Diamond Sleet Rains Worldwide, Two New Web Shell Threats, New Botnet GoTitan Discovered, and Malware Shop Persian Remote World Sells RATS
This week: North Korean APT Diamond Sleet conducts a supply chain attack, two threats to web server security from web shells surface, and a new botnet GoTItan is exploiting the ActiveMQ Vulnerability. More plus the latest from data leak sites. Surprisingly, there were no new CVEs announced this week.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- North Korean Threat Actor’s Supply Chain Attack Impacts Over 100 Devices Worldwide
- Undisclosed Web Shell Employs Custom Encoding and Code Execution
- New Site Offering a Remote Access Trojan, Loader, and Other Tools Discovered
- A Dive Into the WSO-NG Web Shell
- ActiveMQ Vulnerability (CVE-2023-46604) Exploited by New Botnet
- Latest Additions to Data Leak Sites
- No New CVEs added this week to the CISA KVE
North Korean Threat Actor’s Supply Chain Attack Impacts Over 100 Devices Worldwide
Diamond Sleet – LambLoad – CyberLink Promeo – Supply Chain Attack – Industries/All
Threat Analysis
Recently, Microsoft detected a supply chain attack involving CyberLink Corp’s video and graphics template-based designer, Promeo. This attack used CyberLink’s update infrastructure, leveraging a Promeo update installer embedded with malicious code that downloaded, decrypted, and loaded a second-stage payload. Microsoft currently tracks the malicious application and associated payloads as LambLoad. The Promeo update installer, signed using a valid certificate issued to CyberLink Corp., included checks to restrict the time window for execution and evade detection by security products. Thus far, Microsoft has detected the malicious update installer on over 100 devices in multiple countries, including Japan, Taiwan, Canada, and the United States. At this time, it is unknown how the threat actor was able to modify the CyberLink Corp’s Promeo update installer.
Before executing any malicious code, LambLoad (the malicious update installer) verifies the date and time of the host system to match a preconfigured execution period. It also employs evasion techniques, such as checking for the presence of security software from FireEye, CrowdStrike, and Tanium, and, if these are detected, continues running the CyberLink software and abandons execution of malicious code. If the software is undetected, the malware connects to one of three URLs, using the static User-Agent string ‘Microsoft Internet Explorer’ to download a second-stage payload disguised as a PNG file. This PNG file contains an embedded payload inside a fake outer PNG header that is carved, decrypted, and launched in memory. When invoked, the in-memory payload attempts to contact two legitimate domains that Diamond Sleet has compromised.
Microsoft attributes this supply chain attack with high confidence to Diamond Sleet, a North Korean threat actor. Microsoft bases this attribution on several factors, including the second-stage payload communicating with infrastructure previously compromised by Diamond Sleet. Diamond Sleet is a North Korea-based activity group that has targeted global industries, particularly in media, defense, and information technology. Their operations focus on personal and corporate data theft, financial gain, and corporate network destruction. Diamond Sleet is known for using a variety of custom malware that is exclusive to the group. Their recent activities have included weaponizing open-source software and exploiting N-day vulnerabilities.
Risk & Impact Assessment
The Diamond Sleet supply chain attack poses significant risks and impacts regarding cybersecurity and broader organizational health. The primary risk lies in the sophisticated nature of the attack, which could lead to widespread system compromise, data breaches, and potential espionage. Organizations that downloaded the malicious CyberLink Promeo software update have the highest risk of unauthorized access to sensitive data, which could result in financial losses, reputational damage, and legal implications. The material impact of this incident is substantial, extending beyond the immediate organizations to their customers, stakeholders, partners, and suppliers.
This attack undermines trust in the security of software supply chains and raises concerns about the integrity of business operations and data confidentiality. The potential for such an attack to disrupt business continuity, erode customer confidence, and strain partner relationships is significant. This underscores the need for a robust cybersecurity posture and proactive risk management strategies to mitigate the far-reaching consequences of such sophisticated cyber threats. The attack’s global reach and the involvement of a state-sponsored actor like Diamond Sleet amplify these risks, highlighting the importance of international cooperation and intelligence sharing in cybersecurity.
