CozyBear Exploits JetBrains TeamCity, Qakbot Gets Regifted, Phishing Campaign Uses Publicly Available Tool Predator, and an Unexpected Gift from CISA
This week: Russian APT CozyBear exploits JetBrains TeamCity, Qakboit gets regifted even after takedown, a phishing campaign uses Predator to evade security measures and directly target users, the naughty list of ransomware victims grows, and CISA gives an unexpected gift– no new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Can’t Return this Christmas Present: CozyBear’s Large-Scale Exploitation of JetBrains TeamCity (CVE-2023-42793)
- Regifted: Qakbot Resurfaces in New Phishing Campaign
- Don’t Unwrap this Present: Phishing Campaign Employs Publicly Available Tool to Bypass Detection
- You Don’t Want to Be on This Naughty List: Latest Additions to Data Leak Sites
- Finally, a Present We Wanted: CISA Reports No New CVEs Added to its Known Exploited Vulnerabilities Catalog
Can’t Return this Christmas Present: CozyBear’s Large-Scale Exploitation of JetBrains TeamCity (CVE-2023-42793)
JetBrains TeamCity CVE-2023-42793 – CozyBear – GraphicalProton – Backdoor – Rsockstun – Reverse Proxy – Vulnerability Exploitation – Privilege Escalation – Manufacturing – Professional, Scientific, and Technical Services – Information – Public Administration – Educational Services – Other Services
Threat Analysis
CozyBear, attributed to the Russian Foreign Intelligence Service (SVR), has been exploiting CVE-2023-42793 in a large-scale operation since September 2023. Software developers use TeamCity software to manage and automate software compilation, building, testing, and releasing. CVE-2023-42793 impacts JetBrains TeamCity versions before 2023.05.4. Successful exploitation allows threat actors to bypass authentication, leading to remote code execution (RCE).
Currently, there are a limited number of victims where CozyBear conducted post-exploitation activity to escalate privileges, move laterally, deploy additional backdoors, and take other steps to ensure persistent and long-term access to the compromised network environments, indicating that CozyBear has not used the access afforded by CVE-2023-42793, like their compromise of SolarWinds and its customers in 2020, where they modified the software source code to access downstream customers.
The authoring agencies of the Joint Cybersecurity Advisory (CSA) assess that CozyBear could benefit from access to victims, particularly by allowing the threat actors to compromise the software development pipeline. JetBrains issued a patch for this CVE in mid-September 2023, limiting CozyBear’s operation to exploiting unpatched, Internet-reachable TeamCity servers. While the authoring agencies assess that CozyBear has not yet used its access to software developers to access customer networks, they are likely still in the preparatory phase of its operation. Access to the software development pipeline allows CozyBear to establish hard-to-detect command and control (C2) infrastructure.
As a result of this latest CozyBear activity, the authoring agencies have identified a few dozen compromised companies, with over a hundred compromised devices, in the United States, Europe, Asia, and Australia. However, they assess this does not represent the complete set of compromised organizations. Furthermore, besides having an unpatched, Internet-reachable JetBrains TeamCity server, there does not appear to be a pattern to the victims, leading to the assessment that CozyBear’s exploitation of these victims’ networks was opportunistic and not necessarily a targeted attack.
Identified victims included:
- An energy trade association.
- Companies that provide software for billing, medical devices, customer care, employee monitoring, financial management, marketing, sales, and video games.
- Hosting companies, tools manufacturers, and small and large IT companies.
Technical Analysis
Initial Access
CozyBear began exploiting CVE-2023-42793 in Internet-facing JetBrains TeamCity servers in late September 2023. This exploitation usually resulted in code execution with elevated privileges, granting CozyBear a foothold in the network environment. It’s unknown if CozyBear is currently exploiting any other initial access vector to JetBrains TeamCity.
Host Reconnaissance
Once gaining access, CozyBear used various basic, built-in commands, such as whoami, nltest, wmic, and PowerShell, to perform host reconnaissance. Additionally, CozyBear exfiltrated files to gain valuable information about the host system, such as the kernel image (ntoskrnl.exe), SQL Server executable files, and Visual Studio files.
To avoid detection, CozyBear used an open-source project called “EDRSandBlast” to remove the protected process light (PPL) protection, which controls and protects running processes from infections. This technique is known as Bring Your Own Vulnerable Driver (BYOVD). BYOVD allows the group to disable or kill endpoint detection and response (EDR) and antivirus (AV) software. Once the protection is removed, CozyBear injected code into AV/EDR processes for a small subset of victims. CozyBear also ran executables like Mimikatz in memory.
