Russian APT Star Blizzard, Growing Insider Threats, Escalating QR Code Phishing, and the More_Eggs Backdoor
This week: APT Star Blizzard conducts a worldwide spear-phishing campaign, insider threats increased 44% from 2020 to 2022 according to research, a QR code phishing campaign appears in over 60,000 emails in Q3, APT Lazarus Group found exploiting CVE to deploy malware in Operation Blacksmith, and recruiters are being targeted in a phishing campaign deploying the More_Eggs backdoor. All this and the latest from data leak sites and new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Star Blizzard, Russian FSB Linked APT, Increases Sophistication and Evasion in Worldwide Spear-phishing Campaigns
- Insider Threats Leverage Known Vulnerabilities and Tools, Incidents Increased by 44% from 2020 to 2022
- The Escalating Threat of QR Code Phishing: Over 60,000 Emails Detected in Q3
- Lazarus Group Exploited CVE-2021-44228 in Operation Blacksmith to Deploy New Malware
- TA4557 Targets Recruiters in Phishing Campaign to Deploy the More_Eggs Backdoor
- Latest Additions to Data Leak Sites
- CISA Adds 3 New CVEs to its Known Exploited Vulnerabilities Catalog
Star Blizzard, Russian FSB Linked APT, Increases Sophistication and Evasion in Worldwide Spear-phishing Campaigns
Star Blizzard – Evilginx – Spear Phishing – Credential Theft – Public Administration – Other Services – Transportation and Warehouse – Educational Services – Information
Threat Analysis
The Russia-based actor Star Blizzard (Callisto Group, TA446, COLDRIVER, TAG-53, and BlueCharlie) continues successful spear-phishing attacks against targeted organizations and individuals involved in international affairs, defense, and logistics support to Ukraine, as well as academia, information security companies, and other entities aligning with Russian state interests in the US and other geographical areas. According to multiple government agencies, Star Blizzard is almost certainly a subordinate Russian Federal Security Service (FSB) Centre 18 unit.
Based on Microsoft’s analysis of the actor’s TTPs observed in 2022, Star Blizzard has evolved to improve its detection evasion capabilities. Microsoft has identified five new Star Blizzard evasion techniques:
- Using server-side scripts to prevent automated fingerprinting and scanning of actor-controlled infrastructure.
- Using HubSpot and MailerLite services to hide the genuine email sender addresses and prevent the need for including actor-controlled domain infrastructure in email messages.
- Using a DNS provider to obscure the IP addresses of actor-controlled virtual private server (VPS) infrastructure.
- Password-protected PDF lures or links to cloud-based file-sharing platforms where PDF lures are hosted.
- Shifting to a more randomized domain generation algorithm (DGA) for actor-registered domains.
Attack Outline Overview
Star Blizzard’s spear-phishing campaigns target a specific individual or group using information known to be of interest to the targets. Star Blizzard actors use the open-source framework Evilginx in their spear-phishing campaigns, which allows them to harvest credentials and session cookies to bypass the use of two-factor authentication successfully.
Research and Preparation
Using open-source resources, including social media and professional networking platforms, Star Blizzard identifies topics of interest to engage their target. They take the time to research their interests and identify their real-world social or professional contacts. Star Blizzard then creates email accounts impersonating known contacts of their targets. They also create fake social media or networking profiles that impersonate respected experts and have used supposed conference or event invitations as lures.
Star Blizzard has predominantly sent spear-phishing emails to targets’ personal email addresses, although they have also used targets’ corporate or business email addresses. The actors may intentionally use personal emails to circumvent security controls in place on corporate networks. Star Blizzard actors also create malicious domains resembling legitimate organizations.
Building a Rapport & Email Delivery
Having taken the time to research their targets’ to create a believable approach, Star Blizzard will start to build trust. They often establish benign contact on a topic they hope will engage their targets. There is often some correspondence between the actor and the target, sometimes over an extended period, as they build rapport. However, whether this rapport-building contact is conducted via email or other means is unknown.
Once they establish trust, the actor will send an initial email asking to review a document, but without any attachment or link to the document. The threat actor will wait for a response, then send an additional email with either an attached PDF file or a link to a PDF file.
To send their emails, Microsoft has observed Star Blizzard using two different services, HubSpot and MailerLite, which provide them with a dedicated subdomain on the service that is then used to create URLs. These URLs act as the entry point to a redirection chain ending at actor-controlled EvilGinx server infrastructure. The services can also provide the user with a dedicated email address per configured email campaign, which the threat actor uses as the “From” address in their campaigns.
Most Star Blizzard HubSpot email campaigns have targeted multiple academic institutions, think tanks, and other research organizations using a common theme to obtain their credentials. Microsoft assesses that this use-case of the HubSpot mailing platform was to allow the threat actor to track large numbers of identical messages sent to multiple recipients. It should be noted that the HubSpot platform requires the “Reply-to” address in these emails to be an actual in-use account.
