BlackTech Compromises Routers, Lumma Sets Up On Over 150 Servers, Ransomware Groups Repeatedly Hitting Victims, New Malware-as-a-Service Bunnyloader Surfaces, and EvilProxy Phishing Targets Job Site Indeed
This week: Chinese threat actor BlackTech discovered compromising router firmware, new Lumma information stealer revealed in over 150 servers, multiple ransomware actors are teaming up to hit victims in succession, new malware-as-a-service Bunnyloader emerges, and EvilProxy targets job site Indeed –all of this plus the latest from data leak sites and 5 new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
This Week’s Source Material
- CISA: People’s Republic of China-Linked Cyber Actors Hide in Router Firmware
- Silent Push: The Dead Russian Poets Society’: Silent Push uses behavioral fingerprinting, content scans and a 128-year old Russian poem to uncover 150+ new ACTIVE Lumma C2 servers and admin panels.
- FBI: Two or More Ransomware Variants Impacting the Same Victims and Data Destruction Trends
- Menlo Security: EvilProxy Phishing Attack Strikes Indeed
- Zscaler: BunnyLoader, the newest Malware-as-a-Service
- The Latest Additions from Data Leak Sites
- CISA Adds 5 CVEs to its Known Exploited Vulnerabilities Catalog
BlackTech Compromised International Subsidiaries Replaced Router Firmware to Target US and Japan Headquarters
BlackTech – Router Modification – Custom Malware – Cyber Espionage – Industries/All
Overview & Background
The joint Cybersecurity Advisory from the NSA, the FBI, CISA, the Japan National Police Agency (NPA), and the Japan National Center of Incident Readiness and Strategy for Cybersecurity (NISC) titled “People’s Republic of China-Linked Cyber Actors Hide in Router Firmware” details the activities of the People’s Republic of China (PRC)-linked cyber actors known as BlackTech. The joint Cybersecurity Advisory aims to shed light on BlackTech’s capabilities in modifying router firmware without detection and exploiting routers’ domain-trust relationships for pivoting from international subsidiaries to headquarters in Japan and the US, which are the primary targets. The advisory analyzes the tactics, techniques, and procedures (TTPs) employed by BlackTech, highlighting the need for multinational corporations to review all subsidiary connections, verify access, and consider implementing Zero Trust models to limit the extent of a potential BlackTech compromise.
BlackTech, also known by various aliases such as Palmerworm, Temp.Overboard, Circuit Panda and Radio Panda have been active since 2010 and are notorious for their advanced cyber-espionage campaigns. The group has historically targeted various sectors, including government, industrial, technology, media, electronics, and telecommunications, focusing on entities supporting the militaries of the U.S. and Japan. BlackTech is well-known for developing customized malware and tailored persistence mechanisms, enabling them to compromise routers and disable logging to conceal their operations.
Threat Analysis
BlackTech employs a variety of custom malware families, including BendyBear, Bifrose, BTSDoor, and WaterBear, targeting Windows, Linux, and FreeBSD operating systems. These malware families are continuously updated to evade detection, and payloads are often signed with stolen code-signing certificates to appear legitimate.
BlackTech utilizes living off-the-land tactics to blend with normal operating system and network activities, evading detection by endpoint detection and response (EDR) products. Persistence methods include NetCat shells, modifying the victim registry to enable the remote desktop protocol (RDP), and secure shell (SSH). The group uses SNScan for enumeration and a local file transfer protocol (FTP) server to move data through the victim network.
The actors target international subsidiaries of U.S. and Japanese companies, gaining access to internal networks and exploiting trusted network relationships to expand their access to target networks. They modify the firmware of routers to hide their activity and maintain persistence in the network. BlackTech targets branch routers and abuses their trusted relationship within the corporate network, using compromised routers for proxying traffic and pivoting to other victims on the same corporate network.
