APTs Exploit Vulnerabilities in Zoho ManageEngine and FortiOS, Phishing Kit W3LL Lies Deep in Global Microsoft 365 BEC Campaigns, and a Linux Supply Chain Attack Goes Undetected for More than 3 Years.
This week: Multiple APT actors exploit vulnerabilities in Zoho ManageEngine and FortiOS SSL-VPN, phishing kit W3LL compromises as many as 8,000 accounts in a global Microsoft 365 BEC campaign, a zero-day exploits Cisco ASA and FTD to deliver ransomware, and sophisticated threat actors leverage a supply chain attack targeting Linux systems—for over three years.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- CISA: Multiple Nation-State Threat Actors Exploit CVE-2022-47966 and CVE-2022-42475
- Group-IB: W3LL Done: Hidden Phishing Ecosystem Driving BEC Attacks
- Cisco: Cisco Adaptive Security Appliance Software and Firepower Threat Defense Software Remote Access VPN Unauthorized Access Vulnerability
- Cisco: Akira Ransomware Targeting VPNs without Multi-Factor Authentication
- Rapid7: Under Siege: Rapid7-Observed Exploitation of Cisco ASA SSL VPNs
- Fortinet: OriginBotnet Spreads via Malicious Word Document
- Microsoft: Malware distributor Storm-0324 facilitates ransomware access
- Securelist by Kaspersky: Free Download Manager backdoored – a possible supply chain attack on Linux machines
- The Latest Additions from Data Leak Sites
- CISA Adds 2 CVEs to its Known Exploited Vulnerabilities Catalog
Multiple APT Actors Exploited Vulnerabilities in Zoho ManageEngine and FortiOS SSL-VPN to Gain Unauthorized Access
Zoho ManageEngine/CVE-2022-47966 – FortiOS SSL-VPN CVE-2022-42475 – Multiple Tools – Professional, Scientific, and Technical Services – Manufacturing – Transportation and Warehousing
In a recent advisory, CISA detailed an intrusion orchestrated by multiple APT actors exploiting critical vulnerabilities in Zoho ManageEngine and FortiOS SSL-VPN to gain unauthorized access to sensitive systems and data of an organization in the aeronautics sector. The actors demonstrated high skill and resource availability, utilizing numerous tools to facilitate activities such as credential harvesting and establishing secure channels for remote control.
The Cybersecurity and Infrastructure Security Agency’s (CISA) joint Cybersecurity Advisory details an intricate and sophisticated operation orchestrated by multiple APT actors in early 2023 against an organization in the aeronautics sector. The advisory provides a detailed timeline of events and an analysis of the tactics, techniques, and procedures (TTPs) employed. The scope of their report encompasses artifacts discovered during the investigation. By releasing the joint Cybersecurity Advisory, they aim to provide network defenders with tactics, techniques, and procedures (TTPs), IOCs, and methods to detect and protect against similar exploitation.
The threat actors leveraged two critical vulnerabilities, one in Zoho ManageEngine (CVE-2022-47966) and the other in FortiOS SSL-VPN (CVE-2022-42475), as initial access vectors. Zoho ManageEngine devices vulnerable to CVE-2022-47966 contain an unauthenticated, remote code execution vulnerability due to using an outdated third-party dependency, Apache Santuario. FortiOS SSL-VPN devices vulnerable to CVE-2022-42475 have a heap-based buffer overflow vulnerability, allowing an unauthenticated, remote attacker to execute arbitrary code or commands via specifically crafted requests.
Threat Analysis
Multiple APT actors exploited two critical vulnerabilities, CVE-2022-47966 and CVE-2022-42475, to gain unauthorized access to sensitive systems and data. CISAs analysis confirmed that a nation-state advanced persistent threat (APT) actor exploited CVE-2022-47966 to gain initial access. The APT actors leveraged this vulnerability to execute various malicious activities, including creating local user accounts with administrative privileges, downloading malware, enumerating the network, collecting administrative user credentials, and moving laterally through the organization’s network.
CISA also identified additional APT actors who exploited CVE-2022-42475 to establish a presence on the organization’s firewall device. This activity involved the use of disabled administrative account credentials and the deletion of logs, preventing CISA from identifying follow-on exploitation or data exfiltration. However, the actors initiated multiple Transport Layer Security (TLS)-encrypted sessions on TCP port 10443, indicating successful exchanges of data transfer from the firewall device. CISA also identified the actors leveraging legitimate credentials to move from the firewall to a web server, where multiple web shells were loaded—among other locations.
During the operation, the APT actors utilized a range of tools, including Mimikatz, Ngrok, ProcDump, Metasploit, Interact.sh, anydesk.exe, quser.exe, and xpack.exe. These tools were instrumental in furthering their objectives, aiding in activities such as credential harvesting, establishing secure channels for remote control, and executing malicious payloads, among other functions.