Other HubSpot campaigns have used the campaign URL embedded in an attached PDF lure or directly in the email body to perform redirection to actor-controlled Evilginx server infrastructure configured for email account credential theft. Microsoft assesses that in these cases, the actors used the HubSpot platform to remove the need to include actor-controlled domain infrastructure in the spear-phishing emails and better evade detection based on indicators of compromise (IOC).
Star Blizzard’s use of the MailerLite platform is similar to the second HubSpot tactic, with the observed campaign URL redirecting to actor-controlled infrastructure purposed for email credential theft. The PDF file will be unreadable, with a prominent button purporting to enable reading the content. Pressing the button in the PDF lure causes the default browser to open a link embedded in the PDF file code, beginning the redirection chain. Targets will likely see a web page titled “Docs” in the initial page opened and may be presented with a CAPTCHA to solve before continuing the redirection.
The host domain in the web address is actor-controlled and not the email server’s or cloud service’s expected domain. Following the public reporting by Recorded Future (August 2023) on detection opportunities for Star Blizzard domain registrations, Microsoft has observed Star Blizzard making significant changes in their chosen domain naming syntax. Before the public reporting, Star Blizzard utilized a limited wordlist for their DGA. Subsequently, Microsoft has observed that the threat actor has upgraded their domain-generating mechanism to include a more randomized list of words. Domains are usually registered in groups, many times with similar naming conventions.
In December 2022, Microsoft began to observe Star Blizzard using a domain name service (DNS) provider that acts as a reverse proxy server to resolve actor-registered domain infrastructure. As of May 2023, most Star Blizzard registered domains associated with their redirector servers use a DNS provider to obscure the resolving IP addresses allocated to their dedicated VPS infrastructure. Microsoft has yet to observe Star Blizzard utilizing a DNS provider to resolve domains used on Evilginx servers.
Previously, Star Blizzard evaded automated browsing and detonation by fingerprinting browsing behavior using hCaptcha servers to filter targets and prevent automatic scanning of their Evilginx server infrastructure. However, beginning in April 2023, they have gradually moved away from using hCaptcha servers as the sole initial filter to using JavaScript code before redirecting the browsing session to the Evilginx server.
In May 2023, Star Blizzard actors were observed refining the JavaScript code, resulting in an updated version (“Docs”), which they still use today. This capability collects various information from the browser performing the browsing session to the redirector server. This information includes checks if the browser has any plugins installed and if the page is being accessed by an automation tool.
The redirector server assesses the data collected from the browser and decides whether to allow continued redirection. A bad verdict results in an HTTP error response and no further redirection. A good verdict will redirect to a sign-in screen with the targeted email populated in the username field.
If multifactor authentication is configured for a targeted email account, entering a password in the displayed sign-in screen will trigger an authentication approval request. If passwordless access is configured, an authentication approval request is immediately received on the device chosen for obtaining authentication approvals.
Star Blizzard cannot obtain the credentials if the target has not inputted a valid password and/or approved the authentication request. However, if the target completes the authentication process, they will have obtained the credentials. Once they have obtained access, they will access and steal emails and attachments from the victim’s inbox. They will also set up mail-forwarding rules, giving them ongoing visibility of victim correspondence. They have also accessed mailing list data and contacts list, which they use for follow-on targeting and further phishing activity.
Star Blizzard continues to use TTPs first observed in 2022, such as the Evilginx framework, spear-phishing, and custom-built PDF lures. Star Blizzard consistently uses pairs of dedicated Virtual Private Servers (VPSs) to host actor-controlled infrastructure (redirector and Evilginx servers), where each server usually hosts a separate actor-registered domain.
Risk & Impact Assessment
Star Blizzard’s spear-phishing campaigns pose considerable risks to targeted organizations, primarily in international affairs, defense, academia, and sectors aligning with Russian state interests. The primary risk lies in the unauthorized access and exfiltration of targeted email data, which may include confidential communications, intellectual property theft, and network integrity.
The material impact of such incidents extends beyond the immediate victims to likely affect customers, stakeholders, partners, or suppliers through the cascading effects of trust erosion, reputational damage, and potential secondary phishing attacks. The implications for entities involved in critical infrastructure or national security are even more severe, potentially impacting national security and diplomatic relations. The sophisticated nature of Star Blizzard’s tactics, particularly their ability to bypass two-factor authentication and leverage social engineering, amplifies these risks, making traditional defense mechanisms less effective and increasing the challenge of promptly detecting and mitigating these threats.
