New Nova Infostealer, Gh0st RAT Evolves, New Toolset Unleashed, and a Look at Microsoft Outlook Attack Vectors
This week: a new MaaS infostealer surges, Gh0st RAT spawns a new variant dubbed SugarGh0st, a new toolset includes Agent Racoon, Ntospy, and a version of Mimikatz called Mimilite, and an in depth look at Microsoft Outlook attack vectors. Plus the latest from data leak sites and six new CVEs impacting Qualcomm and Apple products.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- New MaaS Infostealer Activity Surges Since September
- Two Distinct Infection Chains Using RAR Files Deliver new Gh0st RAT Variant, SugarGh0st
- New Toolset Deployed in Various Sectors Across the US, Middle East, and Africa
- Russian APT Exploits Outlook and WinRAR Vulnerabilities in Mass Phishing Campaign
- ownCloud Vulnerability CVE-2023-49103 Actively Exploited, Leaking Admin Credentials and Server Configuration Details
- Exploring Various Attack Vectors in Microsoft Outlook
- Latest Additions to Data Leak Sites
- CISA Adds 6 New CVEs to its Known Exploited Vulnerabilities Catalog
New MaaS Infostealer Activity Surges Since September
Nova – Infostealer – Malware-as-a-Service – Sordeal – Credential Harvesting – Registry Modification – Industries/All
Threat Analysis
Nova Infostealer, emerging from the Malware-as-a-Service (MaaS) operator Sordeal, has been active in the cyber threat landscape since early 2023. Initially appearing as a relatively unnoticed tool, Nova has seen a notable increase in malicious activities, especially from September 2023, likely driven by free key giveaways to the full version. This malware is adept at performing extensive system information-gathering, executing registry modifications, and utilizing techniques to disable kernel-level logs for increased stealth.
Nova Infostealer demonstrates a range of technical capabilities; among these is its ability to gather comprehensive system information, which includes details about the system’s hardware, operating system, and installed software. Additionally, Nova is equipped to make registry modifications. Notably, Nova employs methods to disable kernel-level logs.
Like most infostealers, Nova Infostealer also harvests credentials, extracting sensitive information such as usernames, passwords, and other credentials from browsers like Chrome, Firefox, and Edge. This functionality extends to applications commonly used for communication and data storage, like Microsoft Skype, FileZilla, Nord VPN, and OpenConnect VPN. Furthermore, it can collect stored sessions and passwords from the registry. Recent developments have shown that Nova has expanded its scope to include Discord, a popular communication platform, and can inject malicious code into Discord’s modules.
This new capability allows it to intercept and exfiltrate Discord session tokens and other sensitive user information. In addition to the Discord injection, the MaaS operators are also working on adding capabilities that will enable the malware to inject malicious code into crypto wallets such as Exodus and Atomic.
The Nova Infostealer sample (win32snapshot.exe) analyzed by CYFIRMA is packed with an NSIS (Nullsoft Scriptable Install System) based crypter. Upon execution, the malware drops an archive named app-64.7z in the temp directory. The malware then extracts the archive and executes win32snapshot.exe contained within the archive. This executable downloads essential elements like AutoIT, Microsoft Visual C++ Redistributable, and Java. AutoIT, in particular, plays a significant role in Nova’s operation. Developed for automating actions in a Windows environment, AutoIT can interact with Windows APIs via the DllCall() function.
The malware then creates processes in suspended mode for code injection and attempts DLL sideloading and process injection. This approach indicates a methodical process designed to establish a foothold in the system while evading detection. Nova also uses utilities like wmic and executes various PowerShell commands to gather system information, including logical disk size, total physical memory, CPU information, UUID, and product names and keys. This comprehensive system profiling is a testament to the malware’s thoroughness in understanding its environment.
Furthermore, the malware uses cmd.exe and PowerShell to interact extensively with the registry. It queries and modifies registry keys related to the system for persistence and configuration. One notable event is the modification of a key within the “ROOT\Certificates” branch of the Windows Registry. The name of the added value is “Blob,” suggesting that binary data or a binary blob (a collection of binary data) is being stored in this registry entry. This value addition indicates installing a root certificate by the malware, which would allow a threat actor to masquerade malicious files from any entity (for example, Microsoft) as valid signed components. It could also allow an actor to decrypt SSL traffic.
Another notable modification is the “Circular Kernel Context Logger” registry key value is set to “0”. As a result, events related to kernel-mode operations, system calls, and other low-level activities will no longer be recorded. Additionally, the malware drops Update.exe (a renamed version of win32snapshot.exe) into the startup folder to achieve persistence. Combining modifying the Circular Kernel Context Logger registry key with dropping itself in the startup directory enables the malware to maintain persistence on the infected system without leaving a trace in the kernel-level logs.
The deployment process of Nova, particularly its use of an NSIS-based crypter and subsequent execution steps, demonstrates a methodical approach to establishing control over the infected system. The use of AutoIT, a legitimate scripting tool, for malicious purposes highlights a common tactic among threat actors: repurposing legitimate tools for nefarious objectives. This behavior underscores the importance of monitoring for known malware signatures and anomalous behaviors within systems.