BlackTech has exploited various brands and versions of router devices, concealing configuration changes, hiding commands, and disabling logging while conducting operations. They have compromised several Cisco routers using variations of a customized firmware backdoor, turning backdoor functionality on and off through specially crafted TCP or UDP packets. However, this is not limited to Cisco routers; actors could use similar techniques to enable backdoors in other network equipment. Additionally, the actors have been observed replacing the firmware for certain Cisco IOS-based routers with malicious firmware, with an SSH backdoor, to establish persistent backdoor access and obfuscate future malicious activity. The actors replace the firmware by first installing older legitimate firmware that they modify in memory to allow the installation of a modified unsigned bootloader and firmware.
To hide their presence and obfuscate changes made to compromised Cisco routers, the actors may hide Embedded Event Manager (EEM) policies that manipulate Cisco IOS Command-Line Interface (CLI) command results. EEM is a feature usually used in Cisco IOS to automate tasks that execute upon specified events. On a compromised router, the malicious EEM policy waits for specific commands to execute obfuscation measures or deny execution of specified, legitimate commands. This malicious EEM policy removes lines containing certain strings in the output of specified, legitimate Cisco IOS CLI commands and prevents the execution of other legitimate CLI commands, such as blocking copy, rename, and move commands for the associated EEM policy to hinder forensic analysis.
BlackTech’s intentions are likely for intelligence collection. The group likely aims to facilitate the collection of sensitive information, trade secrets, intellectual property, and government secrets for political, economic, or strategic advantage. The targeting of entities supporting the militaries of the U.S. and Japan indicates a focus on gaining insights into military and strategic operations. The objectives of BlackTech include obtaining unauthorized access to systems and modifying router firmware to access parent organizations, demonstrating an objective to compromise network infrastructure and pivot within organizational networks. BlackTech possesses advanced capabilities, evidenced by its development of customized malware, dual-use tools, and exploitation of living off-the-land tactics. The group’s ability to modify router firmware, disable logging, and exploit trusted network relationships showcases their technical proficiency and resourcefulness in conducting sophisticated cyber-espionage campaigns.
Risk & Impact Assessment
BlackTech’s sophisticated operations present a pronounced risk to the confidentiality and integrity of organizational data and information systems. The group’s ability to modify router firmware to gain unauthorized access and exploit trusted network relationships poses a significant threat to the disclosure of sensitive information, trade secrets, intellectual property, and government secrets. However, while less likely, there is the possibility of a risk to availability, especially if a mistake in firmware replacement renders a device inoperable, thereby disrupting operations. The impact of such a compromise could be substantial, potentially affecting net sales, revenues, or income from continuing operations for the targeted organizations. Such compromise could lead to the unauthorized access and modification of data, leading to the leakage of proprietary information or trade secrets, loss of competitive advantage, damaged reputations, or legal consequences. Additionally, if the actors make a mistake in firmware replacement, rendering devices inoperable, it could disrupt organizational operations, leading to downtime, loss of productivity, and additional costs for remediation and strengthening of cybersecurity measures.
Lumma’s Massive C2 Infrastructure, Over 150 Servers Uncovered
Lumma Infostealer – Phishing – Malvertising – Steganography – Industries/All
Overview & Background
The blog post from Silent Push titled “‘The Dead Russian Poets Society’: Silent Push uses behavioral fingerprinting, content scans and a 128-year old Russian poem to uncover 150+ new ACTIVE Lumma C2 servers and admin panels” details the discovery and analysis of over 150 previously unidentified Lumma C2 servers and their associated control panels. The blog post aims to shed light on Lumma’s delivery methods, the innovative techniques used by Silent Push to uncover these servers, and the unique connection between Lumma’s infrastructure and a historical Russian poet. The blog post analyzes Lumma’s delivery methods, the tactics, techniques, and procedures (TTPs) of the threat actors, and the various indicators of compromise (IOCs) associated with Lumma’s activity.
