Threat Actors Deploy Custom Malware, Modify Open-Source InfoStealer and Use Social Engineering to Reset MFA for SuperAdmins in Okta.
This week: ATP group Earth Estries deploys custom malware, threat actors use open-source InfoStealer and social engineering in attacks, a new variant of Chae$ malware is targeting finance and logistics – all this and the latest from data leak sites and CISA’s CVE catalog.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- Trend Micro: Earth Estries Targets Government, Tech for Cyberespionage
- Cisco Talos: SapphireStealer: Open-source information stealer enables credential and data theft
- Okta: Cross-Tenant Impersonation: Prevention and Detection
- Security Joes: New Attack Vector In The Cloud: Attackers caught exploiting Object Storage Services
- Morphisec: Threat Profile Chae$ Malware
- The Latest Additions from Data Leak Sites
- CISA Adds 2 CVEs to its Known Exploited Vulnerabilities Catalog
APT Group Deploys Custom Malware in Intelligence Collection Operation
Earth Estries – Zingdoor – TrillClient – HemiGate – Backdoor – Infostealer – All Industries
According to a blog post by Trend Micro, Earth Estries, an active cyber intelligence collection group, has targeted governmental and technology sector organizations with sophisticated backdoors and hacking tools, including Zingdoor, TrillClient, and HemiGate. The group employs advanced evasion techniques, such as the PowerShell downgrade technique, and abused public services like GitHub and Gmail for command and control. They focused on exfiltrating specific files, notably PDF and DDF files, and have a broad targeting scope affecting organizations in multiple countries.
The blog post by Trend Micro, titled “Earth Estries Targets Government, Tech for Cyberespionage” provides an in-depth analysis of a cyber intelligence collection operation conducted by a threat actor group named Earth Estries. The report dissects the tactics, techniques, and procedures (TTPs) employed by Earth Estries, highlighting the group’s focus on targeting governmental and technology sector organizations. The report also identifies overlaps in TTPs between Earth Estries and another advanced persistent threat (APT) group, FamousSparrow. The analysis aims to guide organizations in assessing their digital assets and enhancing their security configurations.
Earth Estries is an active cybercriminal group with operations dating back to 2020. Specializing in cyber intelligence collection operations, the group employs a range of sophisticated backdoors and hacking tools to compromise its targets. Among these are Zingdoor, a new HTTP backdoor written in Go that is designed for cross-platform capabilities and is heavily obfuscated; TrillClient, an information stealer focused on browser data, packed in a single cabinet file and heavily obfuscated; and HemiGate, another backdoor that communicates with its command-and-control (C&C) server over port 443 and employs RC4 encryption for its configuration files.
A common thread in Earth Estries’ operations is the use of Dynamic-Link Library (DLL) sideloading, a technique that involves loading a malicious DLL by exploiting the legitimate process of a trusted program, allowing the group to deploy various payloads, including tools like Cobalt Strike, PlugX, and Meterpreter.
Upon successful infiltration, Earth Estries compromises existing accounts with administrative privileges and installs Cobalt Strike on the system. The deployment of Cobalt Strike enables them to deploy additional malware and perform lateral movement within the network. The group uses Server Message Block (SMB) and WMI command line (WMIC) to propagate their backdoors and hacking tools to other machines within the target’s environment. The group takes measures to reduce their footprint and risk of exposure. After each operation, they regularly clean their existing backdoor and redeploy new malware for subsequent rounds. They also use the Fastly CDN service to hide the actual IP addresses of their C&C servers. The group’s C&C domains share similar address formats and are hosted on virtual private server (VPS) services in different countries.
In terms of their toolset, Earth Estries employs a variety of sophisticated malware and backdoors to achieve their objectives. One such tool is Zingdoor, designed for cross-platform capabilities. This backdoor is heavily obfuscated and employs anti-UPX unpacking techniques. It is disguised as mpclient.dll and runs via DLL sideloading. Another tool in their arsenal is TrillClient, an information stealer designed to exfiltrate browser data. This malware is packed in a single cabinet file and heavily obfuscated. It connects to a GitHub repository to retrieve commands for its next set of actions. Lastly, Earth Estries uses HemiGate, a backdoor that communicates with its command and control server over port 443 and employs RC4 encryption for its configuration files. Like Zingdoor, HemiGate is executed via DLL sideloading and supports a range of functionalities, including keylogging and file operations. These tools demonstrate Earth Estries’ advanced capabilities and adaptability, making them a formidable threat.