The intentions behind these separate operations appear to be intelligence collection. However, a potential financial motivation can not be ruled out. The well-orchestrated effort to access, exfiltrate, and potentially disrupt or destroy sensitive data poses a significant threat to organizational security and integrity. This meticulous planning and execution are mirrored in the APT actors’ objectives, which were focused on targeting systems that housed critical and sensitive data. The strategic exploitation of vulnerabilities facilitated unauthorized access to a wealth of information, setting the stage for a potential data breach with far-reaching implications and indicating an intention to leverage the acquired data for further malicious activity or sale in the cybercriminal marketplaces. The actors’ activities showcase their high skill and resource availability. Leveraging a diverse set of sophisticated TTPs and tools, and exploiting critical vulnerabilities highlights their advanced capabilities and suggests a backing of substantial resources and expertise.
Risk & Impact Assessment
The risk posed by the exploitation of CVE-2022-47966 and CVE-2022-42475 is substantial, given the APT actors’ meticulous approach to targeting systems housing critical and sensitive data. The likelihood of incidents occurring is heightened due to the vulnerabilities affecting widely used platforms, potentially resulting in a significant compromise of confidentiality, integrity, and availability of data or information systems. The impact of such exploitations is profound, with organizations standing to suffer extensive damage from unauthorized systems or data access, including the exfiltration of sensitive information. The potential modification of data, coupled with the disruption of operations and information systems, not only threatens the destruction or loss of data and information systems but also poses a substantial threat to the corporate assets and operational continuity of organizations.
W3LL Phishing Kit Facilitates Global Microsoft 365 BEC Campaigns, Compromising at Least 8,000 Accounts
W3LL Phishing Kit – Microsoft 365 – W3LL Store – Manufacturing – Information – Finance and Insurance
Researchers unveil the sophisticated operations of the W3LL phishing suite, a significant facilitator of global business email compromise (BEC) campaigns primarily targeting the manufacturing, information, and finance and insurance sectors. Orchestrated through the hidden underground marketplace known as the W3LL Store, the suite leverages various custom tools that bypass Multi-Factor Authentication (MFA) to infiltrate corporate Microsoft 365 accounts globally.
Group-IBs report titled “W3LL Done: Hidden Phishing Ecosystem Driving BEC Attacks” is a comprehensive threat report that unveils the operations of a previously underexplored threat actor known as W3LL. The report outlines the sophisticated phishing ecosystem fostered by W3LL, emphasizing its tools and the underground marketplace, W3LL Store, which facilitates a closed community of phishers. The report offers insights into the phishing campaigns orchestrated using W3LL tools, the functionalities of the W3LL Panel phishing kit, and the dynamics of the W3LL Store. Moreover, it presents a detailed analysis of the victims targeted, predominantly in the US and sectors like manufacturing and IT, and the substantial financial repercussions of these campaigns. The report is a vital tool for corporate security teams, offering a list of indicators of compromise (IoCs) and YARA rules to aid in detecting and preventing BEC attempts involving W3LL tools.
Since its inception in 2017, W3LL has cultivated a private ecosystem of potent phishing tools, central to which is the W3LL Store, an underground marketplace home to a closed community of English-speaking threat actors engaged in business email compromise (BEC) operations. The store offers a plethora of tools and resources vital for phishing endeavors. A significant asset in W3LL’s toolkit is the W3LL Panel OV6, a premier Adversary-in-the-Middle (AitM) phishing kit designed to bypass Multi-Factor Authentication (MFA) and infiltrate corporate Microsoft 365 accounts worldwide. Between October 2022 and July 2023, approximately 500 threat actors utilized W3LL tools in BEC campaigns, targeting over 56,000 accounts and successfully compromising at least 8,000.
Threat Analysis
W3LL has orchestrated a sophisticated suite of tools to facilitate business email compromise (BEC) phishing campaigns. The suite is built around a pipeline of primary tools, each serving a distinct function when conducting a phishing campaign. The SMTP senders, namely “Punny Sender” and “W3LL Sender,” are responsible for bulk email spam, offering features such as Punycode-based email header obfuscation and dynamic phishing email templates. The “W3LL Redirect” tool is designed to generate initial phishing links and is equipped with functionalities like URL formatting customization and GeoIP filtering rules to protect phishing pages from detection. The centerpiece of this toolkit is the “W3LL Panel OV6,” an advanced Adversary-in-the-Middle (AitM) phishing kit specifically crafted to compromise corporate Microsoft 365 accounts, boasting features such as session cookie hijacking and victim account data retrieval. Lastly, the “CONTOOL” facilitates automated account discovery, monitoring, and data exfiltration, leveraging the Microsoft Graph API to extract data from Microsoft 365 accounts.
The W3LL Store stands as a hidden underground marketplace, a hub where criminals can find managed phishing solutions, including but not limited to compromised email accounts, victim email lists, and custom phishing lures. This marketplace serves as a trading ground and offers tool management capabilities, acting as the backend for W3LL’s API-based instruments. Over the last ten months, it has generated an estimated turnover of around $500,000, indicating a thriving criminal business.
To initiate their phishing campaigns, threat actors must first invest in acquiring the W3LL Panel and associated tools, which come with a structured pricing model. The W3LL Panel, central to orchestrating phishing campaigns, has a buy-in cost of $500 for a three-month subscription, with a monthly renewal fee of $150. This panel operates on a license-based activation mechanism, requiring buyers to authenticate each deployed phishing page on the W3LL Store using a unique generated token. This strategy prevents unauthorized resale and maintains control over the distribution of the kit. In addition to the panel, threat actors can invest in various tools to enhance their campaigns’ efficiency. The costs for these tools vary from $50 to $350 per month, with some requiring a buy-in fee.
