What You Need to Know
- Microsoft released a security update for a Windows Support Diagnostic Tool vulnerability (CVE-2022-34713) after initial pushback on not fixing the vulnerability a security researcher reported to them in late 2019. According to the advisory, threat actors are actively exploiting this vulnerability.
- The vulnerability could allow a threat actor to store a file in any location on the file system according to the current user’s permissions. By placing the malicious file into the Windows Startup folder, the threat actor could execute code, which the operating system would run the next time the victim logged in.
- Recommendations include updating Windows to the latest version and restricting the ability of end-users from opening .diagcab files.
- Deepwatch Squads are identifying customers that this vulnerability may impact and evaluating the detection strategy for this exploitation.
Overview
On August 9, Microsoft released a patch for a vulnerability, tracked as CVE-2022-34713, that a security researcher initially reported to the company in December 2019. Six months later, on June 1, 2020, Microsoft closed the case stating, “we will not be fixing this vulnerability in the current version and we are closing this case.”
Two years later, Microsoft reassessed the case due to their updated “Windows bug bar” and determined that the vulnerability met the security update criteria.
In the security advisory, Microsoft stated that active exploitation has been detected for the vulnerability.
Vulnerability Details
The vulnerability, informally known as “DogWalk” and now tracked as CVE-2022-34713, affects Microsoft’s Windows Support Diagnostic Tool and scores a 7.8 on the CVSS scale, garnering a high rating (CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H).
Microsoft’s Windows Diagnostic Tool allows users to download diagnostic packages–.diagcab–from the internet. When a user downloads a package, integrity checks are performed. Still, an implementation flaw in this process could let a threat actor store any file in any location on the file system (according to the current user’s rights) before the package’s integrity checks. By placing a file into Windows’ Startup folder, the threat actor could execute code, which the operating system would then run the next time the victim logged in.
Affected Products
This vulnerability affects the following Microsoft products:
- Windows Server 2008, 2012, 2016, 2019, and 2022
- Windows RT 8.1
- Windows 7, 8.1, 10, and 11
Active Exploitation
According to the advisory, exploitation requires a threat actor to convince a user to open a “specially crafted file” via email attachments or web-based, where a threat actor creates a web site or compromises a website to host the file.
At this time, Microsoft has not provided further details of active exploitation.
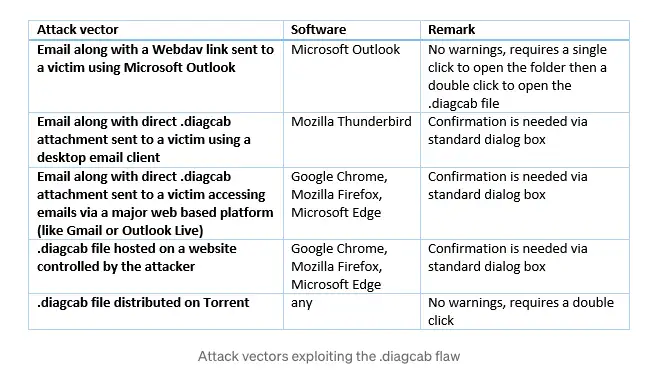
However, according to Microsoft, Outlook and Internet Explorer are secure. These two applications block .diagcab files if the file originates from the internet.
According to the researcher who reported the vulnerability to Microsoft, “neither Gmail nor Outlook Live blocked .diagcab files at all…Other popular products like Google Chrome, Mozilla Firefox or Thunderbird simply pop up the standard open and execute dialog box when they see .diagcab files. Actually, even Microsoft Edge, using one of these browsers for reading emails on a web based platform is probably the biggest attack vector of this vulnerability.”
According to the researcher, the following are possible attack vectors (figure 1):
One possible attack scenario could resemble how TA413 exploited the Follina vulnerability, another vulnerability affecting MSDT, as reported by Proofpoint in May (figure 2).
