Scattered Spider Targets IT Help Desks, Compromised VPN Credentials Lead to Rhysida, and a New Phishing Campaign Delivers Darkgate/Pikabot.
This week: compromised VPN creds lead to Rhysida ransomware on ESXi and Windows systems, APT Scattered Spider is targeting IT Help Desks, a new sophisticated phishing campaign delivers Darkgate and Pikabot, plus fake browser updates and how Citrix Bleed is exploited by LockBit affiliates. All this and the latest from data leak sites and four new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Compromised VPN Credentials Lead to Rhysida Ransomware Deployment on ESXi and Windows Systems
- Scattered Spider Targets IT Help Desks for Data Theft and Extortion, Potentially Deploys Ransomware
- Phishing Campaign Emerges on the Heels of QakBot’s Takedown, Delivers Darkgate and PikaBot
- Fake Browser Update Deploys NetSupport Manager as a Remote Access Trojan
- Citrix Bleed (CVE-2023-4966) Exploited by LockBit Affiliate
- Latest Additions to Data Leak Sites
- CISA Adds 4 New CVEs to its Known Exploited Vulnerabilities Catalog
Compromised VPN Credentials Lead to Rhysida Ransomware Deployment on ESXi and Windows Systems
Rhysida Ransomware – Ransomware – Advanced Port Scanner – ProcDump – PowerShell – PsExec – DataGrabberI.exe – Credential Dumping – VPN Credential Compromise – Industries/All
Threat Analysis
The Rhysida Ransomware Intrusion, as detailed in the Fortinet report, presents a threat actor’s cyber attack chain marked by their persistence in achieving their objectives. The Rhysida Ransomware attack showcased a multi-staged attack with a clear progression from initial access to impact. The threat actor was able to navigate the network, changing and adapting their techniques to overcome obstacles, and ultimately inflicted substantial damage through the deployment of ransomware.
The initial detection of the intrusion was a series of three blocked credential access events, where the threat actor attempted to access and dump the memory of critical processes lsass.exe and the Windows SAM database. These attempts, though blocked, were the first signs of the threat actor’s presence in the network.
The threat actor initially gained access through a compromised VPN, using valid credentials to establish RDP sessions. This initial access did not result from brute force or exploitation of known vulnerabilities, suggesting the possible use of previously compromised credentials. The actor’s early activities included accessing the Active Directory Administrative Center, likely to validate the acquired credentials and assess the domain configuration.
The threat actor demonstrated adaptability and persistence in the discovery and credential access phase. They employed various methods, including downloading tools like Advanced Port Scanner for network reconnaissance and attempting credential dumps using ProcDump and WinPmem. Despite several blocked attempts, their persistence was evident in their continuous efforts to access credentials and gather information about the network.
The threat actor established persistence using PowerShell scripts and the PsExec utility to gain elevated privileges and execute malicious scripts. Notably, their attempts to establish a foothold included using a malicious DLL file and a batch script, which they added to the system scheduler for ongoing execution.
Collection activities involved deploying a PowerShell script designed to harvest browser data and creating custom software, DataGrabberI.exe, for extracting specific file types from the network. This phase demonstrated the actor’s objective to exfiltrate sensitive data before executing their final objective.
The impact of the intrusion was significant. The threat actor successfully deployed ransomware on the organization’s ESXi servers, which did not have endpoint security installed, and several Windows hosts and servers, leading to the encryption of numerous files and virtual machines and the creation of ransom notes. Windows hosts and servers that had endpoint security were not encrypted. Using tools like AnyDesk, WinSCP, and PuTTY in the final stages of the attack underlined the actor’s ability to leverage legitimate utilities to achieve their malicious objectives.
In the Rhysida Ransomware Intrusion, the threat actor almost certainly intended financial gain, primarily through extortion, as evidenced by the ransom note. Their objectives included gaining unauthorized access using compromised credentials, escalating privileges, moving laterally within the network, accessing and collecting sensitive data, and deploying Rhysida ransomware to as many systems as possible. While their tactics and techniques were not sophisticated, they were persistent in their efforts to change and adapt techniques when they were blocked. These actions served the threat actors’ objective to disrupt operations to achieve their intention of financial gain. While the threat actor utilized legitimate tools for malicious purposes, they had access to or developed a custom tool named DataGrabberI.exe, highlighting their resources and capabilities. Overall, the threat actor’s operation was characterized by a high degree of planning, resources, and a focus on financial extortion.