Source Material: CISA, Russian FSB Cyber Actor Star Blizzard Continues Worldwide Spear-phishing Campaigns; and Microsoft, Star Blizzard increases sophistication and evasion in ongoing attacks
Insider Threats Leverage Known Vulnerabilities and Tools, Incidents Increased by 44% from 2020 to 2022
Insider Threat – Microsoft Windows CVE-2017-0213 & CVE-2016-3309- Apache HTTP Server CVE-2021-42013 – Privilege Escalation – Vulnerability Exploitation – Industries/All
Threat Analysis
Insider threats are growing more frequent and expensive: According to the Ponemon Institute, insider threat incidents increased by 44% from 2020 to 2022. The average cost per malicious incident climbed to $648,000, and non-malicious incidents rose to $485,000.
Insider threats are individuals with the potential to negatively affect the confidentiality, integrity, or availability of an organization’s information or IT systems, either wittingly or unwittingly. These threats can come from current or former employees, contractors, or partners who misuse access to an organization’s resources. An example of a witting insider threat could be a user stealing intellectual property. An unwitting insider threat could be a user accidentally publishing secret keys or passwords to a public code repository.
Between January 2021 and April 2023, CrowdStrike identified multiple incidents where internal users exploited or sought to exploit known vulnerabilities or deployed offensive security tooling against their enterprise environment. Approximately 55% of these insider threat incidents involved unauthorized or attempted use of privilege escalation exploits. In comparison, about 45% involved insiders unknowingly introducing risk through the unauthorized download of exploits or offensive security tools.
CrowdStrike’s analysis revealed that malicious insiders commonly exploited six vulnerabilities for which there is publicly available proof-of-concept (POC) code. Three of these privilege escalation vulnerabilities impact Windows systems, and the other three affect Linux. Malicious insiders leveraged these vulnerabilities in two broad categories: unauthorized exploitation to escalate privileges and support follow-on objectives and unauthorized testing of exploits or downloading offensive tools for defensive or training purposes.
For instance, in late July 2022, a terminated employee at a U.S.-based media entity unsuccessfully attempted to leverage CVE-2017-0213 to conduct unauthorized activities. In another incident in early April 2023, an internal user of a Western Europe-based retail entity attempted to exploit CVE-2017-0213, leveraging the WhatsApp messenger application to download an exploit to escalate privileges and install the uTorrent file-sharing application and unauthorized games.
Insiders who unknowingly introduce risks to their environment often involve the unauthorized download of exploits or other offensive security tools for testing or training purposes. In these scenarios, insiders, who may be responsible for using exploits and offensive tools as part of their regular duties, inadvertently introduced risks by not adhering to safe-handling procedures. For instance, exploits were downloaded on unauthorized systems, potentially disrupting operations or inadvertently aiding external adversaries.
The mishandling of exploits and offensive tools could cause damage in several ways. Users testing exploits on unauthorized systems who do not have a thorough understanding of the exploit’s impacts could disrupt operations, as some exploits could cause unintended negative actions, like system crashes. Additionally, an adversary with a foothold on the network could leverage these exploits or tools to support their own malicious activity. Finally, downloading unvetted code can introduce backdoors or other malicious artifacts into the internal user’s network.
As an example, in October 2022, an internal user of a U.S.-based technology entity leveraged, without permission, a CVE-2021-42013 exploit code to launch an Apache reverse shell as part of a Capture-the-Flag (CTF) competition. In another incident in February 2023, an internal user at a United States-based technology entity attempted to download an exploit for CVE-2016-3309 on their corporate computer instead of on the approved system for this type of activity.
Crowdstrike has observed multiple incidents involving insider users’ unauthorized deployment of various security tools, like the Metasploit Framework, on Windows and Linux hosts for defense-focused testing. For instance, in December 2022, an internal user downloaded and staged ElevateKit, a privilege escalation framework commonly leveraged alongside Cobalt Strike. In addition to ElevateKit, the user staged Mimikatz and PowerLurk. While this incident was determined to be related to unauthorized security testing preparation, a threat actor could potentially abuse these previously deployed tools to escalate privileges, move laterally, or establish persistence.
In addition to exploiting known vulnerabilities, insider threats employ various non-exploit-based methods to achieve their objectives. These methods include DLL hijacking, abusing insecure file system permissions, and manipulating insecure service configurations. Such activities enable insiders to escalate privileges, evade defenses, or execute arbitrary code without necessarily relying on known software vulnerabilities.
The analysis of insider threat incidents from January 2021 to April 2023 by CrowdStrike reveals a multifaceted insider threat landscape within organizations. Insider threats, both witting and unwitting, leverage known vulnerabilities, offensive security tools, and non-exploit-based techniques to compromise organizational security. Internal users have an advantage when exploiting older local privilege escalation vulnerabilities. This advantage is because they often possess low-level privileges and/or credentials to run these exploits successfully. Additionally, they better understand the host environment and can perform basic reconnaissance commands with less risk of being caught than an external remote threat actor.