The overarching intention of Earth Estries is intelligence collection. In their latest operation, the group aims to infiltrate organizations in the government and technology sectors to exfiltrate sensitive data, which can be analyzed for strategic advantage. Their operation targeted organizations in the Philippines, Taiwan, Malaysia, South Africa, Germany, and the United States. The group seeks unauthorized access to internal servers and aims to compromise accounts with administrative privileges. The threat actors focus on exfiltrating specific types of files, notably PDF and DDF files, which are uploaded to online storage repositories for later use. Earth Estries demonstrates high-level capabilities, leveraging sophisticated tools and techniques. The group uses multiple backdoors and hacking tools in their operations. They employed a PowerShell downgrade technique by manipulating a communication session to force an older or weaker version of PowerShell to evade Windows Antimalware Scan Interface (AMSI) logging mechanisms. They also abuse public services like Github, Gmail, AnonFiles, and File.io for command and data exchange.
Risk & Impact Assessment
Earth Estries’ operation poses a multi-faceted risk to organizations, particularly those in various countries’ government and technology sectors. The group’s tactics, techniques, and procedures (TTPs) demonstrate a high level of sophistication, including the use of multiple backdoors and hacking tools, PowerShell downgrade techniques, and abuse of public services like Github and Gmail for command and control (C2) and data exfiltration. The risk to confidentiality is pronounced, given the group’s focus on intelligence collection targeting sensitive files. Earth Estries’ ability to laterally move within an organization’s network significantly increases the risk to the confidentiality of data and systems. The group’s use of Cobalt Strike further amplifies this risk, providing a robust toolset for internal reconnaissance and data exfiltration. The likelihood of an incident is elevated because the group’s operation is suspected of being ongoing and the breadth of their targeting.
The impact of Earth Estries’ operations on targeted organizations is severe. The group’s ability to move laterally within a network can lead to widespread system compromise, affecting the organization’s core functions and mission. Financial repercussions could include the costs associated with incident response, system remediation, and potential regulatory fines for data breaches. Moreover, the group’s sophisticated skill set and resources allow them to prolong their activities and potential impact. Their use of multiple backdoors, hacking tools, and techniques to reduce their footprint makes detecting and eradicating challenging for security teams.
Threat Actors Modify Open-Source InfoStealer to Incorporate New Exfiltration Methods
SapphireStealer – FUD-Loader – Data Exfiltration – All Industries
The new blog post by Cisco Talos analyzes SapphireStealer, an open-source information stealer. The report delves into the malware’s capabilities, methods of data exfiltration, its loaders, and operational security failures identified in one sample. It also discusses the malware’s evolution since its initial public release in December 2022, highlighting its increasing prevalence in public malware repositories. The post aims to shed light on the multifaceted threat SapphireStealer poses, particularly its utility in credential and data theft and its adaptability for use in multi-stage infection processes.
SapphireStealer emerged as an open-source information stealer when it was published to GitHub on 25 December 2022, primarily designed to exfiltrate browser credential databases and files containing sensitive user information. Since its release, the malware has seen consistent upload activity to public repositories. Threat actors have extended the malware’s original codebase to support additional data exfiltration mechanisms, creating several variants. The malware is often delivered as part of a multi-stage infection process, sometimes leveraging other open-source malware downloaders like FUD-Loader, also available via the same GitHub account and made available on 2 January 2023.
SapphireStealer is written in .NET and offers a straightforward but effective set of functionalities aimed at stealing sensitive information from infected systems. The malware is capable of:
- Harvesting host information
- Capturing screenshots
- Extracting cached browser credentials
- Identifying and collecting files stored on the system that match a predefined list of file extensions
Upon execution, SapphireStealer first identifies any running browser processes and terminates them. It then queries for browser database file directories, targeting a wide range of browsers such as Chrome, Opera, Yandex, Brave Browser, and Microsoft Edge.