Lumma, also known as LummaC2, is an information stealer with strong ties to Russian threat activity. It has been available on the dark web as a Malware-as-a-Service (MaaS) platform since 2022. The malware is designed to exfiltrate system data and sensitive information from compromised machines, including browser data, stored credentials, and cryptocurrency data. Lumma’s presence in the cyber threat landscape is significant, with its services being offered for $250 to $1,000 per month. The malware’s advertisement has been spotted on various dark web forums, emphasizing its widespread availability and potential threat to organizations and individuals.
Threat Analysis
Silent Push’s investigation into Lumma’s infrastructure began with a focus on a specific HTML title associated with Lumma C2 activity: “LummaC2 | Вход”. By scanning the entire IPv4 range and collecting granular data, including HTML data, Silent Push was able to form a comprehensive view of the threat actor’s tactics, techniques, and procedures (TTPs). Instead of relying solely on isolated indicators of compromise (IOCs), they executed a content similarity scan based on this HTML title. This approach led to the identification of six Lumma C2 IPs active between January and May 2023. Further analysis revealed an associated HTML header, which, when used as a pivot for a content scan across the entire IPv4 space, resulted in the discovery of 33 new IP addresses used as Lumma C2s.
All these domains were proxied to Cloudflare except for one. By leveraging enriched WHOIS data, Silent Push identified a recurring email address to register some of these domains: levisrogers13@gmail[.]com. Pivoting on this email address revealed 111 new Lumma C2 domains, with 53 still active. Interestingly, some newly identified domains hosted content related to Sergei Yesenin, a Russian poet from the early 20th century. Silent Push hypothesized that Lumma’s administrators might use this content to evade detection. However, further investigation revealed that some domains had transitioned from displaying the Yesenin content to the Lumma control panel. By scanning for domains and IPs displaying the same content, Silent Push identified 71 IOCs, with 15 still active.
Further analysis of these domains revealed a connection to another email address, kippjosephc@gmail[.]com, which was linked to 20 domains associated with Lumma. All of these domains were registered after 19 August 2023 and appeared to be proxied to Cloudflare. Silent Push also identified a subset of domains that were not proxied to Cloudflare. These domains provided additional pivoting options, leading to the discovery of an open directory on one of the subdomains containing a new version of Lumma. This directory revealed the use of steganographic PNG files, suggesting that Lumma employed, or will, steganography to conceal malicious content within embedded image files.
Silent Push’s investigation into Lumma’s delivery methods revealed a multifaceted approach to compromising victims. Lumma’s delivery to a user’s machine depends on the intentions and tactics of the operator who procured the infostealer. Generally, threat actors disseminate Lumma through two primary methods:
- Spear phishing campaigns that feature malicious email attachments. These campaigns leverage social engineering tactics to entice victims into executing the payload.
- Malvertisement (malicious advertising) campaigns and links to cracked software, especially within YouTube video descriptions and gaming content. For instance, Russian threat actors have been observed embedding malware in the video descriptions of hijacked YouTube channels, a method that remains prevalent, especially within the gaming community.
Upon execution, Lumma seeks to access an array of on-device data, including local cryptocurrency wallet data, browser data, and stored credentials. Once Lumma gathers this data, the malware connects with its associated C2 domains, transmitting the information through unencrypted archive files. The malware also retrieves a configuration list from the C2 server, as Lumma does not have the configuration data embedded in itself. Interestingly, Silent Push identified an HTTP POST request that used the user agent ‘TeslaBrowser/5.5’.
The threat actors behind Lumma primarily aim for financial gain by exfiltrating sensitive data from compromised systems, including browser data, stored credentials, and cryptocurrency data, and selling the data on cybercriminal marketplaces. Their objectives encompass targeting systems to obtain unauthorized access and exfiltrate this sensitive data. The capabilities of these threat actors are evident in their ability to deploy Lumma through various delivery methods, including spear phishing and malvertisement campaigns. Additionally, the discovery of steganographic PNGs and their ability to adapt and modify their infrastructure demonstrate their technical proficiency and adaptability.
