Golden Chickens Unleash New Malware, Scattered Spider Threats Persist, and New Vulnerabilities Added to CISA’s Catalog Amid Rising Ransomware Trends
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Golden Chickens Hatch New Threats: Unveiling TerraStealerV2 and TerraLogger
- Guarding Against Scattered Spider: Strengthening Cyber Defenses Against UNC3944
- Ransomware and Data Extortion Trends (Apr. 28 – May 4)
- Exploited Vulnerabilities in Apache, SonicWall, Commvault, Yiiframework, Langflow, FreeType and GeoVision Products Added to CISA’s Catalog
Golden Chickens Hatch New Threats: Unveiling TerraStealerV2 and TerraLogger
The Rundown
In early 2025, cybersecurity researchers at Recorded Future’s Insikt Group identified two emerging malware families—TerraStealerV2 and TerraLogger—linked to the financially motivated threat actor known as Golden Chickens (also referred to as Venom Spider). Golden Chickens operates a Malware-as-a-Service (MaaS) platform utilized by various cybercriminal groups. TerraStealerV2 is designed to collect browser credentials, cryptocurrency wallet data, and browser extension information, while TerraLogger functions solely as a standalone keylogger module.
TerraStealerV2 targets browser-stored credentials and cryptocurrency wallets, exfiltrating data via platforms like Telegram and the domain wetransfers[.]io. However, it lacks the capability to decrypt Chrome’s Application Bound Encryption (ABE)-protected credentials, indicating that the tool is likely outdated or still under development. Distribution methods observed between January and March 2025 include various formats such as MSI, DLL, and LNK files, leveraging trusted Windows utilities like regsvr32.exe and mshta.exe to evade detection.
TerraLogger represents the first observed use of a keylogging capability within malware developed by Golden Chickens. It employs a common low-level keyboard hook to record keystrokes and writes the logs to local files, but does not include functionality for data exfiltration or command-and-control communication, suggesting it is either in early development or intended to be a modular part of the Golden Chickens MaaS ecosystem. The current state of both TerraStealerV2 and TerraLogger suggests that these tools remain under active development and do not yet exhibit the level of stealth typically associated with mature Golden Chickens tooling.
Source Material: Recorded Future
Guarding Against Scattered Spider: Strengthening Cyber Defenses Against UNC3944
The Rundown
UNC3944, also known as Scattered Spider, is a cybercriminal group that has gained notoriety for targeting large companies across industries through social engineering and identity-based attacks. Originally focusing on SIM swap fraud within the telecommunications sector, the group evolved in early 2023 to conduct more aggressive ransomware and data extortion campaigns. Their victims include major brands in sectors like retail, finance, gaming, and hospitality, with a notable focus on English-speaking countries. Despite recent law enforcement crackdowns, the group’s connections to a broader cybercrime community suggest they could rebound and continue posing a threat.
A key tactic of UNC3944 involves tricking help desk staff into resetting credentials or bypassing security measures, often by impersonating real employees. This highlights a critical vulnerability in many organizations, reliance on basic verification processes and outdated multifactor authentication (MFA) methods like SMS or email. Once inside, the attackers escalate privileges and access sensitive data or systems, often deploying ransomware for financial gain. In some cases, they seek attention and recognition by targeting high-profile brands.
To help organizations stay ahead of this evolving threat, Google Cloud recommends several proactive defenses. These include improving identity verification processes, adopting strong, phishing-resistant MFA solutions, restricting access based on trusted devices and locations, and ensuring endpoint security tools are active and properly configured. Training support staff to recognize social engineering attempts is also crucial. By hardening these entry points, businesses can significantly reduce the risk of compromise and improve their resilience against sophisticated attackers like UNC3944.
