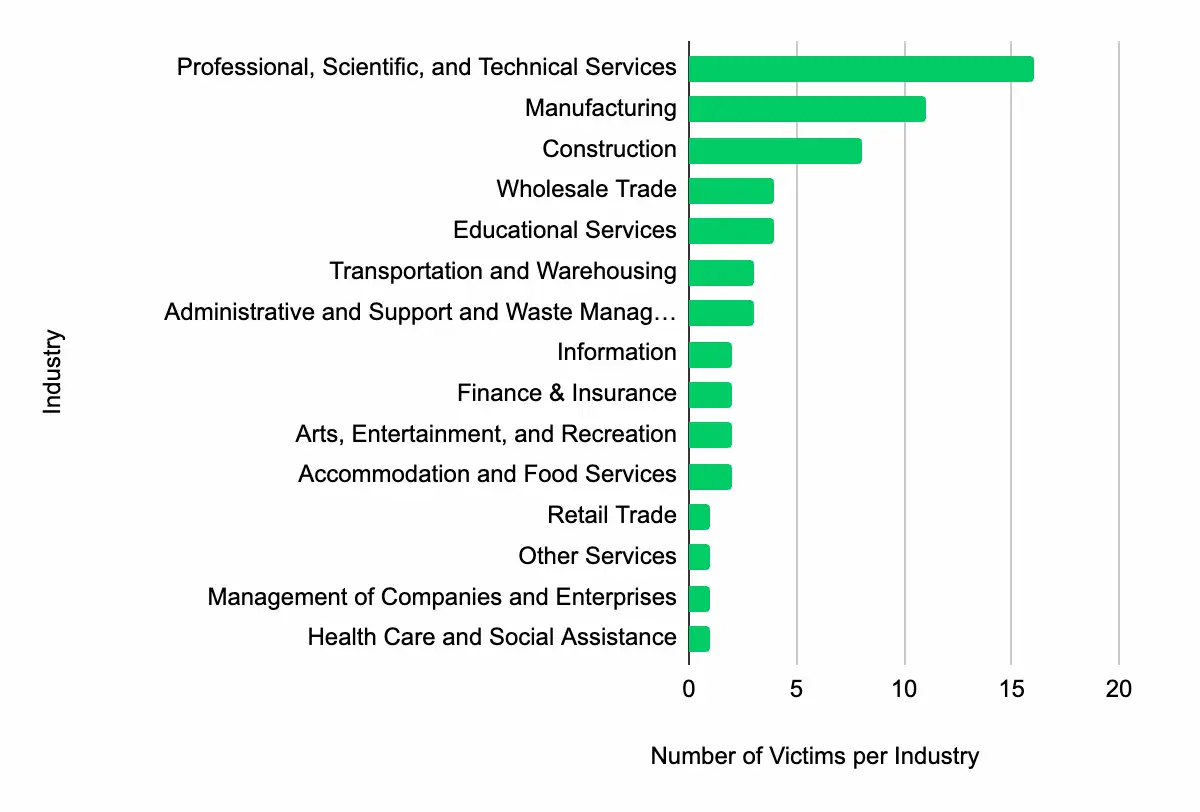
ATI analyzes the latest additions to dark web data leak sites, providing timely information for decision-makers. In the past week, ransomware threat groups added 61 victims to these sites, with 35 based in the US. The most targeted industry was Professional, Scientific, and Technical Services, with 16 victims, followed by Manufacturing, Construction, Wholesale Trade, and Educational Services. It is important to note that while these victims are listed, we cannot confirm the validity of the cybercriminals’ claims.