Risk & Impact Assessment
Lumma poses a pronounced risk to the confidentiality of organizational data, aligning with the primary objectives of its threat actors who seek financial gain. Lumma’s unauthorized access and exfiltration capabilities can lead to significant unauthorized disclosures of sensitive information. However, we can not rule out the risk to data integrity. However, it is highly unlikely and poses a secondary risk. Though not a primary design of Lumma, the potential for disruption to operations or information systems remains a concern, mainly stemming from recovery efforts. In terms of impact, organizations compromised by Lumma can expect material repercussions. Unauthorized access and data exfiltration can lead to substantial financial losses, including potential declines in net sales, revenues, or income from continuing operations. While less likely, the possible modification or loss of data can further exacerbate these financial impacts and erode stakeholder trust.
Victims Targeted by Multiple Ransomware Families and Threat Actors Deploy Data Wiping Malware in Attacks
Ransomware – Data Wiping – Emerging Trends – Industries/All
Overview & Background
The Federal Bureau of Investigation (FBI) released a Private Industry Notification to highlight two emerging ransomware trends and encourage organizations to implement the recommendations to reduce the likelihood and impact of ransomware incidents. The first trend is multiple ransomware attacks on the same victim within a short period. The second trend involves the use of custom data theft, data wiper tools, and malware to pressure victims to negotiate.
Threat Analysis
During these dual deployment ransomware attacks, threat actors deploy two families against victim companies; families include AvosLocker, Diamond, Hive, LockBit, Quantum, and Royal. These families are used in different combinations to encrypt the victim’s data, extract sensitive information, and demand a ransom payment. The second ransomware attack on an already compromised system can be devastating for the victim.
This dual attack scenario is likely, at least in part, carried out by threat actors who are affiliates with multiple ransomware groups. Additionally, our internal data set of victims added to data leak sites shows very few (less than 5) victims impacted by multiple ransomware families. Two possibilities exist to account for this anomaly; threat actors may deploy the second ransomware family if the first family is blocked. The other possibility is that if the victim pays the ransomware (thereby not being listed on the data leak site), they may face an increased chance of being attacked again. The cost of attacking the victim is lower than attacking an unknown victim, and the threat actor knows the victim has paid once.
Throughout early 2022, ransomware groups increased their use of custom data theft, wiper tools, and malware to pressure their victims into negotiating with them. Sometimes, these groups added new code to existing data theft tools to avoid detection or used malware that contained data wipers that remained dormant until a specific time to corrupt data at alternating intervals.
Threat actors are likely employing data wipers to pressure victims into paying the ransom demanded by a set date. If the victim fails to pay the ransom, the data-wiping malware executes and corrupts any data the malware targets. However, it is unknown if data has been corrupted in attacks or if the threat actors are just threatening the use of it. It’s possible that data-wiping malware is only deployed in attacks where the destruction of victim data would not lead to increased focus by international law enforcement agencies. The alarming use of data-wiping malware heightens the need for offline backups to restore any data corrupted by this damaging malware.
Risk & Impact Assessment
The risks associated with these trends can be significant. Threat actors and affiliates’ unauthorized access, disclosure of sensitive data, use of data wipers, and various ransomware families pose significant risks to the confidentiality, integrity, and accessibility of sensitive data and systems. The impact caused by the loss of confidentiality, integrity, and accessibility can be severe and damaging. Organizations could face a substantial material impact on net sales, revenues, or income from continuing operations, resulting in loss of competitive advantage, reputational damage, legal consequences, and disruption of organizational operations, leading to downtime, loss of productivity, and additional costs for remediation and strengthening of cybersecurity measures.