Risk & Impact Assessment
The emergence of Nova Infostealer as a product of the Malware-as-a-Service (MaaS) Sordeal presents significant risks and impacts to organizations across various sectors. The primary risk lies in its capability to stealthily harvest sensitive information, including credentials and system data, which can lead to substantial data breaches and unauthorized access to corporate networks. This risk is exacerbated by Nova’s evolving technical sophistication, particularly its ability to evade detection and manipulate system configurations.
The material impact of such incidents is profound, potentially undermining customer trust, jeopardizing stakeholder interests, and disrupting operations. For partners and suppliers, compromising sensitive data could lead to supply chain vulnerabilities, exposing them to further cyber threats. Additionally, the ability of Nova to masquerade malicious files and decrypt SSL traffic poses a severe threat to the integrity and confidentiality of communications, further amplifying the risks to all involved parties. The cumulative effect of these risks underscores the need for robust cybersecurity measures and heightened vigilance among organizations to mitigate the potential impacts of Nova Infostealer.
Source Material: CYFIRMA, Emerging MaaS Operator Sordeal Releases Nova Infostealer
Two Distinct Infection Chains Using RAR Files Deliver new Gh0st RAT Variant, SugarGh0st
SugarGh0st – Gh0st RAT Variant – Remote Access Trojan – JavaScript Dropper – DynamicWrapperX – Public Administration – Industries/All
Threat Analysis
Cisco Talos recently discovered four lure documents deploying a new Remote Access Trojan (RAT) called SugarGh0st. Based on the language of the decoy documents, lure content, and distribution indicators, these documents likely targeted users in Uzbekistan and South Korea.
The threat actors sent one of the samples to an employee of the Ministry of Foreign Affairs of Uzbekistan, using lure content from multiple Uzbekistan sources in 2021. The threat actors wrote the three other decoy documents in Korean and likely sent them to users in South Korea based on observed command and control (C2) domain requests from IPs originating from South Korea. The initial vector of the campaign was likely a phishing email with an attached malicious RAR archive file containing a malicious Windows Shortcut file.
Overall, SugarGh0st RAT is a fully functional backdoor that offers a comprehensive suite of remote control functionalities, making it a potent tool for cyber espionage. Its capabilities include keylogging, taking screenshots, accessing webcams, and executing arbitrary commands remotely. The RAT can collect detailed information about the victim’s machine, such as the hostname, filesystem, logical drives, and operating system details. It can also manage and manipulate processes and services on the infected machine, allowing for significant control over the system. Additionally, SugarGh0st can interact with the file system, performing operations like searching, copying, moving, and deleting files. Notably, it has the ability to clear the machine’s Application, Security, and System event logs, which helps in evading detection and maintaining persistence on the infected system. These capabilities are directed by the C2 server, with the malware receiving specific hex commands to execute various actions.
Cisco Talos identified SugarGh0st as a customized variant of the well-known Gh0st RAT. A Chinese group called 红狼小组 (C.Rufus Security Team) developed Gh0st RAT, and in 2008, the source code was publicly released. There are several variants of Gh0st RAT in the threat landscape, and it remains a preferred tool for many Chinese-speaking actors.
However, SugarGh0st exhibits several new features compared to the original Gh0st malware. These include searching for specific Open Database Connectivity (ODBC) registry keys, loading library files with particular extensions and function names, custom remote administration task commands, and evading earlier detections. Additionally, the communication protocol of SugarGh0st has been modified, with the first eight bytes of the network packet header reserved as magic bytes, a change from the first five bytes used in earlier Gh0st RAT variants. Other features align with the features of earlier Gh0st RAT variants.
Cisco Talos observed two distinct infection chains deploying SugarGh0st to compromise target systems. Both chains start with a malicious RAR file, which leads to the execution of the SugarGh0st payload through different mechanisms. The first infection chain involves a Windows Shortcut file that triggers a JavaScript dropper, while the second chain leverages a DynamicWrapperX loader for shellcode execution. These chains are designed to bypass security measures and establish persistence on the infected systems, ultimately leading to the deployment of the SugarGh0st RAT.
Infection Chain No. 1 begins with a malicious RAR file containing a Windows Shortcut (LNK) file with a double extension. When this LNK file is opened, it executes a command to drop an embedded JavaScript file in the %TEMP% directory. Then, the living-off-the-land binary (LoLBin) cscript is used to execute the JavaScript. This JavaScript is heavily obfuscated and serves as a dropper, deploying multiple embedded files, including a decoy document, an encrypted SugarGh0st payload, a custom DLL loader, and a batch script to the %TEMP% directory.
First, the JavaScript opens the decoy document, then copies the legitimate rundll32 executable from the “Windows\SysWow64” folder to the %TEMP% directory, and executes the batch script. The batch script contains commands to sideload the DLL loader with rundll32.exe and executes the DllUnregisterServer function. The customized DLL loader includes packed code, when it’s run, it unpacks the code to read the dropped encrypted SugarGh0st payload, decrypts it and runs it in the memory.