Defense Evasion
In several cases, CozyBear avoided detection of its backdoors by replacing a legitimate Zabbix or Webroot antivirus software DLL with one containing the GraphicalProton backdoor, abusing a DLL hijacking vulnerability in each DLL. They also created a backdoor by modifying and copying publicly available source code for an open-source application developed by Microsoft named vcperf. After execution, the backdoored vcperf dropped several DLLs to disc, including the GraphicalProton backdoor.
GraphicalProton primarily leverages cloud services like OneDrive and Dropbox for communication, using randomly generated BMP files to exchange data. This method involves compressing and encrypting data, embedding it within BMP files, and using these cloud services as primary and backup communication channels. GraphicalProton’s execution involves gathering environment information, such as active connections, processes, and user/host/domain names.
To enhance stealth, CozyBear has employed various obfuscation techniques with GraphicalProton. These techniques include wrapping the backdoor in layers of encryption. Additionally, a variant of GraphicalProton foregoes cloud-based C2 channels in favor of HTTP requests, using a re-registered expired domain with a dummy WordPress site for legitimacy.
Privilege Escalation & Persistence
CozyBear used multiple techniques to facilitate privilege escalation, including WinPEAS, NoLMHash registry key modification, and the Mimikatz tool.
CozyBear relied on scheduled tasks to secure persistent execution of GraphicalProton. Depending on CozyBear’s privileges, their executables were stored in the temp, System32, or WinStore directories. CozyBear made all modifications using the schtasks.exe binary, passing multiple variants of arguments to schtasks.exe. To secure long-term access to the environment, CozyBear used the Rubeus toolkit to craft Ticket Granting Tickets (TGTs).
To exfiltrate the Windows Registry, CozyBear saved hives into packed files, exfiltrating them using GraphicalProton. They used “reg save” to save SYSTEM, SAM, and SECURITY registry hives and used PowerShell to stage .zip archives in the C:\Windows\Temp\ directory.
CozyBear used the SharpChromium tool to obtain sensitive browser data such as session cookies, browsing history, or saved logins in a few specific cases. They also used the DSInternals open-source tool to interact with Directory Services, allowing them to obtain sensitive Domain information.
Network Reconnaissance
After CozyBear built a secure foothold and gained an awareness of a victim’s TeamCity server, they focused on network reconnaissance, performing network reconnaissance using a mix of built-in commands and additional tools, such as a port scanner and PowerSploit, which it launched into memory.
Tunneling into Compromised Environments & Lateral Movement
In selected environments, CozyBear used a modified open-source reverse socks tunneler named Rsockstun (rr.exe) to establish a tunnel to the C2 infrastructure. After dropping it to disk, they executed rr.exe in memory or using the Windows Management Instrumentation Command Line (WMIC) utility. To facilitate lateral movement, CozyBear used WMIC and modified the DisableRestrictedAdmin registry key to enable remote connections.
CozyBear’s sophisticated and multifaceted operation is marked by the strategic exploitation of CVE-2023-42793 in JetBrains TeamCity servers. Their tactics, ranging from remote code execution and abuse of Microsoft OneDrive and DropBox to advanced techniques like DLL hijacking and using the GraphicalProton backdoor, demonstrate a high level of technical expertise and adaptability. CozyBear’s operations, characterized by their stealth and persistence, highlight the evolving nature of cyber threats and the importance of robust cybersecurity measures.
Risk & Impact Assessment
CozyBear’s exploitation of CVE-2023-42793 presents multifaceted risks and impacts for organizations directly using JetBrains TeamCity, their partners, and their clients. The primary risk for organizations, whether as customers of or suppliers using TeamCity, centers around CozyBear’s potential to exploit compromised environments. For customers, the risk lies in CozyBear leveraging a compromised supplier as a vector to infiltrate their systems. Conversely, suppliers using TeamCity risk inadvertently compromising their clients’ environments. This dual perspective of risk amplifies the material impact, as it undermines the security posture of the affected organizations and places their clients in jeopardy. Such a scenario can lead to strained relationships, significant financial losses, and reputational damage for suppliers and their clients.
On the other hand, organizations using a vulnerable TeamCity server for internal software development face the direct risk of unauthorized access by CozyBear, potentially leading to lateral movement and persistent threats within their network. In both scenarios, the material impacts encompass reputational damage, erosion of customer trust, and possible legal and regulatory consequences. In all scenarios, the impact is material, with a substantial likelihood that the incident is of significant importance to customers, stakeholders, partners, or suppliers, necessitating a robust response plan and proactive measures to mitigate these risks.
