Explore Our Platform
Deepwatch Managed Security Platform
Technology, People, and Processes Designed to Build Cyber Resilience.
We're Back at Black Hat! Let's Connect
Explore Our Platform
Technology, People, and Processes Designed to Build Cyber Resilience.
Our Approach
The Deepwatch Managed Security Platform combines the technology, people, and processes for a hybrid, collaborative approach to measuring and improving cyber resilience.
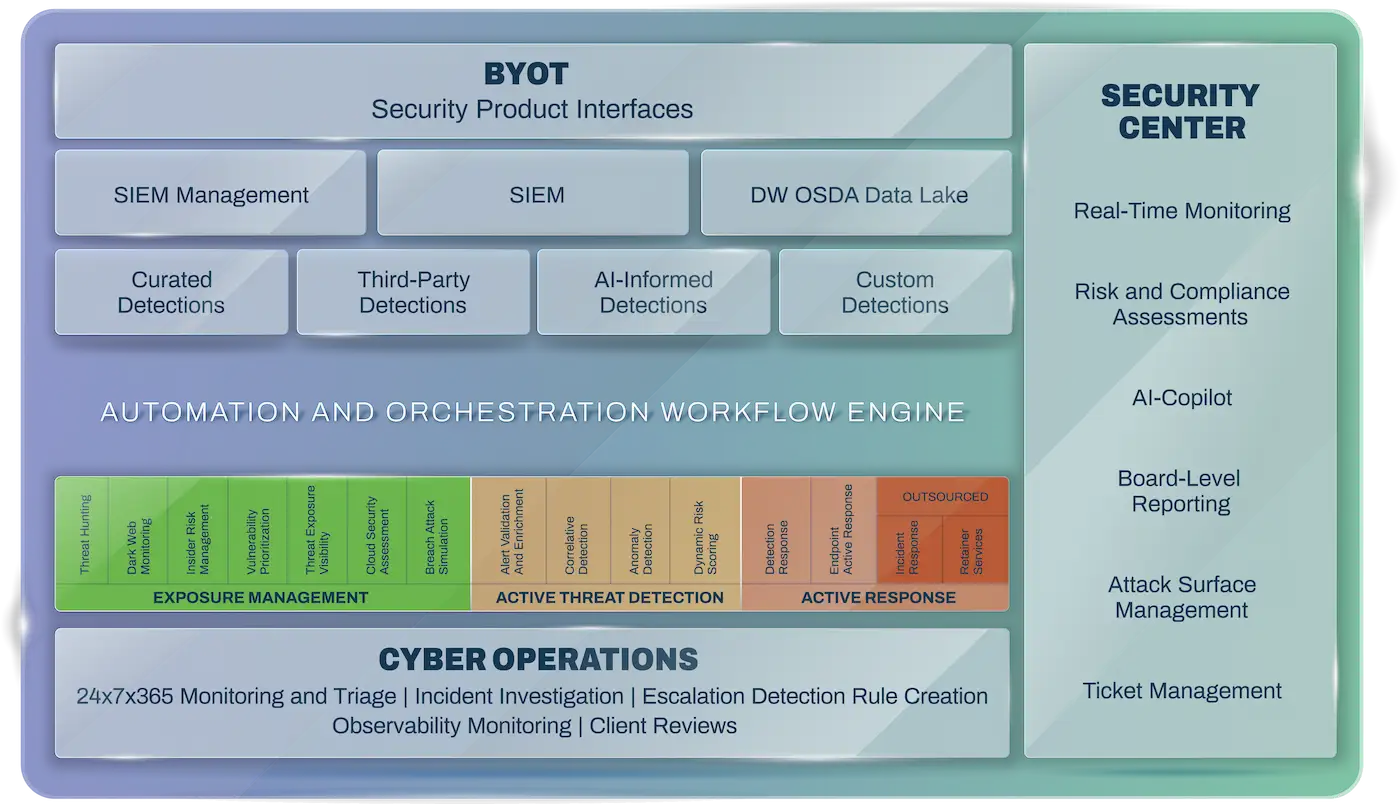
A security program based on your specific risk tolerances, desired security outcomes, and available resources.
Industry veterans and former CISOs who redefined the managed security industry.
A team of experts you will know by name who help you monitor, manage, and respond to threats 24/7/365.
A true partnership of engagement, responsibility, and collaboration to achieve your desired outcomes.
Advanced correlation and dynamic risk threat scoring improve detection 10X and enable more precise responses.
The most advanced dynamic risk scoring engine reduces false positives by 98%, saving you time, money, and alert fatigue.
Our patented Deepwatch Security Index helps you continuously improve your security posture.
Make your existing tools more effective and integrate with best-in-class solutions for improved ROI.
Payback in less than 6 months from economies of scale, network effect, technology, and personnel savings adding to more than 432% per year.
Confidently configure and deploy endpoint prevention policies and improve response.
Deeper insights into your organization's unique requirements, expanding response capabilities.
Ready for Guardians You Can Trust?
Meet with us to discuss your threats, vulnerabilities, and challenges and discover how Deepwatch can stand watch over what matters most.