Source Material: Microsoft, Diamond Sleet supply chain compromise distributes a modified CyberLink installer
Undisclosed Web Shell Employs Custom Encoding and Code Execution
Web Shell – HrServ.dll – PAExec.exe – Code Execution – Industries/All
Threat Analysis
Kaspersky recently discovered a sophisticated and previously unidentified web shell named hrserv.dll. Kaspersky’s investigation revealed its unique features, such as custom encoding methods for client communication and in-memory execution capabilities. Further analysis led to the discovery of related variants compiled in 2021. To date, Kaspersky has identified only one known victim of this web shell, a government entity in Afghanistan.
According to Kaspersky’s telemetry, the infection chain initiates with the PAExec.exe process, creating a scheduled task named MicrosoftsUpdate [sic]. This task executes a BAT file named JKNLA.bat file, which is responsible for copying hrserv.dll into the System32 directory and configuring a service via the system registry.
The web shell, named hrserv.dll, is a PE32+ executable (DLL) compiled with Microsoft Visual C/C++ and exhibits advanced technical features. It employs Base64 encoding and FNV1A64 hashing algorithms for client-server communication. The web shell initiates an HTTP server using the HTTP server API, registering a specific URL to route incoming requests to its queue.
The web shell activates different functions based on the type of HTTP request received, distinguished by the value in the GET parameter named ‘cp.’ For example, a POST request with a ‘cp’ value of 6 indicates a code execution process, which extracts the value of the NID cookie and applies its custom decoding technique. Then, it writes this decoded value to a specified registry path. The custom-decoded POST data is then copied to the memory, creating a new thread, and the process enters a sleep state.
Another example is a POST request with a ‘cp’ value of 1, which creates a file using the custom decoded NID cookie value and writes the custom decoded POST data to that file. A GET request with a ‘cp’ value of 2 will read a file using the custom decoded NID cookie value and return it as a response, or a GET request with a ‘cp’ value of 4 returns the Outlook Web App HTML data.
In one observed scenario, where the cp value is unknown, it causes the activation of a multifunctional implant in the system memory. The implant creates a file in the TEMP directory, retrieves information from the registry, performs actions based on this information, and records the output of these actions in the created file. As a result, the registry and the temporary file are used as a communication channel between the implant and HrServ. Based on their telemetry, after successfully establishing a foothold and placing the implant in the system memory, the following actions erase previously existing traces by deleting the scheduled “MicrosoftsUpdate” job and the initial DLL and batch files.
Kaspersky’s research uncovered earlier variants of HrServ, dating back to early 2021. While these variants share the custom encoding algorithm, they differ in operational behavior, mainly using a different web shell URL and process creation, retrieving its output through a pipe instead of allocating a memory section and creating a thread.
Attributing the web shell (hrserv.dll) to any threat actor or nation-state is challenging, and the observed TTPs are not associated with any threat actors Kaspersky is tracking. However, Kaspersky assesses that it’s unlikely the threat actors are native English speakers. They used specific GET parameters and language settings in the web shell that specified that the Google search interface be displayed in English, but search results are in Traditional Chinese. Furthermore, the analyzed samples include help strings written in English but have multiple typos.
The web shell is capable and sophisticated, with origins dating back to at least 2021. Its use of different strings for specific conditions and communication strategies indicates a web shell designed for financial gain. Yet, it also exhibits operational characteristics akin to Advanced Persistent Threat (APT) behavior.
Risk & Impact Assessment
The discovery of the web shell is unlikely to pose a significant threat to organizations, primarily due to only one known government organization being a victim. However, the sophisticated nature of this malware, with its advanced encoding methods and in-memory execution capabilities, indicates a high risk of undetected infiltration and data exfiltration. The ability of the web shell to execute code and manipulate system processes through registry and memory implants increases the threat of persistent access and control over compromised systems.
These capabilities substantially threaten the confidentiality, integrity, and availability of sensitive data. The material impact of such a breach is profound, extending beyond the immediate victim to potentially affecting customers, stakeholders, partners, or suppliers by compromising data confidentiality and integrity. The lack of post-compromise details and the difficulty attributing the malware to a specific actor or actors further complicates the threat landscape, making it challenging for organizations to assess their level of risk and effectively prepare and respond. This situation underscores the need for heightened monitoring and robust cybersecurity measures to mitigate the risks and impacts of this threat.