These incidents underscore the need for a layered and nuanced approach to cybersecurity that addresses technical vulnerabilities and the human element within the security perimeter. By understanding the motivations, methods, and potential impacts of insider actions, organizations can better prepare and respond to these internal security challenges, thereby safeguarding their assets, reputation, and trust.
Risk & Impact Assessment
Assessing risks and impacts stemming from insider threats exploiting known vulnerabilities and downloading offensive security tools reveals a multifaceted threat landscape with significant implications for organizations. The primary risk involves the potential compromise of sensitive data and critical systems, which can lead to substantial financial losses, estimated at an average of $648,000 per malicious incident. More than just financial repercussions, these incidents erode customer trust and stakeholder confidence, potentially leading to long-term reputational damage.
The material impact of such incidents extends beyond the organization itself, affecting customers, stakeholders, partners, and suppliers, especially when considering the interconnected nature of modern business ecosystems. For instance, the unauthorized access or misuse of data can lead to breaches of customer privacy, disruption of supply chains, and legal liabilities, particularly in sectors where data sensitivity is paramount.
Furthermore, exploiting older vulnerabilities highlights insufficient internal security practices, such as delayed patch management, which poses an ongoing risk. This situation underscores the need for organizations to bolster their cybersecurity defenses and foster a culture of security awareness and adherence to protocols, thereby mitigating the danger of both deliberate and unintentional insider threats.
Source Material: Crowdstrike, How Malicious Insiders Use Known Vulnerabilities Against Their Organizations
The Escalating Threat of QR Code Phishing: Over 60,000 Emails Detected in Q3
QR Code Phishing (Quishing) – Social Engineering – Credential Theft – Industries/All
Threat Analysis
Quick Response (QR) code-based phishing, or “quishing,” is an attack where threat actors use QR codes to deceive victims. These malicious QR codes are often placed in seemingly legitimate locations, such as emails, websites, flyers, or posters. When unsuspecting individuals scan these codes with their smartphones, they are unknowingly directed to malicious websites, leading to credential compromise or malware downloads. This method capitalizes on users’ general trust and familiarity with QR codes, especially since their usage has become more prevalent in everyday activities.
Recently, there has been a noticeable increase in QR code phishing attacks. Trellix’s research indicates a significant surge in quishing campaigns, with over 60,000 email samples detected in the last quarter. Geographically, these attacks have been widespread, but countries like the United States, Germany, Canada, Sweden, and Australia have been identified as primary targets in recent campaigns. These campaigns are characterized by diverse tactics, including postal phishing, spear phishing, and malware delivery, all facilitated through QR code links.
Trellix identified several prominent quishing campaigns, including impersonating postal services, spear phishing emails impersonating human resources, payroll and IT service teams, and file-sharing and crypto-wallet platforms.
Two prominent postal service impersonation quishing campaigns impersonate FedEx and DHL. In the FedEx campaign, users receive an email prompting them to scan a QR code to update delivery information, pay levied customs, or approve delivery (Figure 3 from the Trellix source material, Scanning Danger: Unmasking the Threats of Quishing). Once the user scans the QR code, they are directed to a FedEx login phishing page (Figure 4), prompting them to enter their email credentials, which are exfiltrated to a .PHP page once the user attempts to log in.
Phishing emails impersonating DHL contain waybill numbers, shipment numbers, and subjects such as ‘Waybill:,’ ‘Delivery Attempted,’ and ‘Package put on hold’ to deceive victims (Figure 5). Emails contain QR codes, which, when scanned, redirect the users to a fake DHL page, requesting them to enter their email credentials along with updating delivery and payment information (Figure 6). This data is then exfiltrated to threat actors.
Three types of spear-quishing campaigns were observed: Human resource (HR), payroll, and IT service impersonation. In HR impersonation, cybercriminals pose as HR personnel to trick employees into disclosing sensitive information or performing harmful actions. These emails (Figure 7) often mimic HR communications, such as requests for compliance information, policy updates, or even employee financial information, such as payslips and tax statements.
This campaign leveraged ‘workers.dev’ and ‘glitch.me’ domain URLs, which instantly deploy serverless code to evade detection. These call-to-action URLs redirect through Cloudflare captcha filtering and serve a Microsoft login phishing page.
The payroll impersonation campaign targets individuals and organizations. Cybercriminals impersonate payroll services to steal sensitive financial information, such as Social Security Numbers, bank account details, or login credentials. These emails (Figure 8) mimic salary updates, fiscal year results, and bonus promises, compelling recipients to act.
These emails may include logos, branding, and language commonly used by their payroll department, further deceiving recipients. The spoofed emails closely mimic official communications with a QR prominently placed within the email. Once scanned, the QR code directs the user to a Microsoft credentials harvesting page.