Source Material: Google Mandiant
Ransomware and Data Extortion Trends (Apr. 28 – May 4)
The Rundown
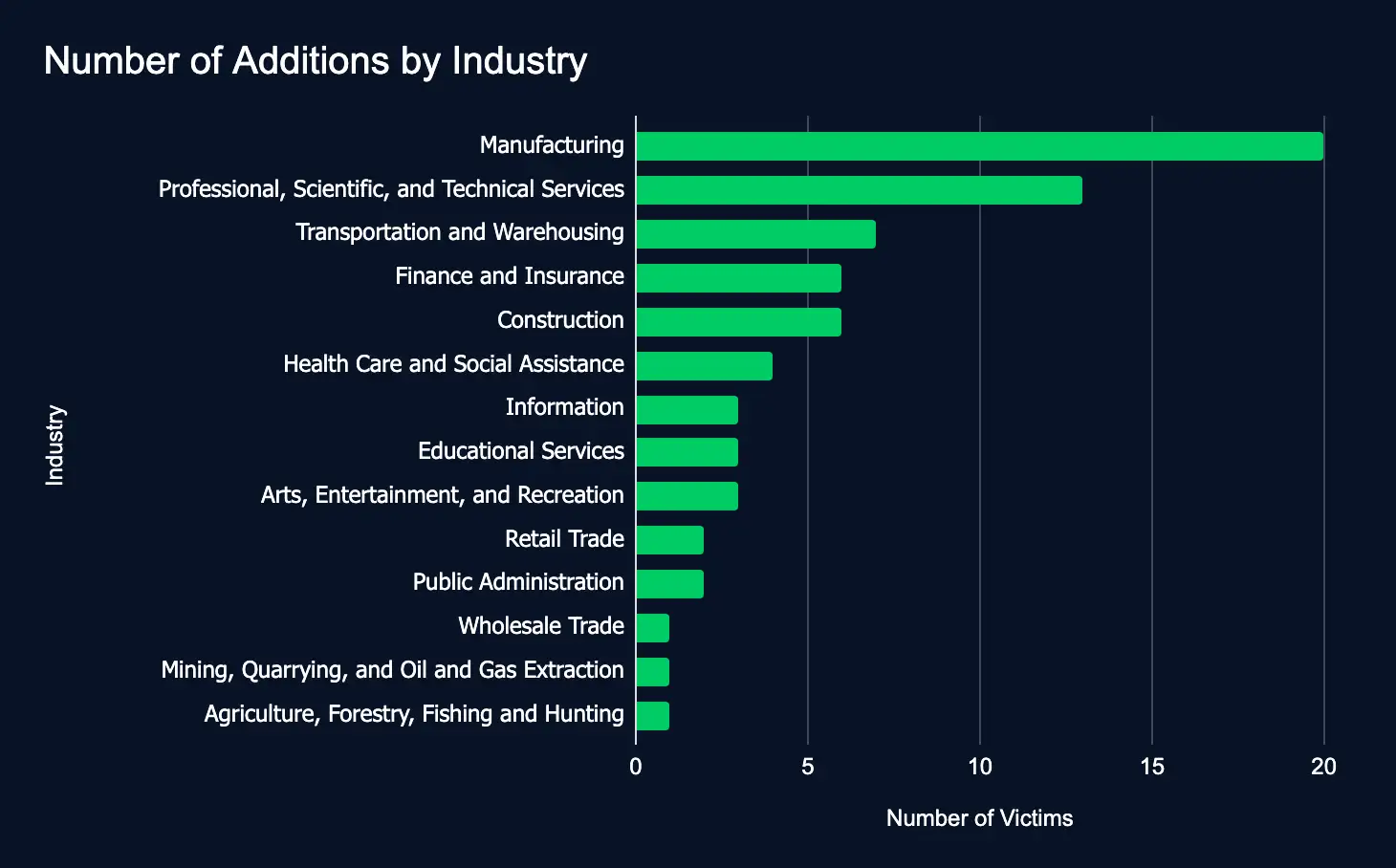
Ransomware and data extortion activity includes a slight decrease between April 28 – May 4, with a 12% decrease in listed organizations compared to the previous week.
During the reporting period, 72 organizations spanning 14 industries were listed on 15 ransomware and data extortion leak sites—a slight decrease from the 82 victims observed the previous week.
This decline in listings should not be viewed as a reduced threat. Instead, it likely reflects a tactical pivot by threat actors toward more selective, high-impact targets and refined attack methodologies. Security teams should interpret this shift as a signal to continuously adapt detection, response, and hardening strategies, ensuring they are aligned with the increasing precision and persistence of ransomware operations.
Key Trends:
- Most affected industries:
- Manufacturing
- Professional, Scientific, and Technical Services
- Transportation and Warehousing
- Most affected countries:
- United States
- Canada
- Italy
- Most active leak sites:
- Qilin
- Play
- Akira
SonicWall, Commvault, Yiiframework, Langflow, FreeType, and GeoVision Products Added to CISA’s Catalog
The Rundown
Between May 1st and 7th, eight critical vulnerabilities impacting products from Apache, SonicWall, Commvault, Yii Framework, Langflow, FreeType, and GeoVision were added to CISA’s Known Exploited Vulnerabilities (KEV) catalog. If not promptly addressed, these flaws could expose organizations to significant cyber threats.