Cisco Talos observed threat actors modifying the file extensions targeted for collection and exfiltration by SapphireStealer. While some were minimal, only containing a few file extensions, others included many different file formats. Furthermore, unmodified SapphireStealer code featured redundant code execution, repeated superfluous executions of the same operations multiple times, and overall inefficiencies. Over time, Cisco Talos has observed that threat actors have taken steps to streamline the malware’s operations, refactor the code significantly, and improve upon the core functionality of the stealer.
To stage the data for exfiltration, SapphireStealer initially creates a working directory (the original source code uses %TEMP%\\sapphire\\work). The malware dumps the contents of any discovered credential databases into a text file within this directory, captures a screenshot, and stores it in the same directory. It also runs a file grabber that locates files with specific extensions on the victim’s desktop. All this data is then compressed into a log.zip archive.
The original source code uses Simple Mail Transfer Protocol (SMTP) to exfiltrate the staged data, where the malware sends an email containing the compressed archive and additional host-related information such as IP address, hostname, screen resolution, OS version, and CPU architecture. However, threat actors have modified the original source code to use Discord webhook API and Telegram posting API for data exfiltration.
SapphireStealer is often part of a multi-stage infection process. One loader observed with SapphireStealer is FUD-Loader, also written in .NET. This loader is responsible for leveraging HTTP/HTTPS communications to retrieve additional executables from actor-controlled infrastructure.
The primary intention behind the deployment of SapphireStealer is for financial gain through the sale or use of stolen credentials and data. It is also plausible that the stolen data could be used for intelligence collection. As the stealer has most likely been employed by multiple threat actors, the objectives are broad, targeting both individual and corporate environments. The stealer’s exfiltration of sensitive information, including corporate account credentials and access tokens, is typically sold on cybercriminal forums and used to compromise corporate networks further. Regarding capabilities, multiple variations of SapphireStealer have been observed, each improving and modifying the original code base separately, each with its own set of features and exfiltration methods. The threat actors demonstrate a moderate level of technical proficiency, as evidenced by their ability to modify the open-source code to suit their specific needs.
Risk & Impact Assessment
Organizations face a moderate to high likelihood of encountering SapphireStealer. This malware has seen a surge in activity since its inception in December 2022, mainly due to its open-source nature. This malware poses a substantial risk to individual users and organizations, threatening the confidentiality of sensitive data, including corporate credentials and access tokens, frequently traded in cybercriminal forums. The malware can compromise an organization’s internal networks, endangering mission-critical functions by terminating browser processes and data extraction from a broad array of browsers, thereby expanding the range of potential targets.
The malware utilizes various data exfiltration methods such as SMTP, Discord, and Telegram APIs, exacerbating defensive strategies’ complexity. In the event of a successful attack, the repercussions can be grave, encompassing unauthorized system access, data integrity, and confidentiality breaches, financial losses due to potential ransomware onslaughts or direct financial theft, and the facilitation of secondary attacks such as spear-phishing and advanced persistent threats (APTs). The stolen data may circulate among threat actors, potentially leading to extensive organizational disruption. While the impact of an attack can fluctuate based on the specific variant of SapphireStealer encountered, organizations uniformly face the prospect of considerable operational and financial repercussions, including reputational harm, legal ramifications, and the financial burdens associated with incident resolution and system recovery.
Threat Actors Use Social Engineering to Reset MFA for Super Administrators
Social Engineering – Okta MFA Reset – Initial Access – Okta Super Administrators – All Industries
The recent blog post, “Cross-Tenant Impersonation: Prevention and Detection,” published by Okta, analyzes an emerging threat targeting Okta tenants. The post focuses on the tactics of a threat actor who used social engineering to access highly privileged roles within multiple organizations’ Okta tenants. The post outlines the threat actors’ methods for lateral movement and defense evasion, particularly their ability to reset Multi-Factor Authentication (MFA) factors for highly privileged users. The article also sheds light on how these actors abuse legitimate identity federation features to impersonate users within the compromised organization, including using a second Identity Provider (IdP) to access applications within the compromised organization and act as a “source” IdP in an inbound federation relationship. The post aims to equip defenders with the knowledge to prevent such techniques and offers multiple detection opportunities.
Inbound Federation is a critical feature in identity management that allows a user authenticated by a source IdP to access applications in a target IdP. This feature is helpful in scenarios such as mergers, acquisitions, and divestitures and in large organizations requiring centralized control while allowing divisions some policy autonomy. Given the power and flexibility that Inbound Federation offers, access to create or modify an IdP is restricted to users with the highest permissions within an Okta organization—namely, Super Administrators or Org Administrators.