Similar to the first infection chain, Infection Chain No. 2 also starts with a RAR archive containing a Windows Shortcut file with embedded commands. Upon opening the file, it drops a JavaScript file into the %TEMP% location and executes it with cscript. However, this JavaScript file is embedded with a legitimate DynamicWrapperX DLL (libeay32.dll), SugarGh0st payload, a decoy document, and shellcode. When the JavaScript is executed, it opens the decoy document and copies wscript.exe to the %TEMP% directory as dllhost.exe. It runs the dropped JavaScript again using the dllhost.exe and creates a registry subkey called “CTFMON.exe” in the Run registry key to establish persistence.
The DynamicWrapperX DLL is an ActiveX component that enables Windows API function calls in various scripts. The threat actor must first run regsvr.exe to install the component before they can run the shellcode embedded in the JavaScript file. The shellcode contains instructions to load the functions necessary for process injection from Kernel32.dll. It also loads two other DLLs, User32.dll and shlwapi.dll. Then, it loads the encrypted SugarGh0st payload, decrypts it, and reflectively loads it into the memory.
The evidence gathered in the analysis of the campaign suggests the involvement of a Chinese-speaking threat actor. This evidence includes two of the decoy files using Simplified Chinese characters in the metadata and the deployment of SugarGh0st, a variant of the Gh0st RAT, which has been a mainstay in Chinese threat actors’ arsenal. Additionally, the targeting of the Ministry of Foreign Affairs of Uzbekistan and entities in South Korea, aligns with the strategic interests and known operational patterns of Chinese threat actors. This alignment, combined with the technical evidence, provides a low confidence assessment for attributing this campaign to a Chinese-speaking adversary.
The analysis of the SugarGh0st RAT campaign reveals a sophisticated and multi-faceted operation. While it is unknown if the two infection chains were conducted by a single threat actor, it demonstrates the adaptability of threat actors when deploying malware. SugarGh0st, with its functionalities and infection mechanisms, represents a significant threat to the cybersecurity landscape. The evidence suggesting the involvement of a Chinese-speaking actor aligns with known patterns of Chinese threat actors. This campaign underscores the evolving nature of cyber threats and the importance of continuous vigilance and advanced security measures. Organizations must be proactive in enhancing their cyber defenses to counter such sophisticated threats.
Risk & Impact Assessment
The deployment of SugarGh0st RAT poses significant risks and impacts to targeted organizations. The primary risk is the potential for unauthorized access and control over sensitive systems and data, which could lead to substantial information access and theft. The RAT’s capabilities for keylogging, remote access, and data exfiltration directly threaten the confidentiality of sensitive information.
For customers, stakeholders, partners, and suppliers, the material impact is considerable. A breach could result in the loss of sensitive data, erosion of trust, legal and regulatory repercussions, and financial losses due to the theft of proprietary information and incident response. The capabilities of SugarGh0st, coupled with observed infection chains, increases the difficulty of detection and mitigation, thereby elevating the risk profile. Organizations must recognize the heightened threat level posed by tools and implement comprehensive cybersecurity measures to mitigate these risks. The potential for widespread impact across various sectors underscores the need for heightened cybersecurity awareness among all stakeholders.
Source Material: Cisco Talos, New SugarGh0st RAT targets Uzbekistan government and South Korea
New Toolset Deployed in Various Sectors Across the US, Middle East, and Africa
Agent Racoon – Ntospy – Mimilite – Credential Theft – Cyber Espionage -Educational Services – Real Estate and Rental and Leasing – Retail Trade – Other Services – Information – Public Administration
Threat Analysis
Palo Alto’s Unit 42 has identified a distinct set of tools used in a series of apparently related attacks targeting organizations across the Middle East, Africa, and the United States. These tools, comprising a new backdoor named Agent Racoon, a new tool designed to steal credentials named Ntospy, and a customized version of Mimikatz called Mimilite, were employed to infiltrate and extract sensitive information from a variety of sectors, including education, real estate, retail, non-profit organizations, telecom companies, and government entities.
Agent Racoon, as previously mentioned, establishes a backdoor within targeted systems. It is developed using the .NET framework and leverages the Domain Name Service (DNS) protocol to create a covert communication channel with its command and control (C2) server. This backdoor has various functionalities, including command execution, file uploading, and downloading. The malware’s C2 infrastructure, traced back to 2020, reveals a sophisticated use of encrypted DNS communication, ensuring stealth in the compromised systems. However, Agent Racoon has no persistence mechanism; instead, it was executed using scheduled tasks.
Ntospy plays a critical role in credential theft, operating as a custom DLL module and functioning as a Network Provider to intercept and capture user credentials during the authentication process. A Network Provider module is a DLL component that implements the interface provided by Microsoft to support additional network protocols during the authentication process. Its deployment involves registering the Ntospy DLL module as a Network Provider to hijack the authentication process and access credentials each time a victim attempts to log into the system. Notably, Ntospy exhibits unique features such as filenames mimicking Microsoft patch naming patterns and storing captured credentials in cleartext within .msu extension files. Unit 42 has observed different versions of the Ntospy malware over the time frame investigated. However, they all share similarities.