Risk & Impact Assessment
The primary risk stems from significant operational disruption, which affects day-to-day operations and can lead to substantial financial losses due to downtime and potential ransom payments. Another critical risk is the theft and exfiltration of sensitive data, including intellectual property, customer data, or employee information. Furthermore, the incident underscores the risk of relying on single-factor authentication methods, as the initial access was gained using compromised credentials, highlighting the importance of robust authentication mechanisms.
The impact of such a data breach extends beyond immediate financial losses to long-term reputational damage, which can erode customer trust and affect business relationships. The material impact of this intrusion is multifaceted. Operational disruption and potential ransom payments have a direct financial impact. The potential for reputational harm resulting from a perceived inability to safeguard sensitive data can have long-lasting effects on business partners, customers, and market position. Lastly, the incident raises significant concerns about regulatory and legal compliance, especially in industries where data protection is heavily regulated.
Source Material: Fortinet, Analyzing Rhysida Ransomware Intrusion
Scattered Spider Targets IT Help Desks for Data Theft and Extortion, Potentially Deploys Ransomware
Scattered Spider – ALPHV Ransomware – AveMaria – Raccoon Stealer – VIDAR Stealer – Fleetdeck.io – Level.io – Pulseway – Tactical.RMM – Tailscale – Social Engineering – Phishing – SIM Swap Attack – Arts, Entertainment, and Recreation – Accommodation and Food Services – Real Estate and Rental and Leasing – Retail Trade
Threat Analysis
Scattered Spider (Starfraud, UNC3944, Scatter Swine, and Muddled Libra) has been targeting organizations’ IT help desks in the commercial facilities sectors and subsectors, primarily engaging in data theft for extortion and other criminal activities. Notably, their operations may have evolved to include using ALPHV ransomware, potentially adding a new dimension to their TTPs.
CISA categorizes the Commercial Facilities Sector as a diverse range of sites that draw large crowds of people for shopping, business, entertainment, or lodging. The Commercial Facilities Sector consists of organizations, including casinos; hotels and resorts; theme and amusement parks; arenas, stadiums, aquariums, zoos, museums, and convention centers; office and apartment buildings; mixed-use facilities and self-storage; and retail districts and shopping malls.
The threat actors comprising Scattered Spider are social engineering experts and use multiple techniques to obtain credentials, install remote access tools, and/or bypass multi-factor authentication (MFA), especially phishing, push bombing, and subscriber identity module (SIM) swap attacks.
According to public reporting, Scattered Spider threat actors have:
- Posed as company IT and/or helpdesk staff using phone calls or SMS messages to obtain employees’ credentials and gain network access or run commercial remote access tools enabling initial access.
- Posed as IT staff to convince employees to share their one-time password (OTP), an MFA authentication code.
- Sent repeated MFA notification prompts leading to employees pressing the “Accept” button (also known as MFA fatigue).
- Convinced cellular carriers to transfer control of a targeted user’s phone number to a SIM card they controlled, gaining control over the phone and access to MFA prompts.
After gaining network access, the FBI observed Scattered Spider using publicly available, legitimate remote access tools, including Fleetdeck.io, Level.io, Pulseway, Tactical.RMM, and Tailscale, amongst others. In addition, Scattered Spider also uses malware as part of its TTPs, including AveMaria, Raccoon Stealer, and VIDAR Stealer.
Scattered Spider threat actors have historically evaded detection on target networks using living off the land techniques and allowlisted applications to navigate victim networks and frequently modify their TTPs. Observably, Scattered Spider threat actors have exfiltrated data after gaining access and threatened to release it without deploying ransomware; this includes exfiltration to multiple sites, including U.S.-based data centers and MEGA[.]NZ.
More recently, the FBI has identified Scattered Spider has encrypted victim files with ALPHV ransomware after exfiltration. After exfiltrating and/or encrypting data, Scattered Spider threat actors communicate with victims via TOR, Tox, email, or encrypted applications.