Source Material: CISA, Russian Foreign Intelligence Service (SVR) Exploiting JetBrains TeamCity CVE Globally
Regifted: Qakbot Resurfaces in New Phishing Campaign
Qakbot – Windows Installer (.msi) – Social Engineering – Phishing – Accommodation and Food Services
Threat Analysis
In December 2023, Microsoft identified a Qakbot phishing campaign. This new wave, commencing on December 11, was characterized by its low volume but targeted approach, specifically focusing on the hospitality industry.
Qakbot, also known as Qbot and Pinkslipbot, was one of the largest and longest-running botnets until its dismantlement by a multinational law enforcement operation named Operation ‘Duck Hunt’ in August 2023. Spearheaded by the FBI, this operation successfully took down the botnet after it had infected over 700,000 computers, causing hundreds of millions of dollars in damage.
Throughout the years, Qakbot has consistently served as an initial infection vector for various ransomware gangs and their affiliates or operators, including Conti, ProLock, Egregor, REvil, RansomExx, MegaCortex, and Black Basta. Qakbot has been linked to at least 40 ransomware attacks against various sectors, including finance and insurance, health care and social assistance, and government agencies worldwide.
The latest Qakbot phishing campaign employed a deceptive method where the targets received an email with a PDF attachment named “GuesListVegas.pdf.” The threat actors crafted the email to appear legitimate, coming from a user masquerading as an IRS employee in the IRS Memphis Tennessee office.
When opened, the phishing email’s PDF attachment notified the recipient that “Document preview is not available,” prompting them to click a button to download it from “Adobe Cloud.” Clicking the button led to downloading a Windows Installer (.msi) file digitally signed by ‘Software Agility Limited.’
Executing the MSI file, which includes an embedded DLL executed through the export “hvsi” function, leads to the invocation of Qakbot. This technique demonstrates a nuanced approach to running the payload, leveraging less common methods to evade detection.
Microsoft says the DLL has an embedded configuration EPOCH timestamp indicating that it was generated on 11 December, the same day the phishing campaign started, and uses a campaign code of ‘tchk06’ and command and control servers at 45.138.74.191:443 and 65.108.218.24:443.
A significant aspect of this campaign is the deployment of a previously unseen version of Qakbot, identified as version 0x500. According to Pim Trouerbach, a detection engineer with Proofpoint, there are minor changes to the new QakBot DLL, including using AES rather than XOR to decrypt strings, as seen in previous versions. Furthermore, this new version contains some bugs.
Risk & Impact Assessment
The recent Qakbot phishing campaign poses significant immediate risks, particularly to organizations in the hospitality industry, due to its targeted and sophisticated nature. The use of socially engineered emails masquerading as legitimate IRS communications, coupled with deploying a new, albeit developing, version of Qakbot, increases the risk of successful infiltration and data compromise. The potential impacts include unauthorized access to sensitive data and, considering the historical use of Qakbot as a precursor to more destructive ransomware attacks, there is a heightened risk of subsequent, more severe cyber incidents.
If a Qakbot infection results in follow-on malicious activity, such as ransomware and data exfiltration. It will likely cause a material impact extending beyond the immediate target and be considered important to stakeholders, including customers, partners, and suppliers. The nature of services in the hospitality sector means that a breach could have cascading effects, resulting in the exfiltration of employee and customer data and potentially disrupting operations. This scenario underscores the need for robust cybersecurity measures and incident response plans for direct targets and associated entities that threat actors might indirectly impact. The likely evolution of Qakbot suggests that the threat is not static, and organizations must remain vigilant and adaptive in their cybersecurity strategies to mitigate these risks effectively.
Source Material: Microsoft Threat Intelligence, X Post
Don’t Unwrap this Present: Phishing Campaign Employs Publicly Available Tool to Bypass Detection
Phishing – Predator Tool – Credential Theft – Evasion Tactics – Industries/All
Threat Analysis
There has been a rise in cybercriminals using publicly available tools to carry out their malicious operations. One such tool recently observed being utilized by cybercriminals in phishing campaigns is Predator, which is hosted on GitHub.
Predator is a tool that was created to combat bots and web crawlers. Its primary function is to differentiate between web requests made by automated systems, such as bots or web crawlers, and those made by human users. This feature is important in various web management contexts, where distinguishing between human and automated traffic affects website functionality, security, and user experience.
However, Predator’s ability to differentiate between automated and human web traffic has been misused to facilitate phishing operations. It has enabled these campaigns to selectively present malicious content to real users while avoiding detection by automated security systems.