The threat actors utilized Mimilite, a customized iteration of the well-known Mimikatz tool, for credential and sensitive information harvesting. This tool, called Mimilite by the attackers, is a streamlined version of Mimikatz, requiring a specific password input via the command line for activation. Its operation involves decrypting the payload using a stream cipher, followed by an integrity check to ensure successful decryption. Mimilite is designed to dump credentials to a predefined file path while masquerading its activities under the guise of a Microsoft update. The tool’s discovery in various environments, coupled with its unique execution method, underscores its role as a critical component in the threat actors’ toolkit for extracting sensitive information.
The TTPs employed by the threat actors in these attacks reveal a consistent and systematic approach. Common techniques include file masquerading and using temporary directories for staging and deploying attack components. The threat actors also demonstrated proficiency in data exfiltration methods, notably using PowerShell snap-ins to extract emails from MS Exchange environments and cleverly manipulating file paths to disguise exfiltrated data. These TTPs, observed across the different tools used in the attacks, highlight a comprehensive and well-coordinated strategy to maximize the efficacy of the infiltration and data extraction processes.
The operational patterns observed in these attacks provide insights into the modus operandi of the threat actors. They consistently used specific directories, such as C:\Windows\Temp and C:\Temp, to stage their tools, indicating a preference for easily accessible and often overlooked system paths. The file naming conventions, such as mimicking legitimate files and applications, further demonstrate a deliberate attempt to blend in with the native environment. Notably, post-attack cleanup activities, including using cleanmgr.exe, were observed, suggesting a conscious effort by the threat actors to erase traces of their presence and actions. These operational patterns reflect a strategic approach to minimize detection and maintain a persistent presence within the compromised systems.
The sophisticated use of a diverse set of tools, including Agent Racoon, Ntospy, and Mimilite, coupled with well-planned TTPs, indicates a clear objective to infiltrate, remain undetected, and exfiltrate sensitive information from a wide range of targets. We assess with moderate confidence that the threat actors have an espionage intention, as evidenced by targeting various sectors across different regions to steal email data. Given the complexity of the tools and the meticulous execution of the attacks, we further assess with moderate confidence that nation-state-related threat actors or highly sophisticated cybercriminal groups with substantial resources and expertise conducted these activities. The level of customization and adaptation in the tools used further reinforces this assessment.
Risk & Impact Assessment
The toolset deployment poses significant risks and impacts to organizations worldwide. These risks extend beyond the immediate threat of data exfiltration and system compromise, potentially leading to reputational damage and financial losses. The sophisticated nature of these tools, coupled with the threat actors’ ability to adapt and remain undetected, increases the likelihood of sustained persistence and data exfiltration. The material impact of such incidents is substantial, likely affecting the victims and their customers, stakeholders, partners, and suppliers.
This ripple effect can lead to a loss of trust, contractual penalties, and a compromised competitive position in the market. Furthermore, the broad range of targeted sectors underscores the widespread applicability of the threat, necessitating heightened vigilance and robust cybersecurity measures across various industries. The cumulative effect of these risks and impacts highlights the urgent need for organizations to assess their cybersecurity posture, implement advanced threat detection and response strategies, and engage in proactive threat intelligence collection and sharing to mitigate the potential consequences of such sophisticated cyber attacks.
Source Material: Palo Alto Unit 42, New Tool Set Found Used Against Organizations in the Middle East, Africa and the US
Russian APT Exploits Outlook and WinRAR Vulnerabilities in Mass Phishing Campaign
Microsoft Outlook CVE-2023-23397 – WinRAR CVE-2023-38831 – TA422 – Phishing Campaign – Vulnerability Exploitation – Public Administration – Information – Educational Services – Financial and Insurance Services – Manufacturing
Threat Analysis
Since March 2023, Proofpoint researchers have observed TA422, identified as overlapping with APT28, Forest Blizzard, Pawn Storm, Fancy Bear, and BlueDelta, conducting regular phishing campaigns. These campaigns primarily targeted government, aerospace, education, finance, manufacturing, and technology sectors in Europe and North America. The threat actor leveraged patched vulnerabilities, notably CVE-2023-23397 and CVE-2023-38831, to initiate these campaigns.
TA422’s campaign prominently exploited two vulnerabilities: CVE-2023-23397, a Microsoft Outlook elevation of privilege flaw, and CVE-2023-38831, a WinRAR remote code execution flaw. CVE-2023-23397 allowed the threat actor to exploit TNEF files to initiate NTLM negotiation, obtaining a hash of the target’s NTLM password. CVE-2023-38831 enabled the execution of arbitrary code when a user attempted to view a seemingly benign file within a ZIP archive.
The phishing campaigns exploiting CVE-2023-23397 began in late March 2023, initially with a few emails. However, they escalated when they launched a high-volume campaign targeting higher education, government, manufacturing, and aerospace technology entities in Europe and North America beginning in September and continuing through October. Proofpoint observed over 10,000 repeated attempts to exploit CVE-2023-23397, targeting the same accounts daily. It is unclear if this was an error or if it was intentional. TA422 re-targeted many higher education and manufacturing users previously targeted in March 2023. It is unclear why TA422 re-targeted these entities with the same exploit. One possibility is that these entities are priority targets, attempting broad, lower-effort campaigns to gain access.