If a threat actor opts to purchase every tool available, they will have to make an initial investment of roughly $1,000, followed by significant monthly renewal fees (approximately $2,000) to maintain access to these tools. Additionally, the W3LL Store offers many items necessary for running a phishing campaign, including compromised web services, SMTP servers, lists of credentials, and much more.
In orchestrating phishing campaigns, W3LL threat actors follow a structured process encompassing several phases, each involving specific tools and techniques to ensure the success of their BEC operations. In the preparation phase, threat actors obtain a list of potential victims by purchasing ready-to-use lists from the W3LL Store or manually harvesting and refining email addresses using Microsoft 365 email validator and refiner tools developed by W3LL. They also acquire the necessary malicious tools from the W3LL Store.
Phishing emails are then sent to targets, facilitated through W3LL SMTP senders with default phishing lures. However, threat actors can procure custom phishing lures from the W3LL Store to make their campaigns more targeted and persuasive. W3LL threat actors use a multi-stage process to set up malicious links. The aim is to lead victims through a chain of redirecting resources, making it difficult to detect and block W3LL Panel phishing pages. The actors employ various tactics, such as exploiting websites with open redirect vulnerabilities, using private link stager tools like W3LL Redirect, or exploiting legitimate services.
Compromising accounts involves a complex process handled by the W3LL Panel. All the threat actor has to do is obtain the results from the admin panel or one of several other exfiltration sources. The process can involve several steps:
- CAPTCHA verification, typically a Google CAPTCHA page or a fake Microsoft 365 login page.
- Displaying a legitimate-looking Microsoft 365 login page.
- Validating the victim’s Microsoft 365 account by sending a request to the Microsoft server.
- Retrieves three authenticated session cookies and sends these cookies to the backend (W3LL Store).
- Identifies the account type by making a request to the Microsoft server to retrieve information about the account itself and its type.
- Validates the password by making a login call to the Microsoft server, providing both the email and password.
If MFA is enabled, the W3LL Panel will first obtain a one-time password (OTP) by sending a request to the Microsoft server to begin the MFA authentication process. Then, a request is made to the W3LL backend, which displays an OTP password page.
If the login succeeds, the W3LL backend has captured the session cookie. W3LL Panel then uses the victim’s email address to retrieve the authenticated session cookie from the W3LL backend and sends a POST request to the Hastebin service, where the threat actor can access it later.
To discover accounts, W3LL threat actors employ the CONTOOL for automated discovery, monitoring, and data exfiltration, leveraging the Microsoft Graph API to extract data from compromised Microsoft 365 accounts. Lastly, the threat actors utilize manual methods to exploit the compromised accounts further, engaging in activities such as data theft, fake invoice scams, email owner impersonation, and malware distribution to fulfill their malicious objectives and maximize their gains.
The threat actors operating under W3LL primarily harbor financial motivations, leveraging a well-structured criminal business to profit from BEC attacks. They have fostered a closed community of phishers, utilizing the W3LL Store to facilitate sophisticated global phishing campaigns targeting corporate email accounts. The objective is clear: compromising corporate Microsoft 365 accounts, bypassing Multi-Factor Authentication (MFA), and harvesting sensitive data through advanced phishing kits. The campaigns have a broad target base, encompassing companies in various regions and industries, with strategies post-compromise, including data theft and fake invoice scams. In terms of capabilities, W3LL exhibits a high degree of sophistication, developing a range of user-friendly custom tools that enhance the efficiency and effectiveness of phishing campaigns, catering to criminals with different skill levels and allowing for the streamlined execution of BEC campaigns.
Risk & Impact Assessment
The W3LL phishing ecosystem presents a substantial risk to organizations, particularly in the US, UK, Australia, and Europe. The risk stems from the sophisticated array of tools and services offered, facilitating business email compromise (BEC) campaigns that have been on a significant rise, posing a severe threat. The tools, meticulously designed to increase the probability of a successful compromise, not only facilitate the harvesting and verification of credentials but also enable the hijacking of session cookies and ensure a higher success rate in compromising accounts. The impact of a successful account compromise can be severe, with threat actors employing post-compromise strategies to exploit the victims further. These strategies range from data theft to malware distribution, potentially leading to substantial financial losses and reputational damage. The impact assessment indicates a high level of sophistication in the strategies, with a notable focus on bypassing established security measures such as MFA, demonstrating a high potential for significant impact on organizations.
Threat Actors Exploited Zero-Day Vulnerability in Cisco ASA and FTD to Deploy Ransomware
Cisco ASA and FTD CVE-2023-20269 – Vulnerability Exploitation – Brute Force Attacks – Akira Ransomware – Lockbit Ransomware – Industries/All
Threat actors have exploited a zero-day vulnerability, now tracked as CVE-2023-20269, affecting Cisco ASA and FTD appliances, as documented by Cisco and Rapid7. This vulnerability allows threat actors to conduct brute force attacks and establish unauthorized clientless SSL VPN sessions. The successful exploitation of this vulnerability can lead to data exfiltration and ransomware deployment. Notably, Akira and Lockbit ransomware groups have been observed exploiting this vulnerability.
