Published March 02, 2022
Prepared by Deepwatch Threat Intel Team
Key Points:
- NVIDIA confirmed that a threat actor stole employee credentials and proprietary information. They also stated there was no evidence that ransomware was involved or that the hack was related to the Ukraine-Russia conflict.
- Shortly after the data breach became public on February 23, a data extortion threat actor named Lapsus$ claimed it took 1TB of data and leaked a 20GB archive.
- To further extort NVIDIA, Lapsus$ claimed they would release a data archive for 30 series GPUs if NVIDIA did not update the GPUs to remove NVIDIA’s lite hash rate limitation, allowing graphics cards to maximize the mining capacity of a GPU.
- Deepwatch Threat Intel Team estimates with moderate confidence that Lapsus$ and data extortion threat actors, in general, will likely increase attacks as threat actors anticipate that organizations will be distracted by the current tensions between Ukraine and Russia dominating headlines. Therefore, it is recommended that customers patch all systems with a priority placed on known exploited vulnerabilities, train users to recognize and report phishing attempts, and finally, use multi-factor authentication.
Summary
NVIDIA, the chipmaker, disclosed on March 1 that its network had been compromised in a cyberattack last week, giving threat actors access to proprietary data and employee login information. A data extortion group known as Lapsus$ posted a Telegram message shortly after the incident was made public, claiming to have 1TB of data taken from the GPU designer.
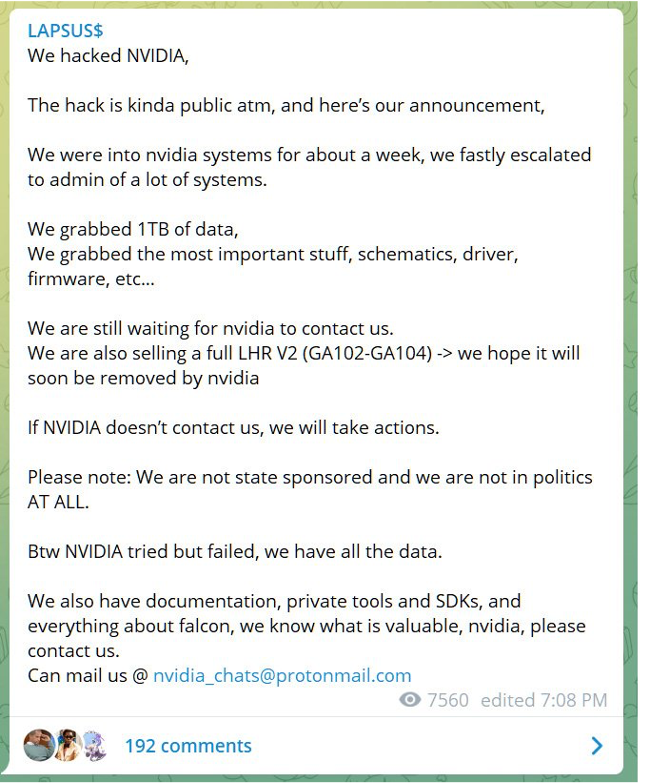
Source: Bleeping Computer
In a statement to BleepingComputer, NVIDIA says that on,
“On February 23, 2022, NVIDIA became aware of a cybersecurity incident which impacted IT resources. Shortly after discovering the incident, we further hardened our network, engaged cybersecurity incident response experts, and notified law enforcement.
We have no evidence of ransomware being deployed on the NVIDIA environment or that this is related to the Russia-Ukraine conflict. However, we are aware that the threat actor took employee credentials and some NVIDIA proprietary information from our systems and has begun leaking it online. Our team is working to analyze that information. We do not anticipate any disruption to our business or our ability to serve our customers as a result of the incident.
Security is a continuous process that we take very seriously at NVIDIA – and we invest in the protection and quality of our code and products daily.”
To further bolster their claims, Lapsus$ released an archive of 20GB of data that supposedly contains “source code and highly confidential/secret data from various parts of NVIDIA gpu driver. Falcon, LHR, and such.”