Throughout the campaign, the messages contained an appointment attachment using the Transport Neutral Encapsulation Format (TNEF) file. The TNEF file used a fake extension to masquerade as a CSV, Excel, or Word document. It contained a UNC path directing traffic to an SMB listener likely hosted on a compromised Ubiquiti router. When vulnerable instances of Outlook processed the appointment attachment, Outlook initiated an NTLM negotiation request to the file located at the UNC path, disclosing NTLM credentials from the targets without their interaction. For all the September and October campaigns, TA422 sent malicious emails from various Portugalmail addresses with the subject line “Test Meeting” and a message body of “Test meeting, please ignore this message.”
In September, TA422 began exploiting the WinRAR vulnerability, CVE-2023-32231, in two distinct campaigns, sending phishing emails from different Portugalmail addresses. The email senders spoofed geopolitical entities and used the BRICS Summit and a European Parliament meeting as subject lures to entice targets to open the emails.
The messages contained RAR file attachments that exploited CVE-2023-32231 to drop a .cmd file, which functions similarly to a batch file, to initiate communications to a Responder listener server. The .cmd file attempted to modify proxy settings in the registry, download a lure document, and beacon to the Responder server. When the .cmd file initiated an HTTP connection with the Responder server, the server responded with a WWW-Authentication header requesting NTLM methods for authentication. In the subsequent request, the victim device included sensitive NTLM information stored in the Authorization header. As NTLM credentials are exchanged, the victim device sends information, including host and usernames, in base64 encoded Authorization headers.
The Responder server was likely a compromised Fortigate FortiOS Firewall based on HTTP response headers and SSL certificates assigned to the server. While the NTLM credential exchange occurred in the background, .cmd opened a second tab that browsed to a legitimate Europa PDF file and displayed it to convince the user that the activity was legitimate. These campaigns used minimalistic batch files, which beaconed to the webhook[.]site and PowerShell to create an RSA key and an SSH connection to a remote server. Additionally, Proofpoint researchers assess with high confidence that TA422 used a compromised Ubiquiti router as the destination of the SSH login attempt.
Between September and November, multiple TA422 campaigns used Mockbin for redirection. Mockbin is a third-party service that allows developers to stage (or mock) code for testing purposes. TA422 sent lures to targeted users in the government and defense sectors, which included a link that, if clicked, would initiate a chain of malicious activity from Mockbin. The Mockbin clusters often redirected victims to InfinityFree domains and almost always used MSN as a landing page if the user did not pass browser checks.
If the user passed the browser checks, they were directed to an InfinityFree URL that checked the user’s geolocation. If that check passed, it downloaded a ZIP file named news_week_6.zip containing an LNK file. If the user executed the LNK, it ran a legitimate calculator binary located in a nested folder of the ZIP structure. Once run by the LNK, the calculator sideloaded the WindowsCodecs.dll file, using a system API to execute the file command.cmd. The .cmd file ran a series of commands to clean up files dropped to disk, displayed a lure document, and beaconed to a stage three Mocky URL. That stage three URL initiated a loop with another Mockbin URL via another obfuscated set of commands.
In late September, TA422 sent another Mockbin campaign spoofing Microsoft to targeted users in the government sector. The campaign used a lure of Windows updates to encourage victims to click a link that, if executed, would initiate a chain of activity from Mockbin. The Mockbin URL eventually downloaded a ZIP file with a name similar to regular Windows update naming conventions, such as kb5021042.zip or update-kb-5021042.zip. All the ZIP files observed contained a signed CAB installer for Windows and a .cmd file that ran as a batch file, displaying a fake progress bar of the alleged Windows update.
In November 2023, TA422 ceased using Mockbin for InfinityFree URLs to filter and redirect targets. Like the Mockbin URLs, the InfinityFree URLs used in the delivery stages redirected targets who did not pass filter checks to the MSN homepage. If the targets passed the checks, they were directed to another InfinityFree URL that checked the user’s geolocation. If that check passed, it initiated the download of war.zip containing a .cmd file. If the user executed the .cmd file, it ran a legitimate binary. The .cmd file cleans up files dropped to disk and beacons to another InfinityFree URL. That URL initiated a loop with a Mockbin URL via an obfuscated set of commands.
The persistent and evolving nature of TA422’s phishing campaigns underscores a threat actor with clear strategic objectives and a sophisticated operational framework. TA422’s consistent targeting of sectors such as government, aerospace, education, finance, manufacturing, and technology reveals an intention likely centered around espionage and intelligence gathering. The selection of vulnerabilities, coupled with the adaptive use of social engineering tactics, indicates a focus on maximizing access to sensitive information while minimizing detection and exposure.
TA422’s ability to adjust its tactics in response to errors or lack of success demonstrates its strategic planning and execution of cyber operations. The campaign’s breadth, targeting multiple sectors across different regions, suggests that TA422 operates with a broad targeting scope, possibly at a state level, aiming to fulfill long-term intelligence objectives aligned with more general geopolitical goals. However, the broad targeting may be due to an error or an objective to mask their actual targets.