The TTPs of Scattered Spider can be broken down into various stages. In the reconnaissance, resource development, and initial access phase, Scattered Spider often begins with broad phishing and smishing attempts against a target using victim-specific crafted domains, such as victimname-sso[.]com, victimname-servicedesk[.]com, and victimname-okta[.]com. In most instances, Scattered Spider conducts SIM-swapping attacks against users who respond to the phishing/smishing attempt. The threat actors then work to identify the personally identifiable information (PII) of the most valuable users that succumbed to the phishing/smishing, obtaining answers to those users’ security questions. After identifying usernames, passwords, and PII and conducting SIM swaps, the threat actors use social engineering to convince IT help desk personnel to reset passwords and/or MFA tokens to perform account takeovers against the users in single sign-on (SSO) environments.
In the execution, persistence, and privilege escalation phase, Scattered Spider will register their own MFA tokens to establish persistence after compromising a user’s account. Further, they have been observed adding a federated identity provider to the victim’s SSO tenant and activating automatic account linking. At this stage, the Scattered Spider controls the identity provider and can choose an arbitrary value for the account attribute, enabling them to sign into any account using a matching SSO attribute.
As a result, this activity allows the threat actors to perform privileged escalation and continue logging in even when passwords are changed. Additionally, they leverage common endpoint detection and response (EDR) tools installed on the victim networks to take advantage of the tools’ remote-shell capabilities to execute commands that elevate their access and deploy remote monitoring and management (RMM) tools.
During discovery, lateral movement, and exfiltration, Scattered Spider performs discovery, searching for SharePoint sites, documentation on credential storage, VMware vCenter infrastructure, backups, and instructions for setting up/logging into Virtual Private Networks (VPN). The threat actors will enumerate the victim’s Active Directory (AD) and perform discovery and exfiltration of the victim’s code repositories, code-signing certificates, and source code. Threat actors have activated Amazon Web Services (AWS) Systems Manager Inventory to discover targets for lateral movement, then move to preexisting and actor-created Amazon Elastic Compute Cloud (EC2) instances. In instances where the ultimate objective is data exfiltration, Scattered Spider uses actor-installed tools to bring data from multiple sources into a centralized database.
Scattered Spider often searches for emails or conversations in platforms like Slack, Microsoft Teams, and Microsoft Exchange online regarding the intrusion and any response to determine if their activities have been discovered and maintain persistence. The threat actors frequently join incident remediation and response calls and teleconferences, likely to identify how security teams are hunting them and proactively develop new attack paths in response to the victim’s response. The procedures to execute this technique include creating new identities in the environment, often with fake social media profiles.
During the impact phase, third parties have reported that Scattered Spider may have encrypted data on a target network with ALPHV ransomware, encrypting VMware ESXi servers and demanding a ransom for decryption. Additionally, Scattered Spider conducted financial theft in numerous ways, including extortion.
Risk & Impact Assessment
The primary risk of Scattered Spider’s activities is significant operational disruption if they deploy ALPHV ransomware. This disruption would impact day-to-day operations, potentially leading to substantial financial losses due to downtime and the possibility of ransom payments. Another critical risk is the theft and exfiltration of sensitive data, including intellectual property, customer data, or employee information, as evidenced by Scattered Spider’s targeted attacks. Additionally, these incidents highlight the vulnerability associated with lax IT help desk processes. Scattered Spider’s initial access often involves socially engineering these departments, underscoring the necessity for more robust procedures.
The impact of Scattered Spider’s breaches extends beyond immediate financial losses, encompassing long-term reputational damage. This damage can erode customer trust and negatively affect business relationships. The material impact of Scattered Spider’s intrusions is multifaceted: operational disruptions and potential ransom demands result in direct financial consequences. Moreover, the reputational harm stemming from a perceived inability to safeguard sensitive data can have enduring effects on business partners, customers, and the organization’s market position. Finally, these incidents raise significant concerns regarding regulatory and legal compliance, particularly in sectors where data protection and privacy are regulated.
Source Material: CISA, Scattered Spider
Phishing Campaign Emerges on the Heels of QakBot’s Takedown, Delivers Darkgate and PikaBot
Malware Distribution – DarkGate – PikaBot – Phishing – JavaScript, Visual Basic Script, & LNK Files – Email Thread Hijacking – Industries/All
Threat Analysis
In September of this year, a phishing campaign emerged, initially focused on disseminating the DarkGate malware. This campaign recently began distributing PikaBot. Cofense states that this campaign is one of the most advanced phishing campaigns currently active in the cyber threat landscape. The campaign’s ability to evolve and employ evasive tactics and anti-analysis techniques has enabled the continued distribution of DarkGate and PikaBot malware.