IT service quishing emails target employees by impersonating help/resolution desks, prompting users to log in to their account. The email (Figure 9) is disguised as a support or system administrator message, conveying a sense of urgency by utilizing keywords such as ‘Action Required,’ ‘Notice:,’ and ‘QR code expires in 24 hours’ in the body. The QR code, when scanned, redirects the user to a fake Outlook login phishing page (Figure 10) to harvest credentials.
In addition to utilizing malicious QR codes, this campaign utilized trusted domains like bing[.]com, krxd[.]com and cf-ipfs[.]com to redirect users to phishing sites. For instance, the Bing redirect URLs include a Base-64 encoded phishing URL (Cofense), allowing threat actors to mask phishing domains and bypass security solutions. Along with Bing redirection, these campaigns also utilized typo-squatted domains, anti-bot checks, and captcha filtering to evade detection.
Threat actors impersonated SharePoint, DocuSign, and OneDrive in the file-sharing quishing campaign. The emails (Figure 11) impersonate a SharePoint email, masquerading as a notification such as compensation emendations, insurance revisions, bonus allocations, and dividends, enticing recipients to scan a QR code to access the document. When scanned, the QR code redirects users to a fake Microsoft login page, prompting them to enter their credentials. These spoofed pages are hosted on .ru domains. The DocuSign-themed quishing emails use a structured template of legitimate DocuSign emails (Figure 12), prompting users to review their completed documents. Scanning the QR code will direct users to a Microsoft login phishing page, harvesting their credentials once they try to log in.
In the OneDrive campaign, the emails claim that their HR/payroll support team sent a OneDrive file share request with the subject ‘Payroll Tax Deduction For Week ending’ (Figure 13). The emails use an image-based email body to evade content-based detection filters, identical to a standard OneDrive file invitation. The QR code within the email redirects the user to a spoofed Microsoft login page. Once the user attempts to log in, the credentials are harvested. This campaign also employs Bing redirection, typo-squatting, anti-bot checks, and captcha-based evasion checks to bypass detection by security solutions.
Crypto wallet quishing involved emails impersonating Coinbase (Figure 14) and Binance (Figure 15) support. These emails lure victims to update their wallets by scanning the QR code and completing the process. Once the QR code is scanned, victims are taken to a fake landing page masquerading as a Coinbase or Binance page (Figure 16), prompting the user to click a button directing them to another site to enter their crypto recovery phrase, private wallet key, or Phrase Keystore JSON file.
As QR codes become more integrated into our daily lives for various purposes, it’s crucial to recognize the growing threat of QR code phishing attacks. These attacks leverage the unsuspecting nature of QR codes to deceive individuals and gain unauthorized access to personal and financial information. Users scan QR codes with mobile devices that likely do not have the same level of security and protection as desktop computers, making users who use their mobile phones to access corporate assets particularly vulnerable to QR code phishing.
Risk & Impact Assessment
The rise of QR code-based phishing attacks presents a multifaceted risk to organizations, encompassing direct and indirect impacts. These attacks pose a significant risk to data security, with the potential for credential compromise and unauthorized access to sensitive information. The impact of these attacks can lead to financial losses, intellectual property theft, and a breach of customer trust and extends far beyond the immediate organization, affecting customers, stakeholders, partners, and suppliers.
For customers, there is the risk of personal data exposure; for stakeholders and partners, the concerns lie in the integrity of shared data and the reliability of security practices; and for suppliers, the impact is seen in the potential disruption of supply chains and business operations. This interconnectedness underscores the importance of robust cybersecurity strategies not just for individual organizations but also across their entire network of relationships, highlighting the need for a collective and proactive approach to mitigating these evolving cyber threats.
Source Material: Trellix, Scanning Danger: Unmasking the Threats of Quishing
Lazarus Group Exploited CVE-2021-44228 in Operation Blacksmith to Deploy New Malware
Lazarus Group – Apache Log4j2 CVE-2021-44228 – NineRAT – Remote Access Trojan – HazyLoad – Reverse Proxy Tool – Vulnerability Exploitation – Manufacturing – Agriculture – Other Services
Threat Analysis
Cisco Talos uncovered a cyber campaign attributed to the North Korean umbrella organization Lazarus Group, dubbed Operation Blacksmith, conducted as early as March 2023. This operation leveraged the critical vulnerability CVE-2021-44228 (Log4Shell), and Cisco Talos discovered three novel DLang-based malware families. Two of these are remote access trojans (RATs), where one of them uses Telegram bots and channels for command and control (C2) communications. This Telegram-based RAT is tracked as “NineRAT” and the non-Telegram-based RAT as “DLRAT.” The other DLang-based malware is a downloader tracked as “BottomLoader.”