Risk & Impact Assessment
The activities of TA422, particularly their phishing campaigns exploiting CVE-2023-23397 and CVE-2023-38831, have a roughly even chance of presenting significant risks and impacts to targeted organizations across various sectors. The primary risk lies in the unauthorized access to sensitive information, which could lead to substantial data breaches and intellectual property theft. This unauthorized access jeopardizes the confidentiality of critical data of affected organizations.
The material impact of such incidents would likely extend beyond the immediate targets to their customers, stakeholders, partners, or suppliers, potentially compromising the security of interconnected systems and networks. This ripple effect can result in a loss of trust, reputational damage, and legal or regulatory repercussions, especially considering the sectors targeted by TA422. The broad scope of TA422’s campaign and its evolving tactics underscores the need for heightened vigilance and robust cybersecurity measures across these sectors to mitigate the risk of infiltration and safeguard against the far-reaching impacts of such cyber threats.
Source Material: Proofpoint, TA422’s Dedicated Exploitation Loop—the Same Week After Week
ownCloud Vulnerability CVE-2023-49103 Actively Exploited, Leaking Admin Credentials and Server Configuration Details
ownCloud CVE-2023-49103 – Information Disclosure – Vulnerability Exploitation – Industries/All
Threat Analysis
As of 1 December, Rapid7 has observed at least three CVE-2023-49103 exploit attempts against customer environments. CVE-2023-49103 is an unauthenticated information disclosure vulnerability affecting the ownCloud Graph API extension versions 0.2.x before 0.2.1 and 0.3.x before 0.3.1. CVE-2023-49103 has been remediated in versions 0.3.1 and 0.2.1 of graphapi, released on 1 September 2023.
If an organization deploys its ownCloud via Docker from February 2023 onwards, this vulnerable graphapi component will be present by default. If an organization installs ownCloud manually, the graphapi component is not present by default. ownCloud is a file-sharing platform designed for enterprise environments. ownCloud disclosed the vulnerability on 21 November 2023.
According to the vulnerability description, the graphapi app relies on a third-party GetPhpInfo.php library that provides a URL. When a threat actor accesses this URL, it reveals the configuration details, including all the environment variables of the webserver, of the PHP environment (phpinfo). In containerized deployments, these environment variables may include sensitive data such as the ownCloud admin password, mail server credentials, and license key.
While it was initially considered that Docker installations of ownCloud were not exploitable, Rapid7 has confirmed that a threat actor can exploit vulnerable Docker-based installations of ownCloud by modifying the requested URI to bypass the existing Apache web server’s rewrite rules, allowing them to reach the target URI endpoint.
An indicator of compromise for CVE-2023-49103 will be the presence of an HTTP GET request to a URI path containing /apps/graphapi/vendor/microsoft/microsoft-graph/tests/GetPhpInfo.php in the Apache server’s access logs. A successful request will receive an HTTP 200 response.
When exploiting a Docker-based installation, the threat actor must append an extra path segment to the target URI path, such as `/.css,` to bypass the Apache rewrite rules and reach the target endpoint. Due to how the .htaccess file in ownCloud specifies multiple potential file extensions that ignore the rewrite rules, the additional path segment a threat actor can use may be one of the values listed here.
Risk & Impact Assessment
The exploitation of CVE-2023-49103 poses a significant risk to organizations utilizing ownCloud, including those with Docker-based deployments. The primary risk involves unauthorized information disclosure, including administrative credentials and server configuration details. Exploiting this vulnerability could lead to further malicious activities, such as data exfiltration, ransomware attacks, or potentially deeper network penetration. The material impact of such an incident is substantial, as it directly threatens the confidentiality and accessibility of critical data, which is paramount for customers, stakeholders, partners, and suppliers.
For enterprises relying on ownCloud for secure file sharing and storage, this vulnerability undermines the trust and reliability of the platform, potentially leading to reputational damage and loss of business. Additionally, the ease of exploitation, evidenced by the observed attempts in the wild, elevates the urgency for immediate remediation. Organizations must recognize the heightened risk this vulnerability presents and act swiftly to mitigate potential impacts, ensuring the continued protection of their sensitive data and maintaining the confidence of their key stakeholders.
Source Material: Rapid7, CVE-2023-49103 – Critical Information Disclosure in ownCloud Graph API
Exploring Various Attack Vectors in Microsoft Outlook
Microsoft Outlook Phishing – Email Hyperlinks – Email Attachments – Special Object and Email Reading Exploitation – Industries/All
Threat Analysis
Outlook, a core component of the Microsoft Office suite, is widely used by organizations globally for email communication, scheduling, and more. Its integral role in daily operations makes it a prime target for cyber threats. A minor security flaw in Outlook can lead to significant organizational damage, emphasizing the need for a thorough understanding of its attack vectors. With this in mind, Check Point analyzed Outlook attack vectors, categorizing them into three areas: hyperlinks, attachments, and advanced. They assumed the position of an average user and examined the security risks they may be introduced from a security research perspective.