Phishing Campaign Uses Indeed Redirect Vulnerability to Target Senior Executives to Steal Credentials
EvilProxy – Phishing – Session Cookie Theft – Executive Targeting – Finance and Insurance – Real Estate and Rental and Leasing – Manufacturing
Overview & Background
The blog post from Menlo Security titled “EvilProxy Phishing Attack Strikes Indeed” details a sophisticated phishing campaign that targeted executives across various industries, primarily in the Banking and Financial Services, Insurance providers, Property Management and Real Estate, and Manufacturing sectors. This campaign leveraged a phishing kit named ‘EvilProxy’ and exploited an open redirection vulnerability on the job search platform “indeed[.]com” to redirect victims to malicious phishing pages impersonating Microsoft. The blog post highlights this specific phishing campaign, the techniques, tactics, and procedures (TTPs) the threat actors employ, and its potential risks. The blog post analyzes the threat intelligence gathered from various sources, including URLScan, Phishtank, and VirusTotal feeds, to comprehensively understand the campaign.
EvilProxy is a phishing kit that has gained notoriety for its ability to act as a reverse proxy, intercepting requests between the client and the legitimate site. This capability allows it to harvest session cookies, bypassing non-phishing-resistant multi-factor authentication (MFA). EvilProxy is sold on the dark web as a subscription-based offering for a limited time, typically 10, 20, or 30 days, making it accessible to many cybercriminals. Open redirection vulnerabilities, such as the one exploited in the ‘indeed.com’ website, occur when an application redirects users to an untrusted external domain. Threat actors can manipulate this flaw to exploit users’ trust in the redirecting source, leading them to phishing sites or compromised sites serving malware.
Threat Analysis
The primary infection vector for this campaign was a phishing email containing a deceptive link that appeared to originate from ‘indeed.com.’ When victims clicked on this link, they were redirected to a login page masquerading as Microsoft Online due to an exploited open redirection vulnerability in ‘indeed.com.’ The attack sequence involved:
- The victim receives a phishing email containing a link that appears to be from Indeed.
- Upon clicking the link, the victim is redirected to a login page masquerading as Microsoft Online.
- This phishing page, powered by the EvilProxy framework, dynamically fetches content from the legitimate login site.
- The phishing site operates as a reverse proxy, relaying the request to the genuine website.
- EvilProxy intercepts the legitimate server’s requests and responses.
- This interception allows the threat actor to steal session cookies.
- With these stolen cookies, threat actors can log into the legitimate Microsoft Online site, impersonating the victims and bypassing non-phishing-resistant MFA.
In this attack, users clicked on a URL, believing they were being directed to ‘indeed.com’ or one of its subdomains. However, parameters supplied to the subdomain ‘t[.]indeed.com’ redirected the user to another target. This redirection led the user to the phishing page. The threat actors utilized the EvilProxy phishing kit, which acted as a reverse proxy, performing an adversary-in-the-middle attack by stealing user session cookies, thereby helping to bypass MFA.
The phishing pages, impersonating the Microsoft Online login page, were hosted on nginx servers capable of acting as reverse proxies and had the subdomain “.lmo.” These servers fetched dynamic content, such as login pages, and served as adversaries in the middle by intercepting requests and responses between the victim and the legitimate site. This interception facilitated the harvesting of session cookies. Menlo Security attributed the use of EvilProxy to several observed artifacts. These included common URI paths found in the phishing pages and the utilization of Microsoft’s Ajax CDN for dynamic fetching and rendering of JavaScript content. Specific strings in the URI paths and unique POST requests containing victims’ email addresses and session identifiers indicated EvilProxy’s involvement. Another distinguishing feature was the use of the open-source FingerprintJS library for browser fingerprinting, particularly the Domblockers module, which identified elements being blocked by browsers.