Source Material: Securelist/Kaspersky, HrServ – Previously unknown web shell used in APT attack
New Site Offering a Remote Access Trojan, Loader, and Other Tools Discovered
Persian RAT – Persian Loader – Persian Security – Remote Access Trojan – Loader – Crypter – Industries/All
Threat Analysis
During routine intelligence gathering, Cyble Research and Intelligence Labs (CRIL) came across a new malware loader, Persian Loader, on VirusTotal, first submitted on 26 September 2023 from Great Britain. This discovery led CRIL to a website called Persian Remote World, a platform that sells various malicious tools. Persian Remote World offers malicious software, including Remote Access Trojans (RATs), loaders, and crypters. Persian RAT and Persian Loader are particularly noteworthy for their advanced capabilities.
CRIL identified a sample of the Persian RAT malware on VirusTotal, notable for its relatively large file size of 3.75 MB, which is larger than typical RAT binaries. Upon execution, Persian RAT establishes a mutex named “Persian” through the CreateMutexW() API, a technique used to prevent multiple instances of the RAT on a single system and to coordinate multithreading operations. The RAT then activates critical privileges such as SeShutdownPrivilege and SeDebugPrivilege through the AdjustTokenPrivileges() API, initiating system reboots and modifying other processes memory.
Persian RAT is designed for manual control, awaiting commands from its Command and Control (C2) server to perform malicious activities. Static analysis reveals routines indicative of multiple capabilities. These include firewall manipulation using netsh commands, enabling the threat actor to enable or disable the victim’s firewall. Additionally, it contains a keylogger routine for capturing keystrokes and transmitting them to the actor, who can enable or disable this function as needed.
Beyond keylogging and firewall manipulation, Persian RAT also exhibits cookie and password theft capabilities, specifically targeting popular browsers like Mozilla Firefox, Google Chrome, and Microsoft Edge. Additionally, Persian RAT targets various software applications and games, scanning and exfiltrating crucial files from their directories, including FileZilla, VMware, Telegram, and several others.
Persian RAT incorporates a range of embedded commands, like DISABLEUAC, DISABLEFIREWALL, STARTBOMB, STARTRANSOMWARE, STARTSCREENWATCHING, and ACTIVATEBANKING. These commands suggest they are used to disable User Account Control (UAC) and the firewall, ransomware operations, screen capture, and interactions with banking websites. These commands further demonstrate the RAT’s versatility in conducting various malicious activities. Furthermore, analysis of the RAT’s binary revealed hard-coded strings for financial institutions, suggesting a potential intent to engage in financial fraud and identity theft.
Persian Loader is another malicious tool offered on the Persian Remote World website for a monthly subscription fee of $20. It is designed to load other executable files on victim systems. It employs TCP Sockets to facilitate the execution of second-stage payloads within infected systems. The Persian Loader builder and management tool, Persian X Loader 5.0, was hosted on their Telegram channel for free. This tool allows the creation of a custom listener server, which can be bound to any designated port, acting as a server for the malicious loaders created by the builder. The threat actor can build the malicious loader binary using Persian X Loader 5.0 by incorporating the listener server IP and port within the builder. Once executed on a victim’s system, the newly built executable connects to the listener server, enabling remote control.
The management panel of Persian Loader offers various functionalities, including reconnecting with specific victims, starting and stopping the listening server, executing files on infected systems, and building new loader binaries. This level of control and customization makes Persian Loader a versatile tool for cybercriminals.
Cyble also describes Persian Security as a tool that can encrypt and obfuscate executable files to prevent detection and analysis, also known as a crypter. This crypter is sold for $45 monthly to $650 for a lifetime subscription, making it the most expensive tool.
Cyble, to date, has not identified any activity using Persian Remote World-related tools, but common tactics such as phishing websites and emails, gaming forums, and YouTube comments are likely vectors. These methods are frequently used to deliver loaders and malware. Given the capabilities of Persian Loader and Persian RAT, it’s plausible that threat actors may employ phishing campaigns to deliver the loader to infect systems with the RAT. The use of compromised websites or drive-by download attacks could also serve as potential distribution channels for this malware.