The Lazarus Group is recognized for its sophisticated cyber operations. Lazarus Group comprises various sub-groups, each with distinct objectives aligned with North Korea’s defense, political, national security, research, and evasion of international sanctions aiming to steal sensitive data, disrupt operations, and financial gain. Each sub-group conducts its own campaigns and develops and deploys bespoke malware against its targets, not always working in full coordination.
The tactics, techniques, and procedures (TTPs) used in this operation bear similarities and overlap with the methods and tools used by the Lazarus sub-group, Andariel. Andariel is typically responsible for gaining initial access, reconnaissance, and establishing long-term access for espionage purposes. In some cases, Andariel has also targeted healthcare organizations with ransomware attacks.
NineRAT uses Telegram bots and channels to receive commands and communicate data, interacting with Telegram through DLang-based libraries and employing methods like getMe for authentication and sendDocument/getFile for file transfers. The malware contains two embedded components; it writes these to the disk and then self-deletes. The first component, an instrumentor named nsIookup.exe, executes the second component, which handles the core RAT operations, including communication with the C2 server.
NineRat utilizes a BAT script for persistence, ensuring its continuous operation within the infected system. The malware employs modular infection chains for functional separation, enhancing its stealth and adaptability. Capable of sending and receiving files, executing various commands, and self-uninstallation, NineRAT includes commands for system reconnaissance activities like whoami and WMIC. NineRAT was first observed in March 2023 against a South American agricultural organization and later in September 2023 against a European manufacturing entity.
In addition to NineRAT, Blacksmith operators deployed HazyLoad and may have deployed DLRAT and BottomLoader. HazyLoad is a proxy tool for establishing direct access to infected systems. It is deployed to avoid repeated exploitation of initial access vulnerabilities. HazyLoad was found targeting entities in Europe and an American subsidiary of a South Korean firm. HazyLoad was previously only seen by Microsoft in October 2023, where they attributed the activity to Andariel (Onyx Sleet).
DLRAT functions as a downloader and a remote access trojan. It can gather system information posting as multipart/form data, deploy additional malware, and execute commands from its C2. It contains hardcoded commands to download, upload, delete, and rename files and sleep for a specified time. BottomLoader is a DLang-based downloader designed to download and execute next-stage payloads via PowerShell commands. It can establish persistence for newer versions or new follow-on payloads by creating a “.URL” file in the Startup directory to run the PowerShell command to download the payload.
The operation consisted of two phases; in Phase 1, Blacksmith operators exploited CVE-2021-44228 (Log4Shell) for initial access to publicly facing VMWare Horizon servers. Preliminary reconnaissance follows the initial access. Once Blacksmith operators completed the initial reconnaissance, they executed several commands to deploy HazyLoad to maintain access to the infected system without having to exploit CVE-2021-44228 repeatedly. Occasionally, Blacksmith operators ran commands that switched HazyLoad to a new remote IP address.
Blacksmith operators also executed commands that created a local user account on the system, granting it administrative privileges. The account name (krtbgt) matched the name created by Andariel and documented by Microsoft. Once Blacksmith operators created the user account, they used it for their hands-on keyboard activity, deviating from previous behavior. The hands-on keyboard activity begins by executing commands to download and use credential dumping utilities such as ProcDump and MimiKatz.
Once the credential dumping was complete, Lazarus operators deployed NineRAT on the infected systems, signifying Phase 2. Once NineRAT is executed, Lazarus operators begin executing several commands to fingerprint the infected systems again.
The operators behind Operation Blacksmith and Andariel have used a similar arsenal, including RATs and proxy tools. Both groups have exhibited tactics involving initial access through the exploitation of vulnerabilities, followed by the deployment of custom malware for persistence and control. This operation’s objectives of gaining initial access, reconnaissance, and maintaining access align with Andariel’s objectives.
Risk & Impact Assessment
The deployment of sophisticated malware tools in Operation Blacksmith by the Lazarus Group presents immediate and material risks to targeted organizations, extending beyond primary cybersecurity concerns to broader implications for stakeholders, partners, and suppliers. The exploitation of CVE-2021-44228 (Log4Shell) for initial access and the subsequent use of advanced malware like NineRAT and HazyLoad indicate a high risk of data breach, intellectual property theft, and potential operational disruptions. These risks are compounded by the Lazarus Group’s strategic focus on maintaining long-term access and heightening the threat of sustained surveillance and data exfiltration.
The material impact of such a campaign is significant, as it not only jeopardizes the security and integrity of an organization’s IT infrastructure but also poses a substantial likelihood of reputational damage, loss of customer trust, and potential legal and regulatory repercussions. This scenario is particularly critical for organizations in sectors like agriculture and manufacturing, as seen in this campaign, where the compromise of sensitive data can have far-reaching consequences on supply chains, market competitiveness, and financial stability. The overlap with tactics attributed to Andariel further complicates the threat landscape, suggesting a need for heightened vigilance and robust cybersecurity measures across a wide range of industries that might be indirectly affected through their connections to the primary targets.