Given the widespread use of the affected technologies, these vulnerabilities pose serious risks to operational security. With a heightened likelihood of exploitation by both state-sponsored and criminal threat actors, accelerated remediation is essential to maintain resilience and safeguard critical infrastructure.
Apache | HTTP Server CVE-2024-38475
- Vulnerability Description: Apache HTTP Server contains an improper escaping of output vulnerability in mod_rewrite that allows an attacker to map URLs to filesystem locations that are permitted to be served by the server but are not intentionally/directly reachable by any URL, resulting in code execution or source code disclosure.
- Exploitation Details: The vulnerability arises from improper escaping of output in mod_rewrite. When substitutions in server context use backreferences or variables as the first segment, it can lead to incorrect mapping of URLs to filesystem paths. By crafting specific HTTP requests, attackers can exploit this flaw to access files that are permitted to be served by the server but are not intentionally or directly reachable by any URL.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-01
- Recommended Mitigation Due Date: 2025-05-22
SonicWall | SMA100 Appliances CVE-2023-44221
- Vulnerability Description: SonicWall SMA100 appliances contain an OS command injection vulnerability in the SSL-VPN management interface that allows a remote, authenticated attacker with administrative privilege to inject arbitrary commands as a ‘nobody’ user.
- Exploitation Details: In real-world attacks, threat actors have combined CVE-2023-44221 with CVE-2024-38475, a separate vulnerability in the Apache HTTP Server’s mod_rewrite module used by SMA appliances. This combination allows attackers to bypass authentication, extract session tokens, and execute commands, effectively gaining administrative control over the device.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-01
- Recommended Mitigation Due Date: 2025-05-22
Commvault | Command Center CVE-2025-34028
- Vulnerability Description: Commvault Command Center contains a path traversal vulnerability that allows a remote, unauthenticated attacker to execute arbitrary code.
- Exploitation Details:The vulnerability exists in the deployWebpackage.do endpoint of the Commvault Command Center, where improper input validation allows unauthenticated attackers to exploit the system. By uploading a specially crafted ZIP archive containing a web shell, an attacker can perform directory traversal, enabling the placement of the malicious file in a location accessible via the web interface. This ultimately leads to remote code execution on the affected system.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-02
- Recommended Mitigation Due Date: 2025-05-23
Yiiframework | Yii CVE-2024-58136
- Vulnerability Description: Yii Framework contains an improper protection of alternate path vulnerability that may allow a remote attacker to execute arbitrary code. This vulnerability could affect other products that implement Yii, including—but not limited to—Craft CMS, as represented by CVE-2025-32432.
- Exploitation Details: The vulnerability stems from the Yii framework’s mishandling of behavior attachments specified through the __class array key. Attackers can exploit this flaw by sending specially crafted JSON payloads that manipulate the behavior attachment process. This manipulation can lead to unauthorized code execution within the application context.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-02
- Recommended Mitigation Due Date: 2025-05-23
Langflow CVE-2025-3248
- Vulnerability Description: Langflow contains a missing authentication vulnerability in the /api/v1/validate/code endpoint that allows a remote, unauthenticated attacker to execute arbitrary code via crafted HTTP requests.
- Exploitation Details: The flaw arises from the /api/v1/validate/code endpoint, which processes user-submitted code using Python’s exec() function without proper authentication or sandboxing. This endpoint is intended to validate code snippets but fails to securely handle untrusted input.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-05
- Recommended Mitigation Due Date: 2025-05-26
FreeType CVE-2025-27363
- Vulnerability Description: FreeType contains an out-of-bounds write vulnerability when attempting to parse font subglyph structures related to TrueType GX and variable font files that may allow for arbitrary code execution.
- Exploitation Details: Attackers can exploit this vulnerability by crafting malicious font files that, when processed by FreeType, trigger the out-of-bounds write condition. This can lead to the execution of arbitrary code on the affected system. Notably, the exploitation does not require user interaction, making it suitable for zero-click attacks.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-06
- Recommended Mitigation Due Date: 2025-05-27
GeoVision | Multiple Devices CVE-2024-6047 & CVE-2024-11120
- Vulnerability Description: Multiple GeoVision devices contain an OS command injection vulnerability that allows a remote, unauthenticated attacker to inject and execute arbitrary system commands.
- Exploitation Details: The vulnerability resides in the /DateSetting.cgi endpoint of the affected devices. Specifically, the szSrvIpAddr parameter fails to properly sanitize user input, allowing attackers to inject malicious commands.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-05-07
- Recommended Mitigation Due Date: 2025-05-28
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share