Risk & Impact Assessment
The emergence of the Persian Remote World site, along with its offerings of Persian RAT and Persian Loader, represents an escalation in the cyber threat landscape. The risks associated with these tools are multifaceted, impacting organizational cybersecurity on several levels. Organizations face the risk of data breaches, financial fraud, identity theft, and operational disruptions. The capabilities of these tools, such as keylogging, firewall manipulation, and the targeting of financial institutions, amplify the potential for substantial material impact. This material impact includes the likelihood of sensitive data compromise, which could have far-reaching consequences for customers, stakeholders, partners, and suppliers.
The ease of access to these sophisticated tools raises the threat level, as it lowers the barrier to entry for less skilled threat actors, potentially increasing the frequency and diversity of attacks. The impact of such incidents goes beyond immediate financial losses, potentially extending to long-term reputational damage, legal liabilities, and erosion of customer trust. Therefore, the presence of these tools in the cyber threat landscape necessitates heightened vigilance and robust cybersecurity measures from organizations to mitigate these risks effectively.
Source Material: Cyble, New Persian Remote World Selling Suite of Malicious Tools
A Dive Into the WSO-NG Web Shell
WSO-NG – Web Shell – Industries/All
Threat Analysis
Akamai’s recent blog post on the WSO-NG web shell is the first in a series that sheds light on web shells. Web shells are tools threat actors use to gain and maintain access to openly accessible or compromised web servers. It serves as a backdoor into the network, allowing the threat actor to execute commands remotely and manage files on the server. This web shell is notable for its ability to blend into the server environment, making detection challenging for standard security measures.
The first iteration of the web shell (WSO) can be traced back at least 14 years. Over time, the initial developer of WSO, along with collaborators, consistently delivered improvements to features and addressed bugs. In 2021, a GitHub user revealed an updated iteration of the WSO shell, eventually naming it “wso-ng.php,” which, according to the creator, represented that it is the “New generation of famous WSO web shell.”
To use the WSO-NG web shell, threat actors log in to a page that initially appears as a 404 error page. However, a hidden login form is situated beyond the visible screen area. This deception is achieved using CSS to displace the login form 1,000 pixels to the left.
Threat actors can use several capabilities and integrations after gaining access through the concealed login form. Some of the integrations include VirusTotal (to auto-check IP reputation), SecurityTrails (to show neighbors on the same IP), and ip-info (to show domains on the same server).
One of the reconnaissance features involves retrieving AWS metadata to acquire AWS credentials associated with the active cloud instance, facilitating lateral movement within the cloud account. Another reconnaissance feature is the capability to search for Redis database connections to obtain more extensive access to application data. Redis, an in-memory key-value database, is widely used in contemporary applications, particularly in cloud settings.
WSO-NG also incorporates a built-in php add-filter exploit to circumvent shared web hosting security measures, such as restricting risky PHP functions through the PHP add-filter functionality, which prevents website owners from accessing other sites on the same server. Additionally, it capitalizes on an exploit that auto-elevates & bypasses disabled functions in FastCGI environments, a prevalent configuration in web hosting, enabling it to escalate privileges and establish a foothold at the “root” level.
Risk & Impact Assessment
The successful deployment of the WSO-NG web shell presents significant risks and impacts to organizations, primarily through its sophisticated evasion capabilities and advanced reconnaissance features. The ability of WSO-NG to blend seamlessly into server environments and mimic legitimate processes poses a high risk of undetected intrusion, leading to potential data breaches, unauthorized access to sensitive information, and disruption of critical services.
The material impact of such incidents is substantial, as they can erode customer trust, damage stakeholder relations, and disrupt supply chains. The shell’s capability to facilitate lateral movement within networks is particularly concerning, escalating the risk of widespread system compromise. This threatens the confidentiality and integrity of an organization’s data and poses a severe risk to partners and suppliers who may be indirectly affected through connected systems or shared resources. Bypassing shared web hosting security measures further amplifies these risks. In summary, WSO-NG represents a multifaceted threat that can have far-reaching consequences, extending beyond the immediate target to impact a broader ecosystem of connected entities.