On 6 September 2023, Cisco published an advisory, and the CVE ID CVE-2023-20269 was assigned to a vulnerability exploited in the wild between March and August 2023. The vulnerability affects Adaptive Security Appliance (ASA) and Firepower Threat Defense (FTD) remote access VPNs. Currently, Cisco has not released an update to address this vulnerability. However, they have provided workarounds, which are provided in the recommendations section. The confirmed or possible exploitation of this vulnerability has been covered in two earlier blog posts, one from Cisco and the other from Rapid7. This vulnerability is due to improper authentication, authorization, and accounting separation between the remote access VPN feature and the HTTPS management and site-to-site VPN features. Exploiting this vulnerability could allow an unauthenticated, remote threat actor to conduct a brute force attack or establish a clientless SSL VPN session with an unauthorized user.
A clientless SSL VPN session refers to a VPN connection where the user/threat actor does not need to install a dedicated VPN client software on their end device to establish a secure connection to the VPN server. Instead, users/threat actors establish the VPN connection through their web browser using the SSL (Secure Sockets Layer) protocol, which encrypts the data traffic between the web browser and the VPN server. This type of VPN session allows users/threat actors to access web applications, file shares, and other resources on the network securely through their browsers without needing a full VPN client installation.
The vulnerability (CVE-2023-20269) in the remote access VPN feature of Cisco ASA FTD devices could allow an unauthenticated, remote threat actor to conduct a brute force attack or an authenticated, remote threat actor to establish a clientless SSL VPN session with an unauthorized user. This vulnerability is due to improper authentication, authorization, and accounting separation between the remote access VPN feature and the HTTPS management and site-to-site VPN features. A threat actor could exploit this vulnerability by specifying a default connection profile/tunnel group while conducting a brute force attack or establishing a clientless SSL VPN session using valid credentials.
Threat Analysis
This vulnerability affects Cisco devices running a vulnerable Cisco ASA or FTD Software release. However, Cisco does not list vulnerable versions apart from Cisco ASA Software release version 9.16 or earlier. However, organizations can use Cisco’s software checker tool, which identifies any Cisco security advisories that impact a specific software release and the earliest release that fixes the vulnerabilities. Alternatively, Cisco provides a form in the advisory to search for vulnerabilities affected by CVE-2023-20269.
The exact conditions to determine whether a device is susceptible to CVE-2023-20269 depend on the desired outcome, as detailed below. The following conditions must be met for threat actors to execute a brute-force attack:
- At least one user is configured with a password in the LOCAL database.
OR - HTTPS management authentication points to a valid AAA server.
AND - SSL VPN is enabled on at least one interface.
OR - IKEv2 VPN is enabled on at least one interface.
All of the following conditions need to be met for threat actors to establish a clientless SSL VPN session successfully:
- The threat actor has to have valid credentials for a user in the LOCAL database or in the AAA server used for HTTPS management authentication. These credentials could be obtained using brute force attack techniques.
- The device is running Cisco ASA Software Release 9.16 or earlier.
- SSL VPN is enabled on at least one interface.
- The clientless SSL VPN protocol is allowed in the DfltGrpPolicy.
Note: When running Cisco FTD Software, this method cannot succeed as Cisco FTD Software does not support the clientless SSL VPN feature.
The confirmed or possible exploitation of this vulnerability has been covered in two earlier blog posts, one from Cisco and the other from Rapid7. Both blog posts cover the same or similar activity: threat actors leveraging weak or default passwords to conduct credential stuffing and brute-force attacks, sometimes capitalizing on the lack of multi-factor authentication (MFA) or improper configuration. Some of these exploitation attempts resulted in the deployment of Akira or Lockbit ransomware.
According to Rapid7’s blog post, threat actors deployed and executed a batch script upon successful authentication to internal assets, resulting in the installation and execution of the remote desktop application AnyDesk. In some cases, threat actors executed nd.exe on systems to dump NTDS.DIT, SAM, and SYSTEM hives, which may have given the threat actors access to additional domain user credentials. The threat actors performed further lateral movement and binary executions across other systems to increase the scope of compromise.
Risk & Impact Assessment
The core risk stems from the vulnerability (CVE-2023-20269) that allows threat actors to identify valid credentials, which they could use to establish an unauthorized remote access VPN session and establish a clientless SSL VPN session (only when running Cisco ASA Software Release 9.16 or earlier). This risk can be elevated by a lack of multi-factor authentication (MFA) in VPN configurations. The Akira and Lockbit ransomware groups have been observed leveraging the vulnerability in VPN software and the absence of MFA to initiate their ransomware campaigns. Furthermore, threat actors utilized brute force techniques and may have purchased credentials from the dark web to gain unauthorized access to systems.
