February 02, 2022
Prepared by Deepwatch Threat Intel Team
Key Points:
- Proof-of-concept code was publicly disclosed for a Local Privilege Escalation (LPE) vulnerability in Windows 10, tracked as CVE-2022-21882, and affects the Win32k.sys driver.
- Threat actors with limited access to a compromised device can utilize this vulnerability to quickly elevate privileges, allowing them to spread laterally inside the network, create new administrator users, and run privileged commands.
- According to the security researcher credited with disclosing the vulnerability to Microsoft, the vulnerability has already been exploited by advanced persistent threat (APT) actors.
- Deepwatch Threat Intel Teams assess with high confidence that threat actors are likely to use the publicly available exploit code for CVE-2022-21882 to escalate privileges on systems in which they have already initially compromised. Given the vulnerability affects Windows 10, the Deepwatch Threat Intel Team advises customers to install updates as soon as possible, prioritizing vulnerable internet-exposed systems.
- The Deepwatch Vulnerability Management team is currently aware of and monitoring the vulnerability mentioned above. We will continue to provide guidance and remediation recommendations to our customers.
Summary
According to Microsoft, a recently patched vulnerability in Windows 10 had proof-of-concept (PoC) code publicly disclosed. Tracked as CVE-2002-21882 CVSS score 7.0, the vulnerability means that a “local, authenticated attacker could gain elevated local system or administrator privileges through a vulnerability in the Win32k.sys driver.” The author of the exploit code, Gil Dabah, claims that he found the vulnerability two years ago but decided not to disclose it to Microsoft due to difficulties in how Microsoft handles bug bounty awards.
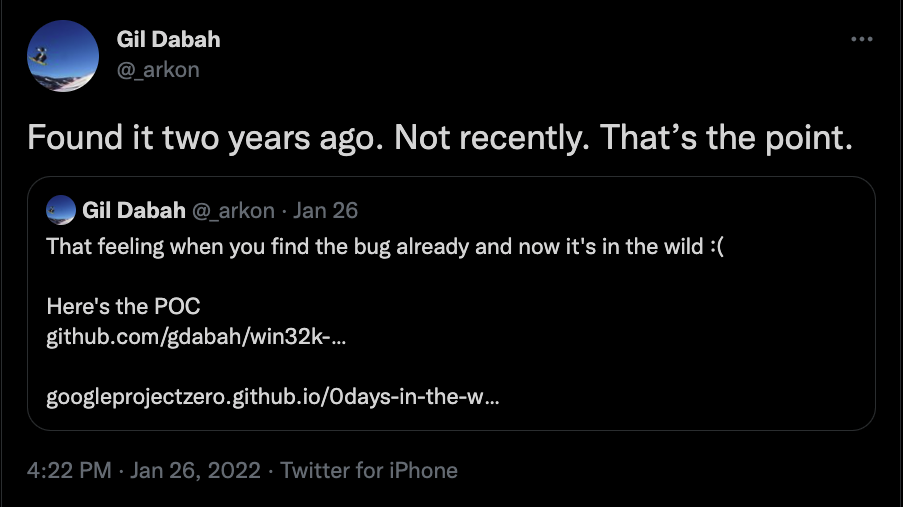
Numerous security experts, including Will Dormann, a vulnerability analyst with the CERT/CC, confirmed that the exploits function as intended.
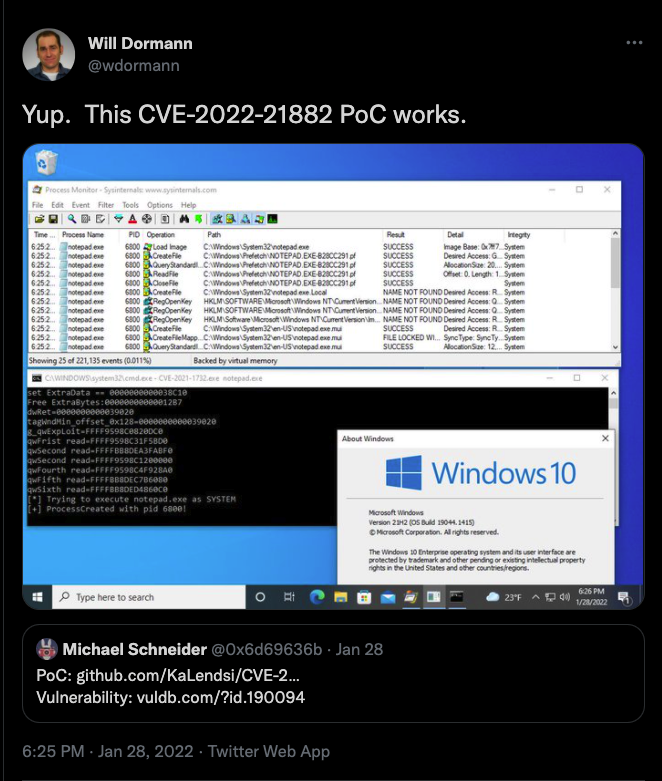
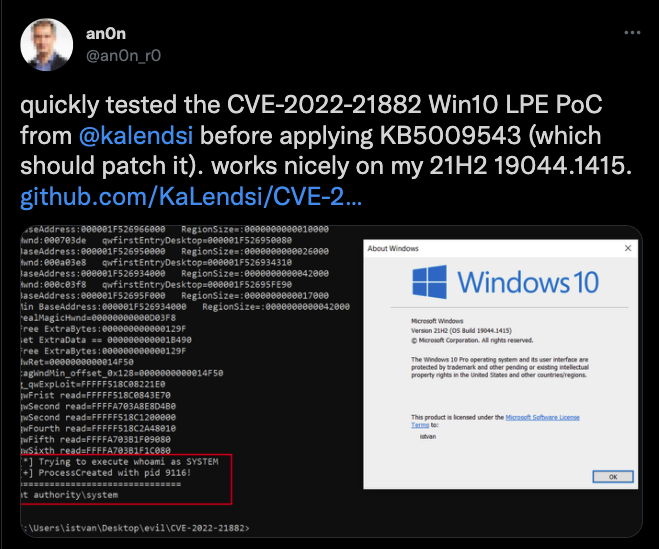
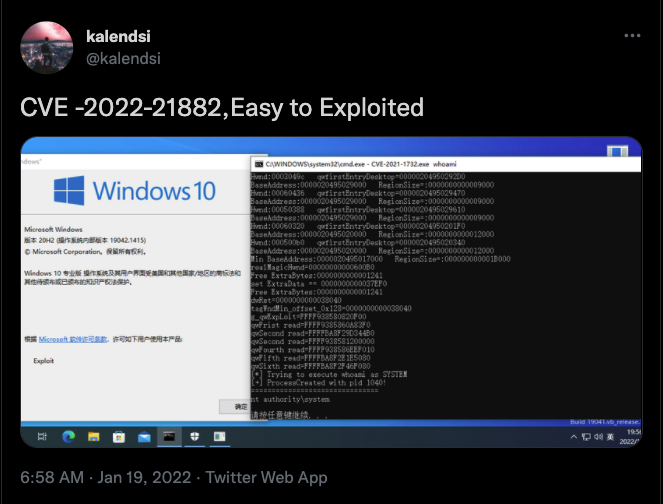
What is the Impact of this Vulnerability?
Microsoft states in their advisory that “A local, authenticated attacker could gain elevated local system or administrator privileges through a vulnerability in the Win32k.sys driver.”