The choice to use Predator also reveals the threat actors’ objective to maximize the success rate of their phishing campaigns while minimizing the risk of detection. This approach not only indicates a sophisticated level of planning and execution but also highlights the ongoing challenge for cybersecurity professionals in anticipating and countering the evolving tactics of cyber adversaries.
The attack flow in these phishing campaigns begins with a phishing email containing a malicious link. The emails analyzed by Trellix all originated from compromised email accounts, indicating a staged attack approach. However, there’s a roughly even chance that not all phishing emails originated from a compromised email account. The campaigns frequently change email templates and the brands they impersonate to create a sense of urgency or mimic legitimate notifications. This strategy is designed to trick users into interacting with the URLs provided in the emails. However, the campaigns incorporated code from Predator to check for possible bot/crawler/automation presence once a victim clicks on a malicious link. If such systems are detected, the code redirects such automated systems to legitimate pages like Wikipedia or Google Search. Otherwise, real users are shown the phishing page.
When the user clicks on the link, the first page uses the window.location.replace method to redirect to the next page. However, the page hosts further code that creates hidden/empty links to detect automation tools. These invisible links will not be visible to the user, but automated programs can see them as they check for all links in the HTML code. If any of these URLs are traversed, it signifies that it is an automated program and is redirected to a legitimate site instead of the actual phishing page. Also, the code uses “junk” text in between words to avoid string-based detection.
If the first method fails, the tool uses further techniques to detect bot/crawler/automation using various functions that perform multiple tests. If a bot is detected, it changes all <href> links within the page to the Microsoft Office Wikipedia page.
The first function checks for “mimeTypes” and the number of plugins in the browser. HTTP headers sent by bots/automation tools are often in different order compared to a browser used by humans, or many just do not send them at all. mimeTypes obtains a list of all the MIME types supported by the browser, and navigator.plugins contains a list of plugins installed. A visitor is considered a bot if the length of both is 0.
The second function, “navigator.webdriver” indicates whether the user agent is controlled by automation. If it returns true, then it is a bot. The third function checks for the same.
The last function, “if (window.callPhantom || window._phantom)” checks for usage of the PhantomJS browser. PhantomJS is a discontinued headless browser used for automating web page interaction.
Lastly, when the tool suspects that the visitor is a bot, it generates random links, which direct to a page limbo.php containing more random links, and this process keeps repeating. Again, attackers slightly changed tactics from the original tool: instead of generating random links dynamically, they hardcoded random links.
Trellix has observed various phishing campaigns employing Predator’s evasion technique code since December 2022. These campaigns showcase a range of phishing tactics, targeting different brands and using diverse deceptive methods. Some notable examples include:
- Fake Notification Emails: One campaign involved emails posing as notifications asking recipients to review a document, with a link leading to a phishing page.
- Fake Remittance Emails: Another campaign used emails with fake remittance information containing malicious links in attached PDFs.
- Fake Voice Call Notifications: Emails mimicking missed voice call notifications with links leading to fake Microsoft phishing pages were also observed.
- Mailbox Storage Notifications: Some phishing emails alerted recipients about mailbox storage issues, urging immediate action and directing them to phishing sites.
- Financial Institution Impersonation: These phishing emails impersonated American Express, asking users to revalidate their credentials. These emails used inline images with text to avoid word/sentence-based detection.
- File Share Notifications: Another campaign involved emails appearing to be from First American Title, sharing a secure document, again using inline images instead of text.
As shown in the above campaigns, threat actors can incorporate this tool’s code into numerous phishing campaigns. Trellix has observed the final phishing pages mimicking American Express, Microsoft 365, and OneDrive.
Cybercriminals always seek new ways to evade detection from organizations’ security products. Utilizing open-source tools, such as Predator, saves them time and effort, as they can readily employ them to avoid detection and achieve their malicious goals more effectively. Furthermore, these threat actors have become more sophisticated, using different URL patterns and targeting multiple brands to achieve better success rates for their phishing campaigns. Since such attacks often originate from compromised accounts, end-user education and awareness are more vital than ever.
Risk & Impact Assessment
The phishing campaigns utilizing Predator pose significant risks and impacts to organizations across various sectors. The primary risk lies in the evasion techniques, which increase the likelihood of these phishing campaigns from being detected, resulting in a successful phishing attack. These campaigns can lead to account compromise. An account compromise can lead to further malicious activity, resulting in data breaches and operational disruptions for affected organizations.