Exploiting the identified vulnerability and the targeted ransomware campaigns can potentially significantly impact organizations. Unauthorized access to Cisco VPNs can lead to a series of detrimental outcomes, including data exfiltration and ransomware deployment, severely compromising the confidentiality and availability of sensitive data. The Akira and Lockbit ransomware groups operate with an extortion strategy, listing victims and stolen information on TOR network-based websites if ransom demands are not met, escalating the potential financial and reputational damage. Moreover, the absence of detailed logs in Cisco ASA configurations hinders a comprehensive understanding and response to intrusions, leaving organizations with gaps in their defense and response mechanisms.
Threat Actors Deploy Trio of Malware via Sophisticated Phishing Campaign
Phishing – Word Document – OriginBotnet – Redline Clipper – AgentTesla – Industries/All
Read about a sophisticated phishing campaign used by threat actors to deploy three malware families, each with unique capabilities, to compromise data security significantly. The campaign manipulates cryptocurrency transactions and extracts sensitive data, posing a severe risk to organizations by potentially causing substantial financial and operational repercussions. The insights gained from this analysis aim to improve current detection strategies, deepen understanding of the risks involved, and aid in anticipating future threat tactics, thereby enhancing your organization’s cyber resilience.
Fortinet’s recent blog post detailed how threat actors utilized malicious Microsoft Word documents to distribute OriginBotnet, RedLine Clipper, and AgentTesla malware families. This sophisticated attack begins with a phishing email encouraging recipients to download a malware loader through a deceptive Word document. Characterized by a binary padding evasion strategy, the loader facilitates a multi-stage malware deployment, each harboring distinct functionalities ranging from keylogging to cryptocurrency theft and harvesting sensitive information.
OriginBotnet is known for its multifaceted capabilities, including sensitive data collection and establishing communications with its command and control (C2) server, facilitating keylogging and password recovery functions on compromised devices. RedLine Clipper, also known as ClipBanker, specializes in cryptocurrency theft, manipulating clipboard activities to alter wallet addresses, thereby redirecting funds to the threat actor’s wallet. AgentTesla is a spyware that logs keystrokes, accesses host clipboards and conducts disk scans to retrieve credentials and other valuable data, transmitting them to its C2 server through various channels.
Threat Analysis
The infection chain begins with a meticulously crafted phishing email containing a malicious Microsoft Word document attachment. It is displayed as a blurred image with a fake reCAPTCHA to lure the recipient into clicking it. Clicking on the fake reCAPTCHA activates an embedded malicious link, setting the stage for malware deployments.
The malicious link downloads, decrypts, and executes a multi-stage loader that employs a binary padding evasion strategy, increasing the file size to a substantial 400 MB to avoid detection. The loader operates in several stages, each involving different executable files and DLLs that work in tandem to decode resource data, establish persistence in the system, and facilitate further malware downloads. It utilizes encryption and decryption algorithms, including AES-CBC and AES-ECB, to secure communications and maintain stealth.
OriginBotnet initiates its operation by scanning running processes to avoid duplication, stored as “david.exe.” It collects detailed information about the victim’s system, including installed antivirus products and system specifications. This malware communicates with its C2 server to receive commands for downloading and executing additional files, showcasing its keylogging and password recovery capabilities.
RedLine Clipper, also known as ClipBanker, originates from a URL specified in the loader. It monitors the system clipboard to identify cryptocurrency wallet addresses. When detected, it replaces the user’s wallet address with the threat actor’s, effectively hijacking cryptocurrency transactions to redirect funds to the threat actor’s wallet.
AgentTesla is stored as “COPPER.exe” and is adept at logging keystrokes and accessing the host’s clipboard to scan for credentials and other valuable data. It maintains persistence by replicating itself in the system and can transmit the gathered data to its C2 server through various communication channels, including SMTP and FTP.
The operation orchestrated by the threat actors showcases an intention encompassing financial gain through cryptocurrency theft and selling sensitive data harvested from compromised systems. The meticulous planning and execution hint at a potential objective of large-scale data exfiltration, targeting individual and organizational assets to obtain unauthorized access to sensitive information. The capabilities demonstrated in this operation are substantial, leveraging a series of sophisticated malware, each with distinct functionalities. The threat actors have exhibited deep knowledge in crafting multi-stage malware deployments, utilizing encryption algorithms and evasion strategies to avoid detection. This operation showcases their technical prowess and a deep understanding of human psychology, leveraging social engineering techniques to lure individuals into initiating the malware deployment chain.
Risk & Impact Assessment
While the exact extent of the distribution is currently unknown, including the number of emails sent and the precise number of victims, it is prudent for organizations to err on the side of caution, given the sophistication of the threat outlined by Fortinet. Deploying OriginBotnet, RedLine Clipper, and AgentTesla presents a notable risk, potentially impacting an organization’s operations and corporate assets significantly. The threat actors have demonstrated a capacity to craft a detailed phishing scheme and a multi-stage malware deployment, which, if successful, could grant unauthorized access to systems, disclose sensitive information, modify data, and disrupt operations. Consequently, the impact of a successful infection could be severe, encompassing data exfiltration, disruption of information systems, and potential data destruction. Organizations should remain vigilant, recognizing the potential for substantial damage and the imperative to implement robust security measures to safeguard against this sophisticated threat.