DarkGate, active since 2018, is a versatile and multifunctional malware with many capabilities. It is adept at downloading and executing files directly into the memory of infected devices, enhancing its stealth and persistence. A notable feature is its Hidden Virtual Network Computing (HVNC) module, which facilitates remote control and surveillance. DarkGate also includes keylogging functionality, enabling it to record keystrokes and capture sensitive information like usernames, passwords, and credit card numbers. It can exfiltrate browsing history and login credentials. DarkGate can also escalate privileges on infected devices, thereby gaining higher levels of access and control. It also can mine cryptocurrency on infected devices.
PikaBot is an emerging malware family that consists of a downloader/installer, a loader, and a core backdoor component. Despite being in the early stages of development, PikaBot already demonstrates advanced techniques in evasion, injection, and anti-analysis. The loader component incorporates sophisticated anti-debugging and anti-VM measures inspired by the open-source Al-Khaser project. PikaBot also utilizes steganography to conceal its payload. It employs a proprietary C2 (Command and Control) framework and supports various commands, including host enumeration and advanced secondary payload injection options.
The timeline of this phishing campaign proceeded with the activities of QakBot malware. The last significant QakBot activity was towards the end of June, with the DarkGate campaign surfacing shortly after that in July. This close succession raises questions about the connections between the two. While direct attribution to QakBot threat actors is complicated, the similarities in tactics raise suspicions. Both campaigns have employed similar methods, such as hijacked email threads for initial infection and unique URL patterns to restrict access. There is a roughly even chance the DarkGate/PikaBot campaign is an evolution or offshoot of the QakBot operation or, at least, is influenced by QakBot due to the shared methodology and near-identical infection chains.
The DarkGate/PikaBot phishing campaign demonstrates a broad targeting strategy, disseminating a large volume of phishing emails across various industries. Cofense has noticed several infection chains, possibly testing different malware delivery options. However, the primary infection chain involves the threat actors forwarding a hijacked email thread with a URL to the target. However, it is unknown how the threat actors obtain these email threads. This URL contains a unique pattern similar to that seen in QakBot phishing campaigns. This URL has filters that restrict access to the malicious file it downloads. When the target clicks on the URL, it downloads a ZIP archive containing a JavaScript file (JS Dropper). This JavaScript file reaches out to another URL to download and run the Darkgate or PikaBot malware. In addition to the primary infection method involving JavaScript files, the DarkGate/PikaBot campaign has employed other file types, including XLL and LNK files and Visual Basic scripts.
Risk & Impact Assessment
The DarkGate/PikaBot phishing campaign presents considerable risks and impacts to organizations across various industries. The primary risk lies in the campaign’s infection methods and the multifunctional capabilities of the malware involved, which could pose a severe threat to data confidentiality, integrity, and availability. The material impact of such a campaign is substantial, as it can lead to the loss of sensitive data and result in operational disruptions. Moreover, the campaign’s success in evading detection increases the likelihood of prolonged, undetected presence in networks, exacerbating the impact. This situation is paramount to the organization’s customers, stakeholders, partners, and suppliers, as it could affect trust and reliability in business operations and data security. The broad targeting strategy of the campaign amplifies its impact, making it a critical concern for organizations that must consider enhanced security measures to mitigate these risks.
Source Material: Cofense, Are DarkGate and PikaBot the new QakBot?
Fake Browser Update Deploys NetSupport Manager as a Remote Access Trojan
NetSupport Manager – Remote Access Trojan – Fake Browser Updates – Phishing Campaigns – Industries/All
Threat Analysis
NetSupport Manager, originally a legitimate tool for file transfers, support chat, inventory management, and remote access, has been repurposed by threat actors as a Remote Access Trojan (RAT). Gaining notoriety in 2020 through a widespread COVID-19-themed phishing campaign, its legitimate origins and ease of access have made it a favored tool among a wide range of threat actors, from novice hackers to sophisticated adversaries. This versatility has led to its prominence in the cyber threat landscape. The delivery methods for NetSupport Manager include fake updates, drive-by downloads, malware loaders, and various phishing campaigns, demonstrating its adaptability in different attack scenarios.
Initial Infection
In recent attacks, deceptive websites and fake browser updates have been primary vectors for deploying NetSupport Manager. However, the specific initial infection method can vary with each threat actor. For example, VMware details an infection chain where a user is deceived into downloading a fake browser update from a compromised website. This is achieved through a PHP script that convincingly mimics an authentic update prompt. The victim, upon interaction, downloads a malicious JavaScript file named Update_browser_10.6336.js.