The threat actors demonstrated a high level of sophistication in their approach to compromising Okta tenants. Their operation involved a multi-step process, beginning with social engineering to target IT service desk personnel to manipulate them into resetting all Multi-Factor Authentication (MFA) factors for users with Super Administrator permissions. Before calling the IT service desk at the targeted organization, the threat actors either had the passwords to privileged user accounts or were able to manipulate the delegated authentication flow via Active Directory (AD).
Once MFA was reset, the threat actor accessed the compromised accounts using anonymizing proxy services to evade detection mechanisms that rely on IP and device reputation. However, the threat actor used an IP and device not previously associated with the user account.
The threat actor then used the compromised Super Administrator accounts for lateral movement within the organization. The actors assigned higher privileges to other accounts and, in some instances, removed second-factor requirements from authentication policies, weakening the organization’s security posture.
A particularly alarming technique involved the configuration of a second Identity Provider (IdP) to act as an “impersonation app.” This second IdP, controlled by the actor, served as a “source” in an inbound federation relationship with the target organization. The threat actor manipulated the username parameter for targeted users in this second “source” IdP to match a real user in the compromised “target” IdP, thereby gaining the ability to Single Sign-On (SSO) into applications as the targeted user.
The threat actors likely aimed to gain unauthorized access to sensitive data and systems within targeted organizations for intelligence collection, extortion, or to sell access. Focusing on compromising highly privileged Okta accounts, particularly Super Administrators, the threat actors sought to undermine the organization’s identity management system to impersonate any user. Their capabilities include advanced social engineering, identity and access management knowledge, evasion techniques, and using anonymizing proxy services.
Risk & Impact Assessment
The elevated likelihood of Okta Super Administrator accounts being compromised through social engineering poses severe risks, jeopardizing organizational data and systems’ confidentiality, integrity, and availability. These risks have far-reaching implications, including financial loss, reputational damage, and legal consequences. The focus on high-privilege accounts amplifies these risks, enabling widespread organizational impact.
The unauthorized access carries catastrophic consequences, affecting all facets of an organization. It opens avenues for data exfiltration, financial loss, and reputational harm. Data modification could misguide decision-making, while system disruption could halt operations and incur financial losses. In extreme cases, data loss could be irreversible, threatening the organization’s viability. The impact is organization-wide and could cascade to partners, customers, and stakeholders, making it an existential threat to organizations and their assets.
Threat Actors Exploit Two Vulnerabilities in MinIO, Gain Remote Code Execution
CVE-2023-28432 – CVE-2023-28434 – MinIO – Remote Code Execution – Exploit Publicly
The blog post by Security Joes, titled “New Attack Vector In The Cloud: Attackers caught exploiting Object Storage Services,” analyzes an emergent threat vector targeting cloud-based Object Storage Services. The article outlines adversaries’ tactics, techniques, and procedures (TTPs) to exploit two vulnerabilities in MinIO (CVE-2023-28434 and CVE-2023-28432), an Object Storage Service. With their post, Security Joes aims to raise awareness among cybersecurity professionals and cloud service users about this threat, offering insights into the exploitation methodologies and suggesting countermeasures to mitigate risks.
Object Storage is a data storage architecture that manages data as objects instead of traditional block or file storage architectures. Each object typically contains the data itself, metadata, and a unique identifier. Object Storage is highly scalable and is commonly used in cloud computing environments to store large volumes of unstructured data like media files, backups, and logs. MinIO is an open-source Object Storage service that is API-compatible with Amazon S3 cloud storage. MinIO Inc. designed MinIO to be simple and scalable, offering data protection and encryption features. MinIO has gained significant traction in enterprise and cloud-native deployments.
Threat actors have exploited two critical vulnerabilities in MinIO (CVE-2023-28434 and CVE-2023-28432). The exploitation began when the threat actors convinced a DevOps engineer to update MinIO to a vulnerable version. The threat actors then crafted a request targeting the endpoint to retrieve the admin credentials of a vulnerable instance (CVE-2023-28432). Upon retrieving the admin credentials, the threat actor can connect and engage with the compromised instance through the MinIO Client. With a foothold within the compromised instance, the actor exploits the admin update command (CVE-2023-28434), enabling the actor to designate an alternative URL for updates, replacing the authentic binary with a malicious one hosted on a remote server under the actor’s control.