Storm-0324 and JSSLoader’s Connection to Ransomware
Storm-0324 – Sangria Tempest – JSSLoader – TeamPhisher – Phishing – Industries/All
A new report delves into the operations of Storm-0324, a malware distributor notorious for facilitating ransomware operators’ access through evolving tactics, techniques, and procedures (TTPs). The group’s sophisticated phishing strategies and malware distribution techniques have been a significant threat to organizations globally since at least 2016. The report offers a deep dive into their recent activities, including deployment of the JSSLoader email-based infection chain and initiating a new Teams-based phishing campaign in July 2023, leveraging vulnerabilities such as CVE-2023-21715 and tools like TeamsPhisher.
The recent blog post by Microsoft Threat Intelligence presents a critical examination of Storm-0324, a cybercriminal group notorious for facilitating ransomware access through diverse avenues, including email-based infection chains and Teams-based phishing activities. The post aims to equip network defenders with the essential knowledge and tools to counteract this formidable threat actor. By delving deep into Storm-0324’s tools, tactics, and procedures (TTPs) and proposing defensive strategies, the blog aspires to assist readers in significantly reducing the potential repercussions of the group’s operations on their networks, thereby nurturing a more secure cyber environment.
Storm-0324, also identified as DEV-0324 with activity that overlaps with groups TA543 and Sagrid, has played a prominent role in the cybercriminal landscape, operating as a malware distributor since at least 2016. The group is known for crafting highly-evasive infection chains, predominantly leveraging email-based vectors. Their modus operandi involves distributing a variety of first-stage payloads, encompassing several banking trojans and ransomware. Since 2019, the group has mainly disseminated the JSSLoader malware, paving the way for the ransomware-as-a-service (RaaS) actor Sangria Tempest to gain access. In a notable evolution of their tactics, they initiated Teams-based phishing activities in July 2023, utilizing an open-source tool to circulate phishing lures through Microsoft Teams chats.
Threat Analysis
Since as early as 2019, Storm-0324 has utilized a sophisticated infection chain, primarily deploying phishing emails that reference invoices or payments to direct users to a SharePoint site hosting a ZIP archive. This archive harbors files with embedded JavaScript code, which, when executed, deploys a JSSLoader variant DLL, followed by additional tooling, such as the Griffon malware from Sangria Tempest. Leveraging the CVE-2023-21715 vulnerability, the group employs files like WSF and Ekipa to host the JavaScript code. These emails often contain a security code or password, enhancing their believability and serving as an anti-analysis measure necessitating user interaction post-launch.
In July 2023, the group began using a new phishing strategy, utilizing TeamsPhisher to distribute malicious links through Microsoft Teams chats, which, when clicked, lead to a SharePoint-hosted malicious file. TeamsPhisher facilitates the attachment of files to messages sent to external tenants, a function the group abuses to disseminate phishing attachments. To counteract these phishing campaigns, Microsoft has taken measures such as suspending identified accounts linked to fraudulent activities and bolstering user notifications to encourage caution against unknown or malicious senders.
Historically, Storm-0324 has orchestrated a malware distribution chain using exploit kits and email-based vectors to deliver a variety of first-stage payloads, including banking trojans and ransomware. The group has leveraged traffic distribution systems like BlackTDS and Keitaro for identification and filtering capabilities, enabling them to evade detection by specific IP ranges and redirect victims to their malicious download site. Since 2019, the primary malware has been the JSSLoader, facilitating access for the ransomware actor Sangria Tempest.
Storm-0324 operates with financial motivations, striving to gain initial access through email-based infection vectors and subsequently hand off access to compromised networks to other threat actors, often culminating in ransomware deployments. Their objectives encompass infiltrating systems to distribute first-stage payloads, facilitating access for other cybercriminal groups, and showcasing a high degree of collaboration within the cybercriminal ecosystem. The group exhibits substantial capabilities, crafting highly evasive infection chains and employing sophisticated tools and techniques, including exploiting recent vulnerabilities and leveraging open-source tools for phishing endeavors.
Risk & Impact Assessment
The risk posed by Storm-0324 to organizations globally is substantial, grounded in the group’s persistent and evolving threat activities spanning several years. While the exact number of victims remains unspecified in the source material, the detailed account of their tactics and the sophistication of their tools indicate a high probability of many entities being at risk. Storm-0324’s operations severely threaten the confidentiality, integrity, and availability of data and information systems. Their established and evolving tactics present a considerable risk of unauthorized access to systems and data, potentially leading to the exfiltration of sensitive information, disruption of operations, and even destruction or loss of data. The impact of falling victim to an intrusion facilitated by Storm-0324 is grave. Organizations can expect substantial disruptions, financial repercussions, and potential reputational damage. The group’s facilitation of ransomware attacks through distributing first-stage payloads further exacerbates the potential impact, setting the stage for more dangerous follow-on malicious activity, including ransomware deployment. It is imperative to note that this assessment is based on qualitative analysis, and a more accurate estimation of risk would benefit from quantitative data on the number of victims targeted or affected by Storm-0324’s operations.