Payload Delivery and Execution
The Update_browser_10.6336.js file, once executed, establishes connections to the domain implacavelvideos[.]com. It uses PowerShell to bypass execution policies and download additional payloads, such as a PHP file from kgscrew[.]com. This file, encoded in Base64 and compressed into p.zip, is saved in the directory (\appdata\roaming\divx-429) and set to run at system startup. The ZIP file contains multiple NetSupport dependencies and DLLs, culminating in installing NetSupport Manager on the victim’s device. This enables the threat actors to monitor user behavior, transfer files, alter computer settings and spread within the network.
Command and Control (C2) Communication
Following the initial infection, update_browser_10.6336.js utilizes PowerShell to run client32.exe, the NetSupport Manager application, which connects to the C2 server at 5.252.177[.]111 (sdjfnvnbbz[.]pw). VMware’s analysis identified a URL in the PowerShell command line (hXXps://gamefllix[.]com/111.php?9279) used to download further payloads. When connected to this URL, it downloads an obfuscated script contained in a GET response.
Payload Analysis
The script, appearing as base64 encoded and initially unreadable, was found to contain a ZIP archive. VMware created a custom script, which successfully reconstructed this archive, revealing files like Client32.ini, which specifies the GatewayAddress for client32.exe to establish a network connection on port 443 using RADIUSSecret for authentication.
Licensing and Attribution
The NetSupport Licensing information, extracted from NSM.LIC, displayed the licensee name HANEYMANEY, previously linked with TA569, known for delivering payloads via fake browser updates. However, this does not conclusively link TA569 to this attack, suggesting the possibility of a compromised and leaked NetSupport Manager license. This incident highlights the complexities in attributing cyber attacks and the challenges posed by threat actors utilizing legitimate software.
Risk & Impact Assessment
The deployment of NetSupport Manager as a Remote Access Trojan (RAT) presents significant risks and impacts to organizations, extending beyond mere data breaches to encompass broader operational, reputational, and financial ramifications. The RAT’s capability to facilitate unauthorized access and control over networked systems poses a critical risk to the confidentiality, integrity, and availability of sensitive information. This unauthorized access can lead to substantial data exfiltration, system manipulation, and potential service disruptions, directly impacting an organization’s operational capabilities. The versatility and stealth of NetSupport Manager, coupled with its ability to bypass traditional security measures, exacerbate these risks, making detection and mitigation challenging. From a material impact perspective, the incident holds substantial importance to customers, stakeholders, partners, or suppliers due to the potential for compromised data integrity and the resultant erosion of trust.
The RAT’s ability to propagate within a network can lead to cascading effects, affecting not just the primary victim but also interconnected entities, thereby amplifying the impact across the supply chain. This scenario underscores the need for robust cybersecurity measures and incident response plans, as the implications of such an attack extend far beyond the immediate victim, potentially affecting a wide array of external parties who rely on the integrity and availability of the affected systems.
Source Material: VMWare, NetSupport RAT: The RAT King Returns
Citrix Bleed (CVE-2023-4966) Exploited by LockBit Affiliate
Citrix NetScaler ADC and Gateway CVE-2023-4966 – LockBit – Ransomware – PowerShell – Session Hijacking – Vulnerability Exploitation – Industries/All
Threat Analysis
The Citrix Bleed vulnerability, CVE-2023-4966, is a software vulnerability within Citrix NetScaler ADC and NetScaler Gateway appliances, with exploitation activity identified as early as August 2023. The successful exploitation of this vulnerability allows threat actors to bypass MFA and hijack legitimate user sessions. Citrix publicly disclosed CVE-2023-4966 on 10 October, which provided guidance and detailed the affected products, IOCs, and recommendations. CISA added this vulnerability to the Known Exploited Vulnerabilities (KEVs) Catalog based on widely available public exploits and evidence of active exploitation.