Source Material: Akamai, Defeat Web Shell WSO-NG
ActiveMQ Vulnerability (CVE-2023-46604) Exploited by New Botnet
Apache ActiveMQ CVE-2023-46604 – GoTitan – Botnet – Sliver – PrCtrl Rat – Kinsing – Ddostf – Remote Code Execution – Vulnerability Exploitation – Industries/All
Threat Analysis
In October 2023, a critical vulnerability identified as CVE-2023-46604 was disclosed by Apache, impacting various versions of Apache ActiveMQ. This vulnerability, which involves deserializing untrusted data, poses a significant threat to systems running affected versions of Apache ActiveMQ across any operating system. On 2 November, CISA added CVE-2023-46604 to its Known Exploited Vulnerabilities (KEV) Catalog, highlighting that the vulnerability has been exploited.
In recent weeks, Fortiguard has detected numerous threat actors exploiting CVE-2023-46604 to disseminate diverse malware strains. Their analysis unveiled the emergence of a newly discovered Golang-based botnet named GoTitan and a .NET program called “PrCtrl Rat,” equipped with remote control capabilities.
The exploitation of CVE-2023-46604 begins with a threat actor establishing a connection to ActiveMQ, typically via the OpenWire protocol on port 61616. This phase involves transmitting a specially crafted packet that triggers the system to unmarshal a class under the actor’s control. This action prompts the vulnerable server to retrieve and execute a class configuration XML file from a remote URL, a process requiring the presence of a predefined XML file hosted externally. The known exploitation of this vulnerability notably leverages the “ClassPathXmlApplicationContext” to load a malicious XML application configuration file from a network location via HTTP. This method allows threat actors to define arbitrary code intended for execution on the compromised machine, with parameters such as “cmd” or “bash” to facilitate remote code execution.
GoTitan, the newly discovered botnet exploiting CVE-2023-46604, is written in the Go programming language. This botnet is particularly noteworthy for its targeted approach, as it only provides binaries for x64 architectures. Upon execution, GoTitan performs several checks and creates a debug log file named “c.log,” which records execution time and program status, suggesting that it’s in the early development stage. GoTitan self-replicates by copying itself as “/.mod” within the system and ensures its persistence by registering in the system’s cron. It then communicates with its command and control (C2) server, gathering and transmitting essential information about the compromised endpoint, including architecture, memory, and CPU details. GoTitan maintains its connection with the C2 server by sending a heartbeat signal and awaits further instructions. It supports a variety of distributed denial-of-service (DDoS) attack methods, including UDP, TCP, TLS, and various HTTP methods, showcasing its versatility and potential for widespread impact.
In addition to GoTitan, the exploitation of CVE-2023-46604 has been leveraged to disseminate various other strains of malware and tools. One such tool is Sliver, an advanced open-source penetration testing tool developed in Go. Sliver’s diverse features, designed for each penetration testing stage, make it a potent tool for threat actors. It allows the generation of customized implants capable of evading detection and executing a range of commands on infected systems.
Another significant threat is the .NET program “PrCtrl Rat,” which demonstrates capabilities for remote control and execution. It is distributed via CVE-2023-46604 and exhibits functionalities like file system information retrieval, file upload and download, and a heartbeat signal. Kinsing, a malware known for its involvement in cryptojacking operations, has also been observed exploiting this vulnerability. It performs various actions on compromised systems, including configuration modifications and process cleanups.
Lastly, Ddostf, a malware with a history of targeted Distributed Denial of Service (DDoS) attacks, continues to showcase its proficiency in this domain. It incorporates multiple attack methods and has been adapted to exploit the CVE-2023-46604 vulnerability.
Risk & Impact Assessment
The exploitation of CVE-2023-46604 by the GoTitan botnet and various other malware presents a multifaceted risk landscape for organizations. The primary risk involves unauthorized access and control of affected systems, potentially leading to data breaches, service disruptions, and the compromise of sensitive information. The targeted nature of GoTitan, focusing on x64 architectures, indicates a specific threat to enterprises with significant reliance on such systems, elevating the risk of targeted attacks. The botnet’s capabilities in conducting DDoS attacks further amplify the risk, posing threats to the availability and integrity of critical services.
From an impact perspective, exploiting this vulnerability can have far-reaching consequences, including operational downtime, financial losses, and reputational damage. The material impact is particularly significant, as there is a substantial likelihood that incidents related to this vulnerability could affect not only the direct victims but also their customers, stakeholders, partners, and suppliers. This ripple effect underscores the importance of robust cybersecurity measures and the need for proactive incident response strategies to mitigate the broader implications of such threats.