The primary intention behind the phishing campaign is likely financial gain, as evidenced by the theft of session cookies. Threat actors can sell these stolen cookies to other threat actors to monetize their malicious activities. However, another intention (although unlikely) could be intelligence collection, evidenced by targeting senior executives across specific industries. The threat actors’ main objective was to target the systems and data accessible by C-suite employees and other key executives. While EvilProxy employs sophisticated methods, it’s worth noting that the threat actors almost certainly purchased access for a limited time. Furthermore, EvilProxy provides comprehensive videos and tutorials, so even threat actors with basic computer knowledge can use the kit. However, they had the resources and skills to purchase server access and deploy Docker containers provided by EvilProxy.
Risk & Impact Assessment
The primary risk from this phishing campaign is the loss of confidentiality. The theft of session cookies provides unauthorized access to sensitive data within victims’ Microsoft accounts, directly threatening the confidentiality of personal and corporate information. Given the threat actors’ likely intermittent access to the EvilProxy tool due to the actors’ access expiring. If the current campaign is successful and the threat actors repurchase access, there is a likely chance that organizations within the targeted sectors could be impacted in future campaigns. The time needed to process and monetize the stolen cookies will likely influence the timeframe of a future campaign. The threat actors’ strategic approach suggests that if they deem the campaign profitable and manageable, they might continue to target organizations in the same sectors in subsequent campaigns. The risk is further accentuated by the stolen data being leveraged for subsequent malicious activities, amplifying the threat landscape for the affected organizations.
In terms of impact, organizations targeted by this campaign face material consequences. Unauthorized access to sensitive data can lead to significant financial repercussions, especially if the data pertains to corporate secrets, proprietary information, or personal details of high-ranking officials. The potential exfiltration of this data poses a direct financial threat and damages the organization’s reputation, trustworthiness, and market standing. The ripple effect of such a breach can influence net sales, revenues, and income from continuing operations, especially if the breach becomes public knowledge or if the data is used maliciously against the organization.
New Malware-as-a-Service, BunnyLoader, Emerges on the Scene
BunnyLoader – Infostealer – Malware Loader – Malware-as-a-Service – Industries/All
Overview & Background
The blog post from Zscaler titled “BunnyLoader, the newest Malware-as-a-Service” details the technical intricacies and capabilities of BunnyLoader, a new entrant in the Malware-as-a-Service landscape. The blog post aims to shed light on the malware’s functionalities, its evasion techniques, and its communication with its command and control servers. The blog post analyzes the malware’s behavior upon execution, its various tasks, such as keylogging, data theft, remote command execution, and the systems it targets.
Malware-as-a-Service (MaaS) refers to a business model where cybercriminals offer malware services for rent or sale, often on the dark web. This model allows even non-technical individuals to launch sophisticated cyberattacks without developing malware themselves. Over the years, MaaS has evolved, with various offerings ranging from ransomware to banking trojans available for purchase. The rise of MaaS platforms has lowered the barriers to entry for cybercrime, enabling a broader range of actors to engage in malicious activities. Historically, MaaS has roots in the broader trend of commoditization of cybercrime, where tools and services are readily available, making it easier for criminals to execute attacks and monetize their efforts.
Threat Analysis
BunnyLoader, upon execution, performs a series of actions to ensure its persistence and evade detection. It starts by creating a new registry value named “Spyware_Blocker” in the Run registry key, hides its window, and creates a mutex named “BunnyLoader_MUTEXCONTROL.”
BunnyLoader employs a range of anti-VM checks to detect and evade virtualized environments. It checks for specific modules associated with known security solutions and queries the system to detect virtual machines. Additionally, it checks for Docker containers and specific sandbox usernames. If it identifies a sandbox environment, it throws an error message to mislead the user.
The malware communicates with its command and control (C2) server, sending an HTTP registration request containing details about the infected system. Once registered, it waits for tasks from the C2 server. These tasks range from downloading and executing payloads, running keyloggers, and stealing information from web browsers, cryptocurrency wallets, VPNs, and messaging applications to remote command execution.