This critical vulnerability impacts the following Citrix software versions:
- NetScaler ADC and NetScaler Gateway 14.1 before 14.1-8.50
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.15
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-92.19
- NetScaler ADC and NetScaler Gateway version 12.1 (EOL)
- NetScaler ADC 13.1FIPS before 13.1-37.163
- NetScaler ADC 12.1-FIPS before 12.1-55.300
- NetScaler ADC 12.1-NDcPP before 12.1-55.300
According to data obtained from the FBI and Australian Signals Directorate’s Australian Cyber Security Center (ASD’s ACSC) and voluntarily shared by Boeing, LockBit affiliates have exploited the Citrix Bleed vulnerability.
To exploit Citrix Bleed, LockBit affiliates sent an HTTP GET request with a crafted HTTP Host header to obtain a valid NetScaler AAA session cookie. Exploiting the vulnerability returns system memory information, including the NetScaler AAA session cookie. After acquiring a valid NetScaler AAA session cookie, LockBit affiliates established an authenticated session within the NetScaler appliance without a username, password, or access to MFA tokens.
Once they gained access, the affiliates executed a PowerShell script (123.ps1), which concatenates two base64 strings, converts them to bytes, and writes them to a designated file path. The PowerShell script then executes the resulting file (adobelib.dll) using rundll32. A 104-hex character key must be included in the command to execute the Dynamic Link Library (DLL).
Following execution, the DLL attempts to send a POST request to https://adobe-us-updatefiles[.]digital/index.php (resolves to 172.67.129[.]176 and 104.21.1[.]180 as of November 16, 2023). Although adobelib.dll and the adobe-us-updatefiles[.]digital appears to be a legitimate Adobe file and website; they have no association with legitimate Adobe software and no identified interaction with the software.
Other observed activities include using a variety of TTPs commonly associated with ransomware activity. For example, LockBit affiliates have been observed using AnyDesk, Teamviewer, and Splashtop remote management and monitoring (RMM) tools, Batch and PowerShell scripts, the execution of HTA files using the Windows mshta.exe utility and other common software tools typically associated with ransomware incidents. A list of indicators related to the Lockbit affiliate’s exploitation of CVE-2023-4966 is available in our full report.
Risk & Impact Assessment
The exploitation of the Citrix Bleed vulnerability (CVE-2023-4966) by LockBit affiliates presents significant risks and impacts for organizations globally. The primary risk involves unauthorized access to sensitive systems and data, bypassing multi-factor authentication, and hijacking legitimate user sessions. This vulnerability exposes organizations to potential data breaches, operational disruptions, and financial losses.
The material impact of such incidents extends beyond the immediate organization, affecting customers, stakeholders, partners, and suppliers, particularly in sectors reliant on Citrix NetScaler ADC and Gateway appliances. Exploitation can lead to a loss of customer trust, reputational damage, and legal liabilities if sensitive customer data is compromised or operations are significantly disrupted. Additionally, the TTPs used by LockBit affiliates, including ransomware deployment, further escalate the risk, potentially resulting in widespread data encryption and exfiltration. This scenario underscores the need for robust cybersecurity measures, highlighting the risks where a single vulnerability can have far-reaching consequences.