Undetected for Over 3 Years: Sophisticated Threat Actors Leverage Supply Chain Attack to Target Linux Systems
Supply Chain Attack – Linux – Backdoor – Infostealer – Industries/All
A new report details a sophisticated malware campaign that targeted Linux systems for three years through a supply chain attack leveraging the official Free Download Manager website. This report delineates the multi-stage infection process involving a DNS-based backdoor and a bash stealer, facilitating unauthorized access and extensive data harvesting, including sensitive credentials and cryptocurrency wallet files.
The blog post from Kaspersky’s Securelist, titled “Free Download Manager backdoored – a possible supply chain attack on Linux machines,” comprehensively analyzes a malware campaign targeting Linux systems through a potentially compromised version of the Free Download Manager software. The blog post aims to detail the multi-faceted threat operating undetected for over three years, leveraging a DNS-based backdoor and a bash stealer to compromise systems. The blog post analyzes Linux systems that have been infected through this campaign, dissecting the malware components and the methods employed by the attackers to maintain persistence and evade detection.
The malware campaign has been silently perpetrating since 2020, utilizing a malicious Debian package of the Free Download Manager software distributed through a deceptive repository. This campaign is characterized by a sophisticated multi-stage infection process involving a DNS-based backdoor and a bash stealer, facilitating unauthorized access and data theft from the infected systems. The backdoor and bash stealer have historical roots in known threats, including the Bew backdoor, known since 2013, and a variant of a bash stealer described in 2019. Despite the significant footprint of this campaign, it remained undetected for years, illustrating the stealth and complexity of the threat actors’ approach.
Threat Analysis
The threat actors orchestrated a supply chain attack to distribute the infected Debian package, leveraging the official website of the Free Download Manager software. Kaspersky’s investigation revealed that users visiting the official site to download the software were, in certain instances, redirected to a malicious domain hosting the compromised package. This redirection did not occur uniformly, suggesting that the malware developers possibly scripted the redirection to trigger based on a certain degree of probability or the digital fingerprint of the potential victim, allowing the threat actors to maintain a presence on the official website, intermittently distributing the malicious Debian package between 2020 and 2022. Upon installation, an infected post-installation script executes, dropping two executable files (crond and bs) into the system and establishing persistence through a cron task that triggers every 10 minutes. This script unveils a two-pronged infection involving a DNS-based backdoor and a bash stealer.
The backdoor, once installed, initiates with a type A DNS request to a specific domain, receiving in return two IP addresses that encode the address and port of a secondary C2 server. This backdoor launches a reverse shell, facilitating communication with the C2 server via SSL or TCP, depending on the connection type specified in the DNS response. In the case of SSL communication, it launches the second executable file (bs), delegating all further communications to this executable.
The bs executable is the bash stealer and is tasked with harvesting sensitive data from the infected system, including system information, browsing history, saved passwords, cryptocurrency wallet files, and credentials for various cloud services. Post-data collection, the bash stealer leverages an uploader binary fetched from the C2 server to transmit the harvested data back to the threat actors. However, Kaspersky did not observe any additional activity via the reverse shell.
The threat actors behind this campaign exhibited a high degree of sophistication and strategic planning, leveraging a supply chain attack to infiltrate a broad spectrum of Linux systems. While not explicitly stated, their intentions appear to be centered around extensive data harvesting, potentially aiming for financial gains, espionage, or selling the data on cybercriminal marketplaces. The meticulous execution of the supply chain attack, utilizing the official website, indicates a well-planned operation with objectives to gain unauthorized access to systems, maintain a stealthy presence, and exfiltrate sensitive data over a prolonged period. The complex multi-stage infection process underscores their capabilities, the probabilistic redirection script, and the deep understanding of Linux systems, showcasing technical skills, knowledge, and strategic insight in choosing and exploiting their attack vector to remain undetected for an extended period.
Risk & Impact Assessment
The malware campaign exploiting the Free Download Manager software presents a significant risk to organizations and individual users, with a high likelihood of incidents involving unauthorized access to systems and potential loss of data confidentiality, integrity, and availability. The sophisticated multi-stage infection process facilitates various malicious activities, primarily data theft, but could lead to financial loss and future malicious activity through account compromise. The impact of this campaign is severe, with organizations potentially facing financial and reputational damage due to the extensive harvesting of sensitive data, including credentials for various cloud services and cryptocurrency wallet files.
This campaign’s extended undetected operational period further exacerbates the impact, offering threat actors a prolonged window to exfiltrate data, potentially leading to a deep-seated compromise of organizational assets and operations. Moreover, the probabilistic nature of the redirection script used in the supply chain attack complicates the assessment of the full extent of the impact, given the selective targeting strategy employed by the threat actors.