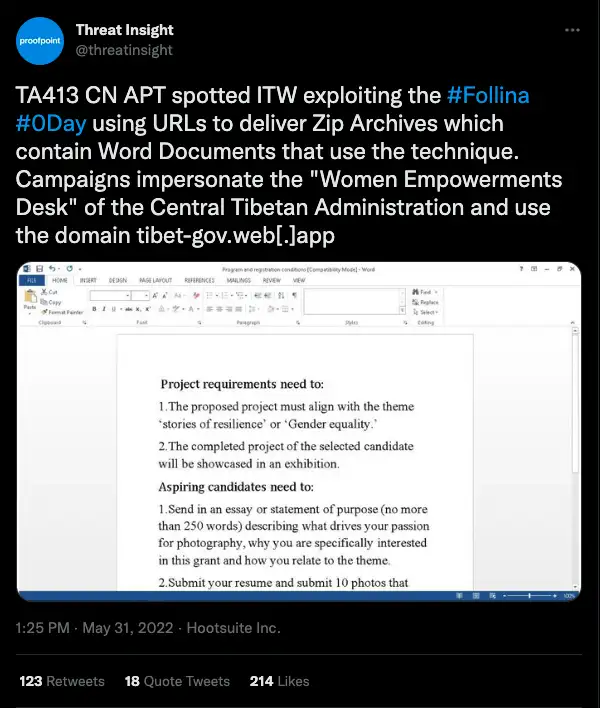
This scenario involved the adversary–TA413–sending Zip archives masquerading as a Tibetan administration department to targeted individuals that contained a Word doc that exploited the Follina vulnerability.
Analyst Note: Threat actors are likely exploiting this vulnerability via email platforms where they’re sending phishing emails with a link to a web site that hosts the malicious file intending to compromise executive and senior-level email accounts for espionage-related activities. Additionally, threat actors could exploit this vulnerability by sending a .diagcab file attachment to recipients using a web-based email platform.
What You Need to Do
Deepwatch Threat Intel Team recommends that customers and organizations update Windows to the latest version, which you can find here.
Additionally, restricting users from opening .diagcab files and implementing the attack vector TTPs listed above in your phishing awareness and simulation exercises could reduce the risk of this threat.
Be On the Lookout (BOLO) and Monitor Logs For:
- Email attachments or linked downloads (web proxy data) containing .diagcab files.
- Outbound web proxy data with WebDAV useragent (specifically when requesting a .diagcab file).
- msdt.exe running .diagcab files (requires 4688 process logs with command line logging enabled).
- msdt.exe may be a child process of explorer.exe or winword.exe (not an exhaustive list) depending on the attack vector.
- It may also be possible to detect malicious .diagcab files being launched by msdt.exe from a remote WebDAV location (ex. a user opens the WebDav Link from a malicious email) by monitoring for the following:
- EventCode 4688 events with parent process “svhost.exe” spawning “rundll32.exe C:\Windows\system32\davclnt.dll…” (truncated) followed by a remote WebDAV location.
- Example Splunk Query
- index=wineventlog EventCode=4688 (parent_process=”svchost.exe” new_process=”*rundll32.exe*” commandline=”*davclnt.dll*”) OR (new_process=”*msdt.exe*” “*diagcab*”)
- The unexpected addition of Startup items.
Conclusion
This is yet another vulnerability in Microsoft’s Windows Support Diagnostic Tool and highlights the importance of end-user cybersecurity awareness training and ensuring machines are up to date.
Threat actors could target customers and organizations by sending phishing emails with links to an adversary-controlled website hosting a malicious file to execute code on the victim machine to deploy additional malware or tools, harvest email account credentials for sale on dark web markets or later compromise.
Customers and organizations are encouraged to implement the guidance and recommendations set out in the “What You Need to Do” section above.
Deepwatch, a leader in managed security services, protects our customers from ever-increasing cyber threats 24/7/365. Powered by curated threat intelligence produced by our Threat Intel Team, our cloud-based security operations platform provides the industry’s most comprehensive detection and automated response to cyber threats. In addition, dedicated experts provide our tailored guidance to mitigate risk and measurably improve security posture. As a result, hundreds of organizations, from Fortune 100 to mid-sized enterprises, trust Deepwatch to protect their business. Visit www.deepwatch.com to learn more.
↑
Share