Furthermore, BunnyLoader has a clipper module that monitors the victim’s clipboard for cryptocurrency addresses, replacing them with addresses controlled by the threat actor. This functionality targets cryptocurrencies, including Bitcoin, Monero, Ethereum, and Litecoin.
The developer behind BunnyLoader has crafted a tool with clear intentions of monetization by offering the malware as a service to other threat actors. Designed with a broad appeal, BunnyLoader boasts a range of functionalities, from evasion techniques to data theft, aiming to cater to both individual cybercriminals and organized groups. This versatility, combined with the developer’s advanced skills, infrastructure management capabilities, and awareness of security solutions, positions BunnyLoader as a formidable tool in the cybercrime landscape.
Users of BunnyLoader will likely be driven by financial gain, leveraging the malware’s capabilities to steal funds or sensitive data. With functionalities that allow for targeting individual systems, especially those involved in cryptocurrency transactions, users seek to compromise various platforms. Their ability to deploy BunnyLoader, bypass specific security solutions, and dynamically interact with its command and control server showcases the depth of malicious capabilities at their disposal.
Risk & Impact Assessment
BunnyLoader poses a pronounced risk to the confidentiality of data and information systems. Its adeptness in stealing information from various sources, including web browsers, cryptocurrency wallets, VPNs, and messaging applications, underscores a heightened likelihood of unauthorized access and disclosure of sensitive information. The malware’s clipper module, designed to replace cryptocurrency addresses, further amplifies this risk, potentially leading to financial repercussions for affected individuals or entities. In terms of impact, organizations compromised by BunnyLoader can anticipate material impact, especially if sensitive customer data or proprietary information is exfiltrated. Such breaches could erode trust, leading to a decline in customer confidence and, subsequently, a tangible reduction in net sales, revenues, or income from continuing operations. The ripple effect could extend to reputational damage, legal ramifications, and increased costs associated with remediation and bolstering cybersecurity measures.
Latest Additions to Data Leak Sites
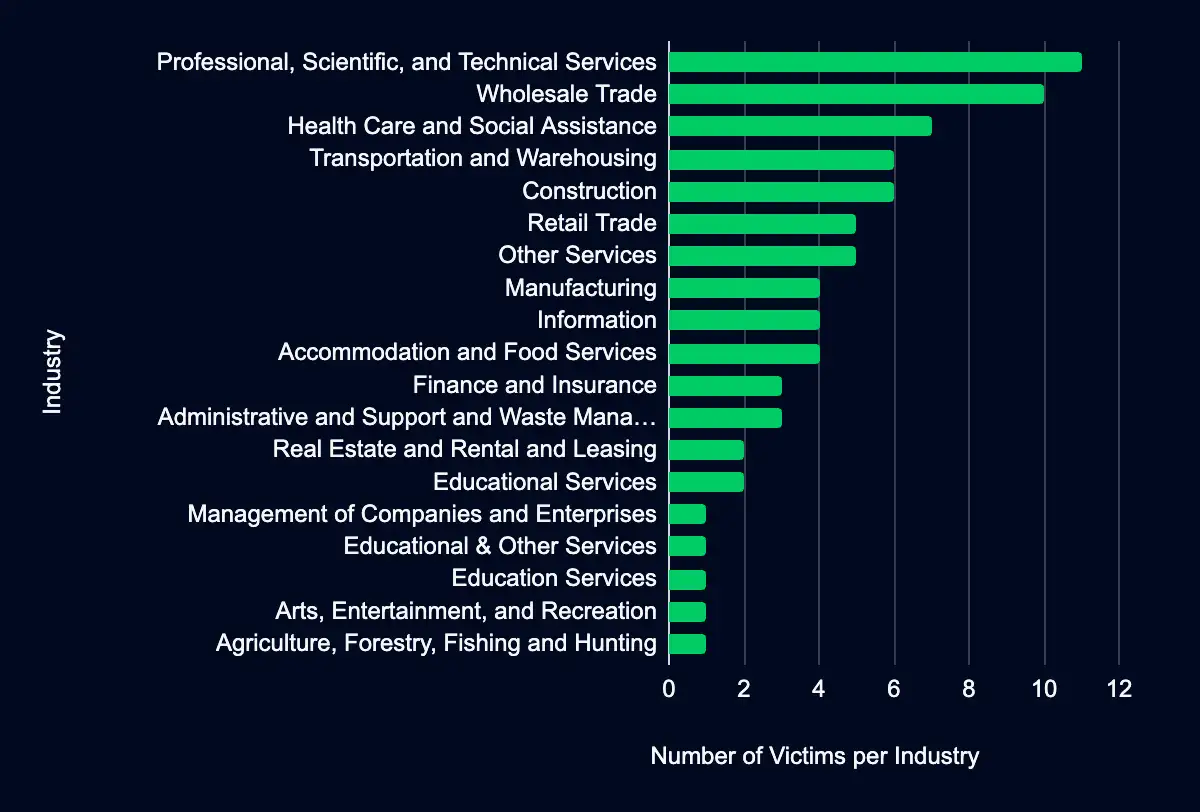
Professional, Scientific, and Technical Services – Wholesale Trade – Health Care and Social Assistance – Transportation and Warehousing – Construction