Microsoft accredits security researcher RyeLv with the find. According to RyeLv’s disclosure, the win32k elevation of privilege vulnerability enables a threat actor to “call the relevant GUI API at the user_mode to make the kernel call like xxxMenuWindowProc, xxxSBWndProc, xxxSwitchWndProc, xxxTooltipWndProc, etc.”
RyeLv further states that “These kernel functions will trigger a callback xxxClientAllocWindowClassExtraBytes. Attacker can intercept this callback through hook xxxClientAllocWindowClassExtraBytes in KernelCallbackTable,and use the NtUserConsoleControl method to set the ConsoleWindow flag of the tagWND object, which will modify the window type.”
According to RyeLv, advanced persistent threat (APT) actors have already exploited this vulnerability.
Customers should keep in mind that while this exploit requires a local authenticated user to perform this attack, that does not mean it should not be prioritized. Threat Actors could use this vulnerability to quickly escalate privileges for lateral movement purposes. Therefore, remediation of this vulnerability should definitely be near the top of the list of priorities. ~ Rob Hundley, Manager, Deepwatch Vulnerability Management
What Versions are Affected?
- Microsoft Windows 10 versions: 1809, 1909, 20H2, 21H1, and 21H2.
- Microsoft Windows 11.
- Microsoft Windows Server 2019.
- Microsoft Windows Server 2022.
What Do I Need to Do?
Given the vulnerability affects Windows 10, the Deepwatch Threat Intel Team advises customers to install updates as soon as possible, prioritizing vulnerable internet-exposed systems.
Deepwatch Threat Intelligence Outlook
Deepwatch Threat Intel Teams assess with high confidence that less sophisticated threat actors are likely to use the publicly available exploit code for CVE-2022-21882 to escalate privileges on systems in which they have already initially compromised. However, given the vulnerability affects Windows 10, the Deepwatch Threat Intel Team advises customers to install updates as soon as possible, prioritizing vulnerable internet-exposed systems.
The vulnerability management team is currently aware of and monitoring the vulnerability mentioned above. We will continue to provide guidance to our customers and remediation recommendations.
↑
Share