Source Material: Cisco Talos, Operation Blacksmith: Lazarus targets organizations worldwide using novel Telegram-based malware written in DLang
TA4557 Targets Recruiters in Phishing Campaign to Deploy the More_Eggs Backdoor
TA4557 – More_Eggs – Phishing – Fake Candidate Websites – Industries/All
Threat Analysis
Since at least October 2023, TA4557 has been engaging in a new technique of targeting recruiters with direct emails, marking a shift from their previous approach of applying to open job listings with malicious content. In their recent campaigns, TA4557 has employed a dual technique: directly emailing recruiters and applying to job postings on public job boards.
When contacting recruiters directly, they often respond to replies with a URL linking to an actor-controlled website posing as a candidate’s resume, or they send a PDF or Word attachment containing similar instructions. These websites and attachments are designed to appear legitimate but are instrumental in the malware delivery process.
Notably, in campaigns observed in early November 2023, TA4557 directed the recipient to “refer to the domain name of my email address to access my portfolio” in the initial email instead of sending the resume website URL directly in a follow-up response.
The scriptlet downloaded by the LNK file decrypts and installs a DLL in the %APPDATA%\Microsoft folder. This DLL is designed to create a new regsrv32 process for execution using Windows Management Instrumentation (WMI) or the ActiveX Object Run method if WMI fails. The DLL has sophisticated anti-sandbox and anti-analysis features, including a loop to retrieve the RC4 key necessary for deploying the More_Eggs backdoor. This loop deliberately prolongs execution time, enhancing evasion from sandbox detection. Additionally, the DLL performs multiple checks to ascertain if it is under debugging using the NtQueryInformationProcess function.
Finally, the DLL deploys the More_Eggs backdoor along with the MSXSL executable. It uses the WMI service to initiate the MSXSL process, after which the DLL deletes itself. More_Eggs can establish persistence on the infected machine, profiling it and delivering additional payloads.
TA4557 has been a subject of interest for cybersecurity researchers since 2018, recognized as a skilled and financially motivated threat actor. Their consistent distribution of the More_Eggs backdoor marks them as a significant player in cybercrime. Historically, TA4557’s activities have shown overlaps with those attributed to the cybercrime group FIN6. However, the distinctiveness of TA4557 lies in its unique tool and malware usage, campaign targeting, and the employment of sophisticated evasive measures.
Furthermore, the malware suite utilized by TA4557 has also been observed in operations conducted by other cybercrime groups, such as the Cobalt Group and Evilnum. Despite these overlaps, Proofpoint tracks these as distinct activity clusters, which are not often observed in their threat data. This distinction underscores the unique operational footprint of TA4557, setting them apart from other groups in terms of tactics, techniques, and procedures.
Risk & Impact Assessment
The phishing campaigns orchestrated by TA4557 pose significant immediate risks to organizations, particularly those involved in recruitment and hiring processes. The primary risks include the potential for unauthorized access to sensitive corporate data, compromise of network integrity, and the installation of persistent backdoors like More_Eggs, which could lead to further exploitation. The sophistication and evasiveness of TA4557’s tactics amplify these risks, making detection and mitigation more challenging.
Beyond the immediate organizational impact, there is a substantial material impact. A successful breach by TA4557 could lead to the erosion of trust among customers, stakeholders, partners, and suppliers, potentially damaging reputations and leading to financial losses. The targeted nature of these attacks also raises concerns about the confidentiality and integrity of sensitive personnel and business information, which could have far-reaching implications for affected organizations. This threat landscape underscores the need for heightened awareness and robust security measures within the targeted organizations and across their extended networks to safeguard against such sophisticated and potentially damaging cyber threats.