In the past week, monitored data extortion and ransomware threat groups added 77 victims to their leak sites. Of those listed, 46 are based in the USA, 8 in the UK, 4 in Germany, 3 in the Netherlands, and 2 in Spain. Professional, Scientific, and Technical Services was the most targeted industry, with 11 victims. This industry is followed by 10 in Wholesale Trade, seven in Health Care and Social Assistance, and six each in Transportation and Warehousing and Construction.
This information represents victims whom cybercriminals may have successfully compromised but opted not to negotiate or pay a ransom. However, we cannot confirm the validity of the cybercriminals’ claims.
CISA Adds 5 CVEs to its Known Exploited Vulnerabilities Catalog
JetBrains CVE-2023-42793 – Microsoft CVE-2023-28229 – Arm CVE-2023-4211 – Google CVE-2023-5217 – Red Hat CVE-2018-14667
Within the past week, CISA added five CVEs to the catalog, affecting JetBrains, Microsoft, Arm, Google, and Red Hat products. Threat actors can exploit these vulnerabilities for code execution, limited SYSTEM privileges, exploit heap corruption, and gain access to already freed memory. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action occur between 19 and 25 October 2023.
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE | Vendor/Project | Product | Description | Due Date |
|---|---|---|---|---|
| CVE-2023-42793 | JetBrains | TeamCity | JetBrains TeamCity contains an authentication bypass vulnerability that allows for remote code execution on TeamCity Server. | 2023-10-25 |
| CVE-2023-28229 | Microsoft | Windows CNG Key Isolation Service | Microsoft Windows Cryptographic Next Generation (CNG) Key Isolation Service contains an unspecified vulnerability that allows an attacker to gain specific limited SYSTEM privileges. | 2023-10-25 |
| CVE-2023-4211 | Arm | Mali GPU Kernel Driver | Arm Mali GPU Kernel Driver contains a use-after-free vulnerability that allows a local, non-privileged user to make improper GPU memory processing operations to gain access to already freed memory. | 2023-10-24 |
| CVE-2023-5217 | Chrome libvpx | Google Chrome libvpx contains a heap buffer overflow vulnerability in vp8 encoding that allows a remote attacker to potentially exploit heap corruption via a crafted HTML page. | 2023-10-23 | |
| CVE-2018-14667 | Red Hat | JBoss RichFaces Framework | Red Hat JBoss RichFaces Framework contains an expression language injection vulnerability via the UserResource resource. A remote, unauthenticated attacker could exploit this vulnerability to execute malicious code using a chain of Java serialized objects via org.ajax4jsf.resource.UserResource$UriData. | 2023-10-19 |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share