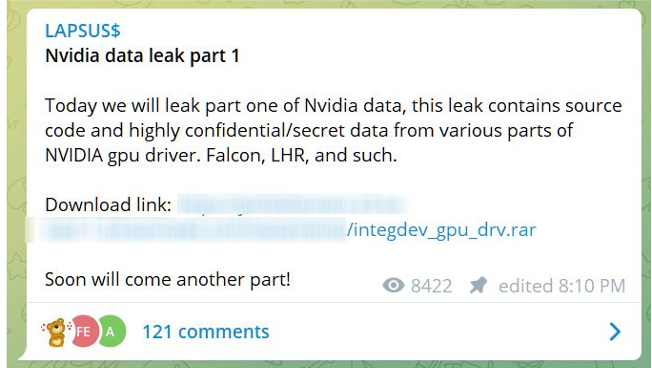
Source: Bleeping Computer
One of the messages from Lapsus$ contained a claim that the firm hacked back to encrypt their virtual machine with the data. Lapsus$ claims that NVIDIA accessed a VM because it was enrolled in Mobile Device Management which gave them access. To date, NVIDIA has not made any statements regarding hacking back.
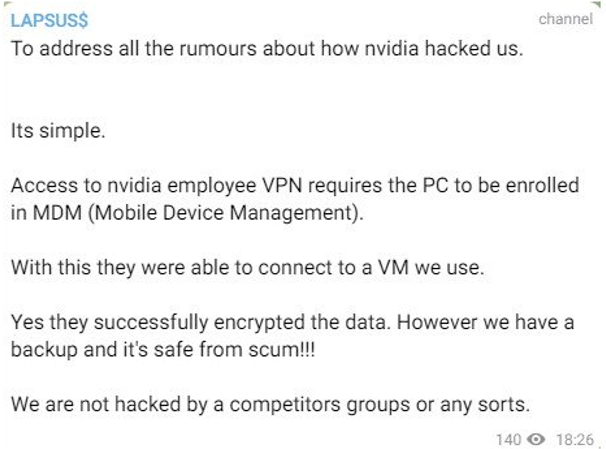
Source: Bleeping Computer
In their statements, they are extorting NVIDIA by threatening to release the 30 series hardware folder, “hw folder,” if NVIDIA does not “push an update for all 30 series firmware that remove lhr limitations.” Nvidia’s lite hash rate technology (LHR) allows graphics cards to minimize the mining capacity.
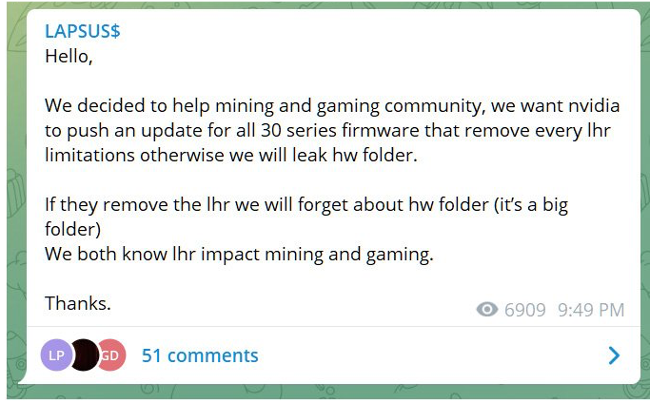
Source: Bleeping Computer
Deepwatch Threat Intelligence Outlook
Deepwatch Threat Intel Team estimates with moderate confidence that Lapsus$ and data extortion threat actors, in general, will likely increase attacks as threat actors anticipate that organizations will be distracted by the current tensions between Ukraine and Russia dominating headlines. As the conflict in Ukraine escalates, customers must remain vigilant against all cyberthreats, and data extortion remains a prominent threat to all customers. Therefore, it is recommended that customers patch all systems with a priority placed on known exploited vulnerabilities, train users to recognize and report phishing attempts, and finally, use multi-factor authentication.
Author: Eric Ford
↑
Share