The Hyperlink Attack Vector in Outlook involves threat actors sending emails with malicious web hyperlinks. These links, when clicked, can lead to phishing sites or initiate browser-based exploits, including sophisticated zero-day attacks. This method is straightforward yet effective, leveraging the common practice of clicking on email links. The simplicity of a single click to launch these links in Outlook underscores the potential risk, especially considering that the security risk lies more in the browser than in Outlook itself. However, not all hyperlinks are web links; they could contain other types of hyperlinks, and those may introduce security risks.
The Attachment Attack Vector in Outlook is multifaceted, with the level of risk varying based on how the user interacts with the attachment. This vector can be broken down into several key scenarios: double-click, single-click, and special file types.
Double-clicking to Open the Attachment
When a user double-clicks an attachment, Outlook attempts to open it with the application associated with the file type. The risk here depends on the security of the application opening the file. For instance, an attachment with an ‘unsafe’ file type is blocked by Outlook, while those not marked as ‘unsafe’ or ‘safe’ prompt a confirmation dialog, requiring the user to confirm they want to open the attachment.
Single-clicking to Preview the Attachment
In this scenario, Outlook uses a registered previewer application to display the content within the email client. The security risk varies depending on the file type and the previewer app’s robustness. Some file types might not have a registered previewer, leading to no preview, while others might require additional confirmation for previewing.
Special File Types
Certain file types are considered ‘safe’ and can be opened directly with a double click. While others, due to their complexity or common usage in attacks, might have additional security measures. For example, Microsoft Office applications may open files in a restricted ‘Protected View’ mode to mitigate risks.
The Email Reading Attack Vector is insidious as it can be triggered simply by reading an email in Outlook. This vector exploits vulnerabilities that activate when Outlook processes an email without requiring additional user interaction. Historically, these vulnerabilities have been less common, but their impact can be significant due to the passive nature of the attack. The vulnerabilities often lie in how Outlook parses or processes different email formats, such as HTML or TNEF (Transport Neutral Encapsulation Format).
The Special Object Attack Vector is even more covert, as it can be triggered without the user needing to read the email. This attack is executed when Outlook processes a specially crafted object, such as a malicious ‘reminder’ object, which can be automatically activated upon receiving an email. An example was the exploitation of CVE-2023-23397, where attackers targeted Ukrainian organizations by leaking NTLM credentials through Outlook without user interaction.
In the comparative analysis of Outlook attack vectors, it’s crucial to consider the level of user interaction required, the degree of difficulty in exploiting these vectors, and the knowledge, skills, and resources needed by threat actors. The Hyperlink Attack Vector, while relatively straightforward to deploy, often requires crafting convincing phishing content and may depend on exploiting browser vulnerabilities, which can be complex given modern browser security measures. The Attachment Attack Vector demands a deeper understanding of file types, application vulnerabilities, and user behaviors, making executing more challenging. The most sophisticated, the Special Object Attack Vector, requires advanced knowledge of Outlook’s internal processing and the ability to craft unique malicious objects, indicating a high level of skill and resource investment.
Risk & Impact Assessment
Assessing the risks and impacts associated with the various Outlook attack vectors reveals a multifaceted threat landscape that poses significant challenges to organizational cybersecurity. The primary risk lies in the potential for unauthorized access to sensitive information and critical communication channels. While seemingly straightforward, hyperlink attacks can lead to substantial data breaches or facilitate further network infiltration. With their more sophisticated exploitation methods, the attachment and special object vectors heighten the risk of targeted attacks that could bypass conventional security measures.
The material impact of these threats extends beyond the immediate organization, potentially affecting customers, stakeholders, partners, or suppliers, especially considering the interconnected nature of modern business operations. A successful attack could result in a loss of trust, legal repercussions, and financial losses for the targeted organization and its associated entities. This interconnected risk underscores the need for a comprehensive, multi-layered security approach that includes robust technical defenses, continuous monitoring, proactive threat intelligence, and effective incident response plans to mitigate potential impacts on all involved parties.