Source Material: Fortinet, GoTitan Botnet – Ongoing Exploitation on Apache ActiveMQ
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Construction – Transportation and Warehousing – Information
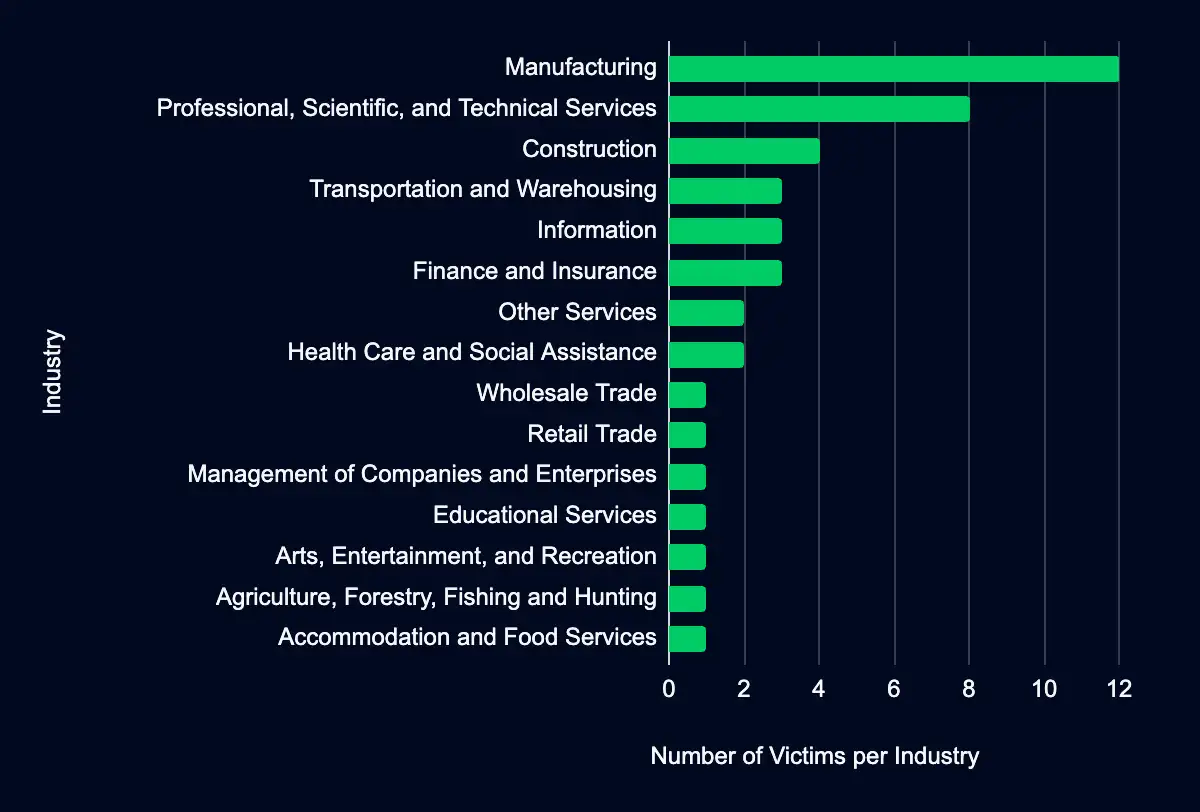
Monitored data extortion and ransomware threat groups have listed 44 organizations on their data leak sites in the past week. Among these, 19 victims are in the USA, followed by five in the United Kingdom, four in Italy, three in Australia, and two in China. The Manufacturing industry suffered the most, with 12 victims. The Professional, Scientific, and Technical Services comes next with eight victims. The Construction had four victims, and Transportation and Warehousing and Information had three victims each.
Our analysis strives to be comprehensive, utilizing the most current data available from our dark web monitoring platform. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed. Additionally, we conduct manual analysis to provide additional data points (country and industry) and omit victims we could not verify or collect the additional data. We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
No new CVEs added this week to CISA Known Exploited Vulnerabilities Catalog
In a rare week, CISA added no new CVEs to its KEV catalog.
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share