Security Joes found that the malicious binary can function as a backdoor, giving the threat actor the ability to execute commands on the host running the application. The executed commands inherit the system permissions of the user who initiated the application. In this instance, the user launching the application held root-level permissions. The nature of this threat renders traditional signature-based detectors inadequate in detecting its presence. As of 5 September 2023, The file found by Security Joes has only one vendor flagging it as malicious.
Upon successfully compromising MinIO and securing remote code execution, the actor downloaded various scripts to fingerprint the system. The actor first issued commands to download and execute an initial downloader script. This script initiated a connection with the C2 server, executed two scripts for system profiling and network reconnaissance, and posted the results to the malicious server. Depending on the results obtained, the actor can determine the value of the compromised machine and decide whether to proceed by deploying additional scripts or to halt their operation altogether. This approach underscores the threat actor’s strategic approach in optimizing their efforts based on the perceived value of the compromised system.
If the actor proceeds with the intrusion, the actor can deploy additional scripts. Through an analysis of the actor’s infrastructure, Security Joes discovered a series of files, each designed to fulfill distinct roles within the intrusion chain. One of the files creates a Windows account and adds it to the “Remote Desktop Users” and “Administrators” groups. Another script discovered is designed to facilitate ping functionality, accomplished by dispatching ICMP echo requests to a designated host address. The primary purpose of this operation is to gauge the round-trip times (RTTs) and ascertain the accessibility of the target host. The last script identified is a one-line webshell similar to the China Chopper. The threat actor can potentially employ these tools to compromise additional environments that may not have any direct link to MinIO.
While researching this behavior, Security Joes discovered that the code in the malicious MinIO binary is available on GitHub under a repository named evil_minio, published on 4 April 2023. According to the repository’s maintainer, their code is a modified version of the MinIO source code and does not impact the normal functions of the tool. Instead, it provides a backdoor that can be accessed by appending the URL parameter “alive” to the MinIO application’s URL. The very detailed repository offers a detailed step-by-step PDF of the intrusion, allowing anyone to recreate the exploitation chain and follow it as a guide for taking over a vulnerable MinIO instance.
The objective of the threat actors exploiting MinIO vulnerabilities is unauthorized access to sensitive data stored in cloud object storage services, potentially for intelligence collection, extortion, or the sale of data or access to other threat actors. Their specific objectives appear multi-faceted, targeting MinIO instances due to their widespread use and compatibility with Amazon S3, with the ultimate goal being unauthorized access, exfiltration, disruption, or destruction of sensitive data. The capabilities demonstrated in carrying out these exploits are advanced, requiring a deep understanding of MinIO’s architecture and vulnerabilities and the skills to craft a sophisticated exploit chain leading to elevated system access. The threat actors are likely highly skilled and may have access to substantial resources, enabling them to execute complex and potentially devastating attacks.
Risk & Impact Assessment
The exploitation of MinIO presents an escalating and multi-faceted risk to organizations, with the likelihood of being exploited high, particularly given the public availability. The risks are not confined to data compromise but extend to a loss of data and information systems’ confidentiality, integrity, and availability. Specifically, threat actors can gain unauthorized access to sensitive data, modify existing datasets, and disrupt services, thereby affecting business continuity. Financial risks are also significant, encompassing the costs associated with incident response and remediation and potential loss due to other factors.
The impact of exploiting MinIO to deploy a rogue binary is far-reaching and severe. This intrusion allows threat actors to circumvent traditional security measures, gaining unauthorized access to an organization’s cloud infrastructure. The operational implications are dire, ranging from service disruptions and could affect internal and customer-facing applications to the exfiltration of sensitive data, such as customer information and intellectual property. The integrity of stored data can also be compromised, which has downstream effects on organizational decision-making. Threat actors can use the access to laterally move within the environment, further exacerbating the impact.