Source Material: Proofpoint, Security Brief: TA4557 Targets Recruiters Directly via Email
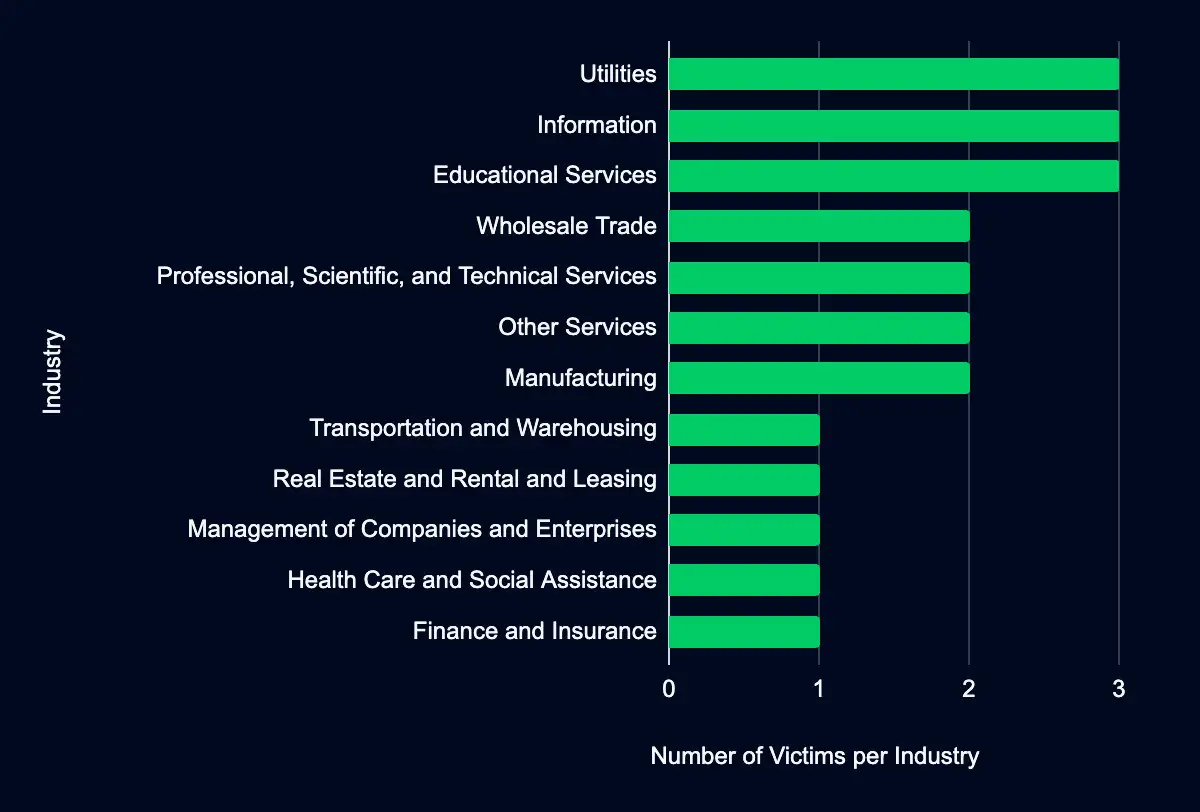
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Information – Administrative and Support and Waste Management and Remediation Services – Transportation and Warehousing
In the past week, 22 organizations were listed on monitored dark web leak sites by data extortion and ransomware threat groups. Of these, a significant majority, 18 companies, are based in the USA, highlighting a continuing focus of ransomware activities within this geographical region. The global reach of these threat groups is further underscored by one victim each from Vietnam, Sweden, Qatar, and Germany, demonstrating the indiscriminate nature of ransomware threat actors.
Our analysis strives to be comprehensive, utilizing the most current data available from our dark web monitoring platform. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed. Additionally, we may have omitted victims we could not verify.
As the data set does not include information about the industry, we do our best to classify the victims based on the NAICS industry classification system. This manual effort may introduce other discrepancies, such as misclassifying the industry. We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
CISA Adds 3 CVEs to Known Exploited Vulnerabilities Catalog
Unitronics Vision PLC CVE-2023-6448 – Qlik Sense CVE-2023-41265 and CVE-2023-41266
Within the past week, CISA added three CVEs to its Known Exploited Vulnerabilities catalog, with one CVE (CVE-2023-6448) impacting Unitronics and two (CVE-2023-41265 & CVE-2023-41266) affecting Qlik Sense products. Threat actors can exploit these vulnerabilities to execute remote commands, escalate privileges, and create an anonymous session. The link to ransomware campaigns is known for the two vulnerabilities impacting Qlik Sense and unknown for the one affecting Unitronics. It is crucial to promptly apply updates or follow vendor instructions to mitigate these vulnerabilities, with CISA recommending mitigative action between 18 December 2023 and 28 December 2023.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2023-6448 | Unitronics | Vision PLC and HMI | Unitronics Vision Series PLCs and HMIs ship with an insecure default password, which if left unchanged, can allow attackers to execute remote commands. | 2023-12-18 | Unknown |
| CVE-2023-41265 | Qlik | Sense | Qlik Sense contains an HTTP tunneling vulnerability that allows an attacker to escalate privileges and execute HTTP requests on the backend server hosting the software. | 2023-12-28 | Known |
| CVE-2023-41266 | Qlik | Sense | Qlik Sense contains a path traversal vulnerability that allows a remote, unauthenticated attacker to create an anonymous session by sending maliciously crafted HTTP requests. This anonymous session could allow the attacker to send further requests to unauthorized endpoints. | 2023-12-26 | Known |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share