| Threat Actor | Target Organization | Country | Industry |
|---|---|---|---|
| Akira | BWSC | Denmark | Professional, Scientific, and Technical Services |
| Akira | Datawatch Systems | USA | Professional, Scientific, and Technical Services |
| Akira | Don’s Mobile Glass | USA | Construction |
| Akira | Guido Companies | USA | Construction |
| Akira | KNP Logistics Group | UK | Transportation and Warehousing |
| Akira | Koury Engineering | USA | Professional, Scientific, and Technical Services |
| Akira | Murphy Plywood | USA | Manufacturing |
| Akira | Optical Cable Corporation | USA | Manufacturing |
| Akira | Parathon | USA | Professional, Scientific, and Technical Services |
| Akira | Tennis Canada | Canada | Arts, Entertainment, and Recreation |
| Akira | TGRWA | USA | Professional, Scientific, and Technical Services |
| Akira | Ultimus | USA | Professional, Scientific, and Technical Services |
| Akira | Venture General Agency | USA | Finance & Insurance |
| ALPHV | G24 News | Spain | Information |
| ALPHV | Grupo Garza Ponce | Mexico | Construction |
| ALPHV | Henderson Franklin Attorneys at Law | USA | Professional, Scientific, and Technical Services |
| ALPHV | IBL Group | Mauritius | Management of Companies and Enterprises |
| ALPHV | KIMCO Staffing Service | USA | Administrative and Support and Waste Management and Remediation Services |
| ALPHV | Ofimedic Medical Software | Spain | Information |
| ALPHV | Pharmatech Republica Dominicana | Dominican Republic | Wholesale Trade |
| ALPHV | Premier BPO | USA | Administrative and Support and Waste Management and Remediation Services |
| ALPHV | Rayden Solicitors | UK | Professional, Scientific, and Technical Services |
| ALPHV | Riggs Abney | USA | Professional, Scientific, and Technical Services |
| ALPHV | SBS Construction | USA | Construction |
| ALPHV | Tempur Sealy International | USA | Manufacturing |
| ALPHV | The Change Organisation | UK | Wholesale Trade |
| Bianlian | Carvin Software | USA | Professional, Scientific, and Technical Services |
| Bianlian | Spokane Spinal Sports Care Clinic | USA | Health Care and Social Assistance |
| CL)P | Sherman College of Chiropractic | USA | Educational Services |
| Karakurt | COSI (Center of Science and Industry) | USA | Arts, Entertainment, and Recreation |
| Lockbit | Al Doha Maintenance & Services Centre (ADMSC) | Qatar | Construction |
| Lockbit | Armortex | USA | Manufacturing |
| Lockbit | ATSER | USA | Professional, Scientific, and Technical Services |
| Lockbit | Best Motel | Germany | Accommodation and Food Services |
| Lockbit | Construction CRD | Canada | Construction |
| Lockbit | Federal Electric Corp | Thailand | Manufacturing |
| Lockbit | Flood Law PLLC | USA | Professional, Scientific, and Technical Services |
| Lockbit | GERB Political Party (Citizens for European Development of Bulgaria) | Bulgaria | Other Services |
| Lockbit | IQ Corporation (IQC) | USA | Manufacturing |
| Lockbit | Llombart Handels- und Treuhandgesellschaft mbH | Germany | Wholesale Trade |
| Lockbit | Mission Petroleum Carriers | USA | Transportation and Warehousing |
| Lockbit | National Board for Certified Counselors | USA | Educational Services |
| Lockbit | Obrelli Jewelry | Italian | Retail Trade |
| Lockbit | Pareto Phone | Australia | Administrative and Support and Waste Management and Remediation Services |
| Lockbit | Persinger & Persinger, L.C. | USA | Professional, Scientific, and Technical Services |
| Lockbit | Point Pleasant School District | USA | Educational Services |
| Lockbit | SCOTTeVEST | USA | Manufacturing |
| Lockbit | TETCO, Inc. | USA | Transportation and Warehousing |
| Lockbit | Unicorp National Developments | USA | Construction |
| Lockbit | West Oaks School | UK | Educational Services |
| Mallox | Kogetsu | Japan | Manufacturing |
| Play | Aapd | Australia | Wholesale Trade |
| Play | ACTIVA Group | Cameroon | Finance & Insurance |
| Play | Aquatlantis | Portugal | Manufacturing |
| Play | Birch, Horton, Bittner & Cherot | USA | Professional, Scientific, and Technical Services |
| Play | Coral Resort | USA | Accommodation and Food Services |
| Play | DAL-TECH Engineering | USA | Professional, Scientific, and Technical Services |
| Play | Garage Living | Canada | Construction |
| Play | The Dispenser USA | Canada | Manufacturing |
| Play | evs professionnel France | France | Professional, Scientific, and Technical Services |
| Ragnar | Batesville Tool & Die, Inc | USA | Manufacturing |
CISA Adds 2 CVEs to its Known Exploited Vulnerabilities Catalog
Microsoft/CVE-2023-38180 – Zyxel/CVE-2017-18368
Within the past week, CISA added two CVEs to its Known Exploited Vulnerabilities Catalog. These vulnerabilities affect products from Microsoft and Zyxel. The vulnerabilities allow for denial of service and command injection. The Common Vulnerabilities and Exposures (CVE) identifiers assigned to these vulnerabilities are CVE-2023-38180 and CVE-2017-18368. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with a CISA due date set between 28 August 2023 to 30 August 2023.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date |
|---|---|---|---|---|
| CVE-2023-38180 | Microsoft | .NET Core and Visual Studio | Microsoft .NET Core and Visual Studio contain an unspecified vulnerability that allows for denial of service. | 8/30/23 |
| CVE-2017-18368 | Zyxel | P660HN-T1A Routers | Zyxel P660HN-T1A routers contain a command injection vulnerability in the Remote System Log forwarding function, which is accessible by an unauthenticated user and exploited via the remote_host parameter of the ViewLog.asp page. | 8/28/23 |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share