New Variant of Chae$ Malware Has Significantly Evolved its Capabilities, Targeting Financial and Logistics Sectors
Chae$ Malware – MSI Installer – Banking Trojan
The Morphisec report titled “Threat Profile: Chae$4 Malware” analyzes a new and advanced variant of Chae$ malware, version 4. The report aims to shed light on the malware’s evolving sophistication, components, and the latest industries targeted. Chae$ malware first appeared on the cybersecurity landscape in November 2020 when Cybereason published its research. Initially, it targeted e-commerce customers in Latin America, mainly focusing on users of the MercadoLibre platform. The malware has undergone several iterations since its inception, with research publications covering versions 1-3. The latest variant, Chae$ 4, marks a significant evolution in its capabilities. It has seen refinements in its code architecture, added layers of encryption, and a shift to Python for its codebase. The malware has also expanded its target list to include customers of prominent platforms and banks such as Mercado Libre, Mercado Pago, WhatsApp Web, Itau Bank, Caixa Bank, and MetaMask.
The Chae$ 4 variant represents a significant evolution in the malware’s development, characterized by a series of technical enhancements that significantly elevate its threat profile. Infections start by executing a malicious MSI installer masquerading as a JAVA JDE or Anti-Virus software installer. Execution of the malicious installer will cause the malware to deploy and download required files inside a dedicated and hard-coded folder under the %Appdata%/ folder.
One of the most notable changes is the shift to Python for its codebase, a strategic move that enhances its evasion capabilities against traditional defense systems. This variant has also adopted WebSockets for primary communication between its modules and the Command and Control (C2) server, replacing the previously used HTTP/HTTPS protocols. The malware’s architecture is now modular, allowing for the independent updating of its seven modules, each serving a specific malicious function. These modules range from system identification to extensive data theft, including login credentials, banking information, and cryptocurrency details. The malware also employs advanced techniques such as Domain Generation Algorithms (DGA) for dynamic resolution of the C2 server’s address, adding another layer of complexity and stealth to its operations.
Chae$ 4 has recently focused on customers of prominent platforms and banks such as Mercado Libre, Mercado Pago, WhatsApp Web, Itau Bank, Caixa Bank, and MetaMask. It also targets Content Management Systems (CMS) like WordPress, Joomla, Drupal, and Magento. This focus suggests a calculated strategy to maximize financial gain by targeting platforms with large user bases and potentially significant financial transactions.
The threat actors behind Chae$ 4 primarily aim for financial gain, a motive manifested in their meticulous targeting of customers of high-profile platforms and financial institutions such as Mercado Libre, Mercado Pago, WhatsApp Web, Itau Bank, Caixa Bank, and MetaMask. Their objectives are clear: to gain unauthorized access to systems and exfiltrate sensitive data, from login credentials to banking and cryptocurrency details. In terms of capabilities, these actors demonstrate advanced technical acumen, evidenced by the malware’s shift to a Python-based codebase for enhanced evasion, the adoption of WebSockets for secure and real-time communication with the C2 server, and a modular architecture that allows for independent updating of its multiple malicious modules. These capabilities are further augmented by sophisticated techniques such as Domain Generation Algorithms (DGA) for dynamic resolution of the C2 server’s address, underscoring their high level of expertise and resources.
Risk & Impact Assessment
The Chae$ 4 malware variant poses a substantial risk to organizations, particularly those in the Finance and Insurance and Transportation and Warehousing sectors. There is an elevated risk of an incident occurring due to the malware’s advanced capabilities and features. Risks manifest in multiple dimensions, including the loss of confidentiality through the exfiltration of sensitive data like login credentials and financial information, the loss of integrity via its ability to modify data, and the potential for loss of availability. However, this is not its primary function. The malware’s advanced evasion techniques further exacerbate the risk of unauthorized system access.
The impact of a successful Chae$ 4 infection would be multifaceted and severe. Financial losses would be immediate, stemming from unauthorized transactions and banking and cryptocurrency information theft. Operational disruptions are also a significant concern, especially in sectors like logistics and banking, where data integrity is crucial. The reputational damage from the loss of customer data could have long-term consequences, including loss of customer trust and potential legal ramifications. Furthermore, the stolen data could be sold on the dark web, leading to additional unauthorized activities and financial losses. Organizations must also allocate significant resources for incident response and system recovery, diverting them from core business functions.