Given the nature of these attacks, a material impact on organizations is unlikely. However, an account compromise that is reasonably expected to result in data theft or disrupt operations will almost certainly have a material impact. This impact is relevant to customers, stakeholders, partners, and suppliers who may be affected by the theft of personal information, data access and integrity issues, or supply chain disruptions. This material impact warrants serious consideration and action from all organizations seeking to safeguard their assets and maintain trust among their key stakeholders.
These campaigns, evidenced by their varied tactics and targets, suggest a persistent and escalating threat. Organizations must, therefore, recognize the heightened risk posed by these phishing campaigns and implement the measures recommended in the Actions and Recommendations section to mitigate any potential impacts.
Source Material: Trellix, Cybercrooks Leveraging Anti Automation Toolkit for Phishing Campaigns
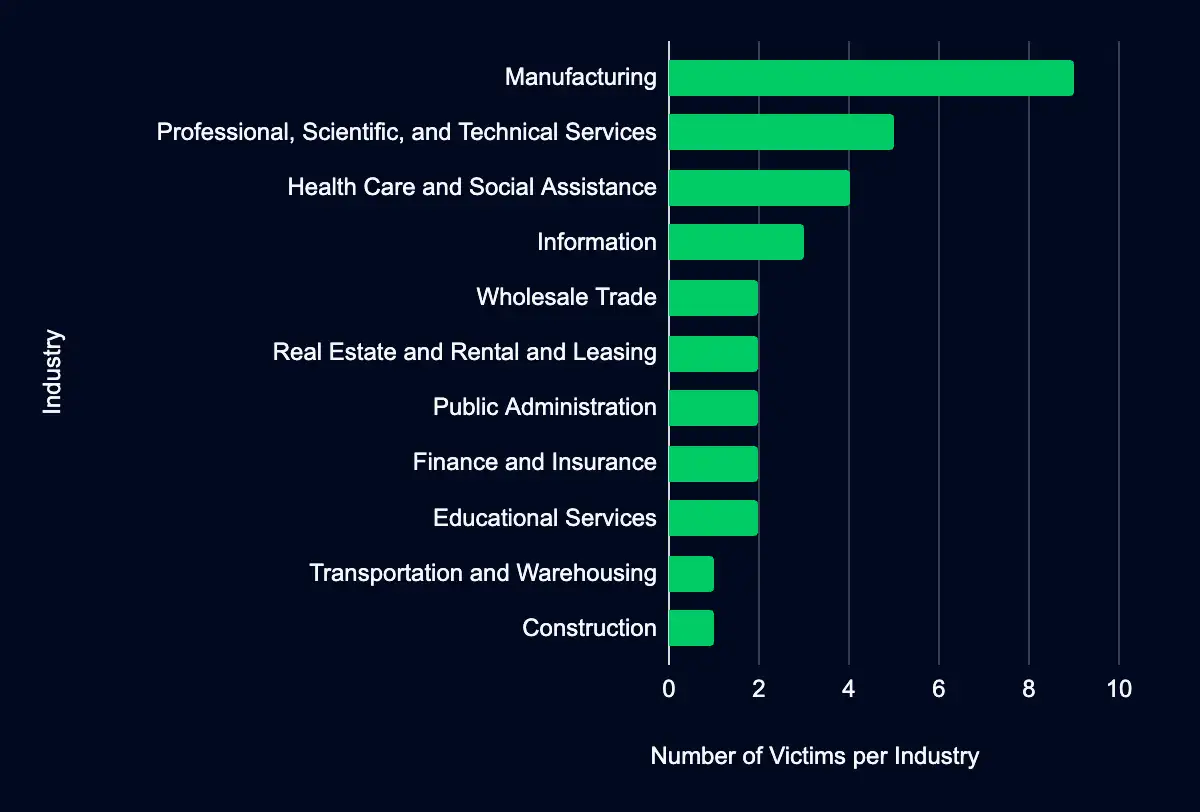
You Don’t Want to Be on This Naughty List: Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Health Care and Social Assistance – Information – Wholesale Trade
The naughty list grows. Ransomware groups listed 33 organizations on their data leak sites in the past week, with almost half from the USA. Your industry, especially Manufacturing and Professional, Scientific, and Technical Services, might be at risk. Dive into this report to uncover the statistics and organizations added and get a comprehensive insight.
Finally, a Present We Wanted: CISA Reports No New CVEs Added to its Known Exploited Vulnerabilities Catalog
In an unexpected gift, CISA added no new CVEs to the Known Exploited Vulnerabilities catalog this past week. This break in updates doesn’t mean the threat landscape is any less dangerous. It’s an opportune moment to review existing vulnerabilities and ensure your systems are protected against known threats.
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share