Source Material: CISA, #StopRansomware: LockBit 3.0 Ransomware Affiliates Exploit CVE 2023-4966 Citrix Bleed Vulnerability
Latest Additions to Data Leak Sites
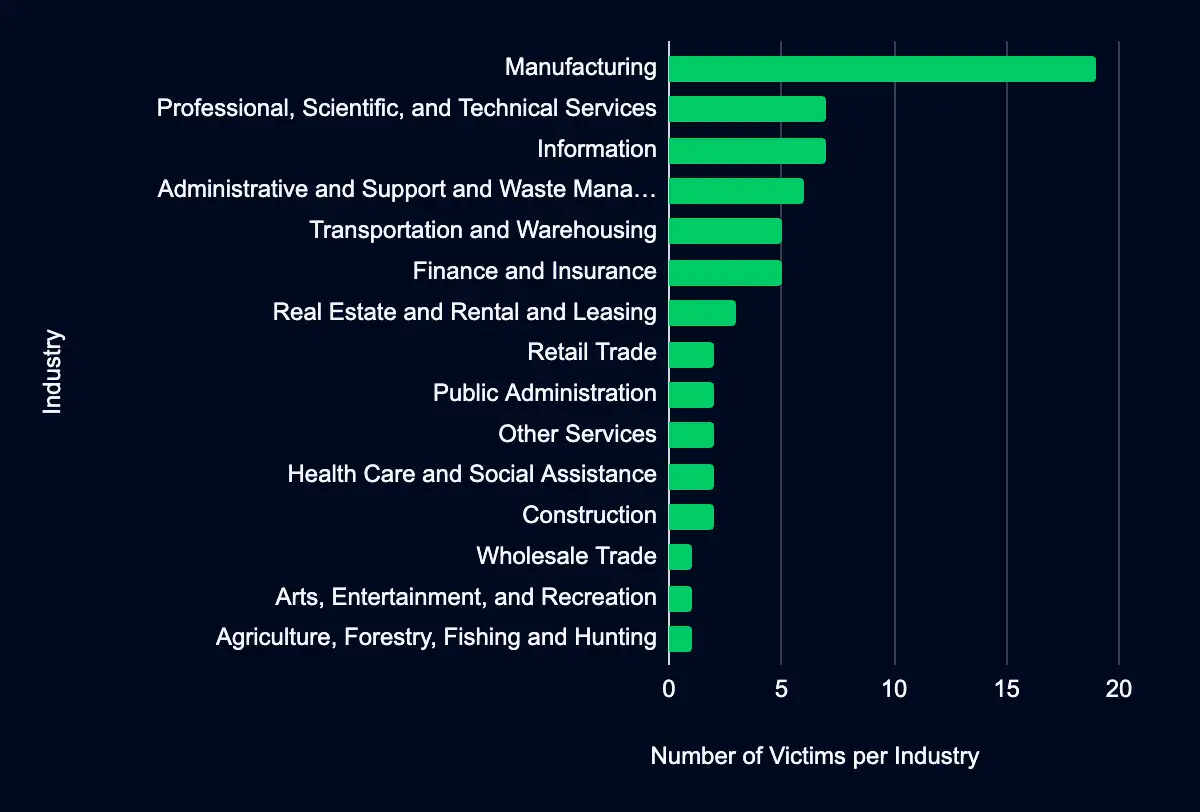
Manufacturing – Professional, Scientific, and Technical Services – Information – Administrative and Support and Waste Management and Remediation Services – Transportation and Warehousing
In the past week, monitored data extortion and ransomware threat groups have added 65 victims to their leak sites in the past week. Among these, 27 victims are in the USA, followed by seven in the UK, six in Germany and Canada, and three in Australia. The Manufacturing industry suffered the most, with 19 victims. The Professional, Scientific, and Technical Services and Information sector comes next with seven victims each. The Administrative and Support and Waste Management and Remediation Services had six victims, and Transportation and Warehousing had five victims.
Our analysis strives to be comprehensive, utilizing the most current data available from our dark web monitoring platform. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed. Additionally, we conduct manual analysis to provide additional data points (country and industry), and we omit victims that we could not verify or collect the additional data.
We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
CISA Adds 4 New CVEs to its Known Exploited Vulnerabilities Catalog
Microsoft Windows CVE-2023-36036, CVE-2023-36025, & CVE-2023-36033 – Juniper Junos OS CVE-2023-36851, CVE-2023-36847, CVE-2023-36846, CVE-2023-36845, & CVE-2023-36844 – SysAid Server CVE-2023-47246
In the past week, CISA added four CVEs to its Known Exploited Vulnerabilities Catalog, impacting GNU, Oracle, Sophos, and Microsoft products. These vulnerabilities can have severe consequences, including local and remote code execution and bypassing security features. It is currently unknown if these vulnerabilities are linked to any ransomware campaigns.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2023-4911 | GNU | C Library | GNU C Library’s dynamic loader ld.so contains a buffer overflow vulnerability when processing the GLIBC_TUNABLES environment variable, allowing a local attacker to execute code with elevated privileges. | 2023-12-12 | Unknown |
| CVE-2020-2551 | Oracle | Fusion Middleware | Oracle Fusion Middleware contains an unspecified vulnerability in the WLS Core Components that allows an unauthenticated attacker with network access via IIOP to compromise the WebLogic Server. | 2023-12-07 | Unknown |
| CVE-2023-1671 | Sophos | Web Appliance | Sophos Web Appliance contains a command injection vulnerability in the warn-proceed handler that allows for remote code execution. | 2023-12-07 | Unknown |
| CVE-2023-36584 | Microsoft | Windows Mark of the Web (MOTW) | Microsoft Windows Mark of the Web (MOTW) contains a security feature bypass vulnerability resulting in a limited loss of integrity and availability of security features. | 2023-12-07 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share