Source Material: Check Point, The Obvious, the Normal and the Advanced: A Comprehensive Analysis of Outlook attack Vectors
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Information – Administrative and Support and Waste Management and Remediation Services – Transportation and Warehousing
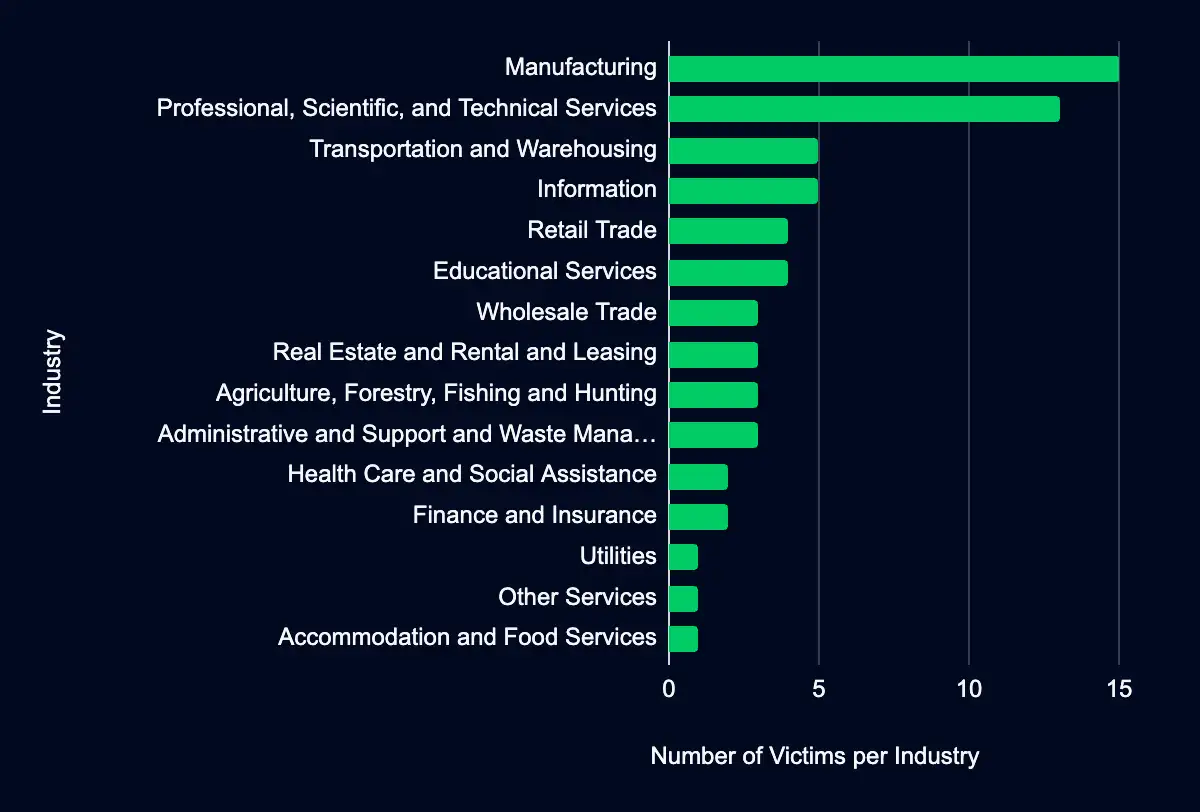
The report reveals that monitored data extortion and ransomware threat groups have listed 65 organizations on their data leak sites in the past week. Among these, 36 victims are in the USA, accounting for over half of all victims listed. The United States was followed by five in the UK, four in Canada, and two in Thailand and Switzerland. The Manufacturing industry suffered the most, with 15 victims. The Professional, Scientific, and Technical Services sector follows with 13 victims. The Transportation and Warehousing and Information sectors had five victims each, and Retail Trade had four victims.
Our analysis strives to be comprehensive, utilizing the most current data available from our dark web monitoring platform. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed. Additionally, we may have omitted victims we could not verify.
As the data set does not include information about the industry, we do our best to classify the victims based on the NAICS industry classification system. This manual effort may introduce other discrepancies, such as misclassifying the industry. We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
CISA Adds 6 CVEs to Known Exploited Vulnerabilities Catalog
Qualcomm Multiple Chipsets CVE-2022-22071, CVE-2023-33063, CVE-2023-33106, and CVE-2023-33107 – Apple Multiple Products CVE-2023-42916 and CVE-2023-42917
In the past week, CISA added six CVEs to its Known Exploited Vulnerabilities Catalog, Vulnerabilities this week affect Qualcomm and Apple products, and their link to ransomware campaigns is currently unknown. Your systems could be at risk from use-after-free, out-of-range pointer offset, integer overflow, out-of-bounds read, and memory corruption vulnerabilities. Explore the report and grasp CISA’s mitigation recommendations. Stay ahead and protect your assets.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2022-22071 | Qualcomm | Multiple Chipsets | Use-After-Free Vulnerability when process shell memory is freed using IOCTL munmap call during process initialization. | 2023-12-26 | Unknown |
| CVE-2023-33063 | Qualcomm | Multiple Chipsets | Use-After-Free Vulnerability due to memory corruption in DSP Services during a remote call from HLOS to DSP. | 2023-12-26 | Unknown |
| CVE-2023-33106 | Qualcomm | Multiple Chipsets | Use of Out-of-Range Pointer Offset Vulnerability due to memory corruption in Graphics with sync points in an AUX command. | 2023-12-26 | Unknown |
| CVE-2023-33107 | Qualcomm | Multiple Chipsets | Integer Overflow Vulnerability due to memory corruption in Graphics Linux while assigning shared virtual memory region. | 2023-12-26 | Unknown |
| CVE-2023-42916 | Apple | iOS, iPadOS, macOS, Safari WebKit | Out-of-Bounds Read Vulnerability that may disclose sensitive information when processing web content. | 2023-12-25 | Unknown |
| CVE-2023-42917 | Apple | iOS, iPadOS, macOS, Safari WebKit | Memory Corruption Vulnerability leading to code execution when processing web content. | 2023-12-25 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share