Latest Additions to Data Leak Sites
Professional, Scientific, and Technical Services – Manufacturing – Information – Retail Trade – Real Estate and Rental and Leasing
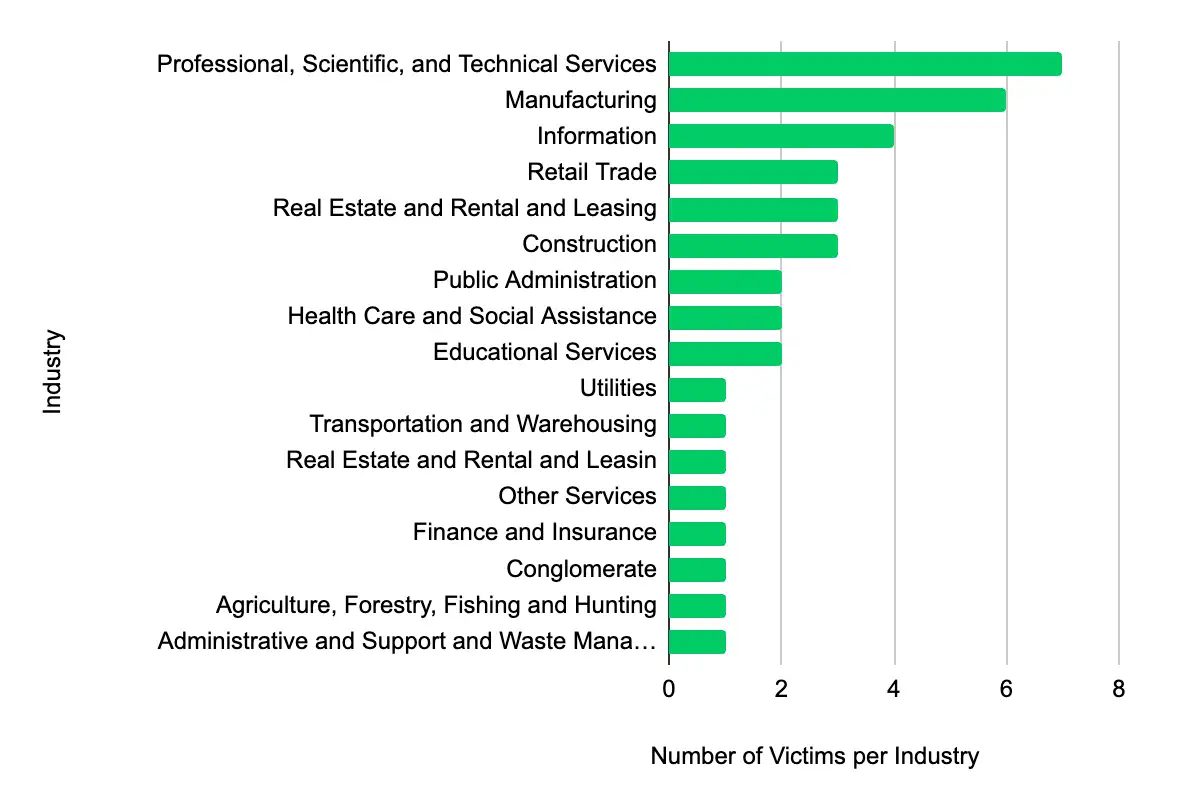
In the past week, monitored data extortion and ransomware threat groups added 40 victims to their leak sites. Of those listed, 22 are based in the US. Professional, Scientific, and Technical Services was the most popular industry listed, with seven victims. They were followed by 6 in Manufacturing, four in Information, and three each in Retail Trade and Retail Trade – Real Estate and Rental and Leasing. This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds 7 CVEs to its Known Exploited Vulnerabilities Catalog
Within the past week, CISA added seven CVEs to the catalog, affecting products from Microsoft, Apple, Cisco, Google, and Android. Threat actors can exploit these vulnerabilities for privilege escalation, conduct a brute force attack, perform an out-of-bounds memory write, disclose information, and code execution. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action occur between 2 and 4 October 2023.
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date |
|---|---|---|---|---|
| CVE-2023-35674 | Android | Framework | Android Framework contains an unspecified vulnerability that allows for privilege escalation. | 10/04/2023 |
| CVE-2023-20269 | Cisco | ASA & FTD | Cisco Adaptive Security Appliance and Firepower Threat Defense contain an unauthorized access vulnerability that could allow an unauthenticated, remote attacker to conduct a brute force attack in an attempt to identify valid username and password combinations or establish a clientless SSL VPN session with an unauthorized user. | 10/04/2023 |
| CVE-2023-4863 | Chromium | Google Chromium contains a heap-based buffer overflow vulnerability in WebP that allows a remote attacker to perform an out-of-bounds memory write via a crafted HTML page. | 10/04/2023 | |
| CVE-2023-36761 | Microsoft | Word | Microsoft Word contains an unspecified vulnerability that allows for information disclosure. | 10/03/2023 |
| CVE-2023-36802 | Microsoft | Streaming Service Proxy | Microsoft Streaming Service Proxy contains an unspecified vulnerability that allows for privilege escalation. | 10/03/2023 |
| CVE-2023-41064 | Apple | iOS, iPadOS, and macOS | Apple iOS, iPadOS, and macOS contain a buffer overflow vulnerability in ImageIO when processing a maliciously crafted image, which may lead to code execution. This vulnerability was chained with CVE-2023-41061. | 10/02/2023 |
| CVE-2023-41061 | Apple | iOS, iPadOS, and watchOS | Apple iOS, iPadOS, and watchOS contain an unspecified vulnerability due to a validation issue affecting Wallet in which a maliciously crafted attachment may result in code execution. This vulnerability was chained with CVE-2023-41064. | 10/02/2023 |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share