Latest Additions to Data Leak Sites
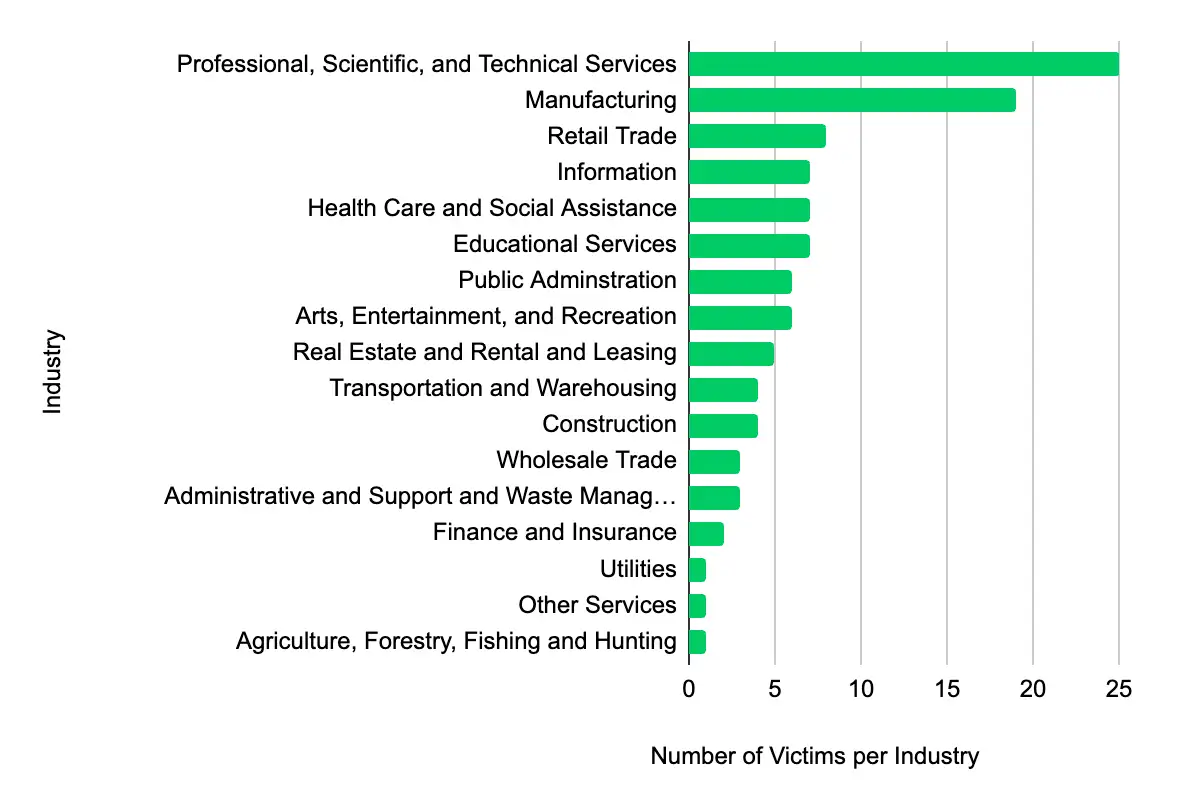
Professional, Scientific, and Technical Services – Manufacturing – Retail Trade – Information – Health Care and Social Assistance
In the past week, monitored data extortion and ransomware threat groups added 109 victims to their leak sites. Of those listed, 52 are based in the US. Professional, Scientific, and Technical Services was the most popular industry listed, with 25 victims. They were followed by 19 in Manufacturing, eight in Retail Trade, and seven each in Information and Health Care and Social Assistance. This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds CVE-2023-33246 to its Known Exploited Vulnerabilities Catalog
Within the past week, CISA added CVE-2023-33246 to the catalog, affecting Apache RocketMQ. A threat actor can exploit this vulnerability by using the update configuration function to execute commands as the system user RocketMQ is running as or achieve the same effect by forging the RocketMQ protocol content. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA setting a mitigation due date of 27 September 2023.
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date |
|---|---|---|---|---|
| CVE-2023-33246 | Apache | RocketMQ | Several components of Apache RocketMQ, including NameServer, Broker, and Controller, are exposed to the extranet and lack permission verification. An attacker can exploit this vulnerability by using the update configuration function to execute commands as the system users that RocketMQ is running as or achieve the same effect by forging the RocketMQ protocol content. | 09/27/2023 |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share