Lace Tempest Storms Zero-day, Confluence Suffers Vulnerability, APT MuddyWater Evolves C2, and BatLoaders Spread Infostealers
This week: APT Lace Tempest exploits a vulnerability in SysAid on-premise servers, an Atlassian Confluence vulnerability is used to deliver Cerber ransomware, APT MuddyWater gets a new C2 framework, we look at the growth of batloaders, and review a threat activity cluster that moved from Vice Society ransomware to Rhysida. All this and the latest from data leak sites and nine new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Lace Tempest Exploited a Zero-day Vulnerability (CVE-2023-47246) in SysAid On-premise Servers
- Atlassian Confluence Data Center and Server Vulnerability (CVE-2023-22518) Exploited to Deliver Cerber Ransomware
- MuddyWater Evolves Operational Tactics, Adopting New Command and Control Framework MuddyC2Go
- How Batloaders Deliver Malware
- Threat Activity Cluster Uses Consistent TTPs While Deploying Two Ransomware Families
- Latest Additions to Data Leak Sites
- CISA Adds 9 New CVEs to its Known Exploited Vulnerabilities Catalog
Lace Tempest Exploited a Zero-day Vulnerability (CVE-2023-47246) in SysAid On-premise Servers
SysAid Servers CVE-2023-47246 – – Lace Tempest – GraceWire Trojan – Cobalt Strike Beacon – WebShell – Vulnerability Exploitation – PowerShell – Educational Services – Health Care and Social Assistance – Manufacturing – Information – Administrative and Support and Waste Management and Remediation Services
Threat Analysis
SysAid is an IT service management solution for managing and tracking IT assets, service requests, and incidents. A component of this system is the SysAid on-premise server, which hosts the software and data locally. This setup is crucial for organizations that prefer maintaining control over their IT service management infrastructure. However, a path traversal zero-day vulnerability, identified as CVE-2023-47246, was discovered in the SysAid on-premise software. This vulnerability enables unauthorized code execution, presenting a severe threat to the security of systems dependent on this software.
With the assistance of Profero, SysAid identified that a threat actor exploited CVE-2023-47246 as a zero-day. Microsoft Threat Intelligence attributed the threat actor to Lace Tempest (also known as Storm-0950), a ransomware affiliate whose activities overlap with FIN11, TA505, and Evil Corp. They are also known to run the Cl0P extortion site. Exploiting this vulnerability allowed them to upload into the webroot of the SysAid Tomcat web service a WAR archive (usersfiles.war) containing a WebShell and additional payloads. The WebShell allowed them to gain unauthorized access and control over the affected systems.
Lace Tempest engaged in a series of activities post-exploitation, including deploying two PowerShell scripts, the GraceWire trojan, and a Cobalt Strike Beacon. Lace Tempest deployed the first PowerShell script through the WebShell to execute a malware loader (user.exe) on the compromised host. This loader injected the GraceWire trojan into one of the following processes: spoolsv.exe, msiexec.exe, or svchost.exe.
The PowerShell script, once executed, first lists files in the C:\Program Files\SysAidServer\tomcat\webapps\usersfiles directory. It then checks for any running Sophos antivirus processes; if none are found, it executes user.exe from the usersfiles directory. After a brief pause, the script performs a clean-up operation by forcefully removing the usersfiles.war file and any user.* files from the specified directory then exits.
The threat actors used the second PowerShell script to disrupt post-incident analysis, which erased evidence of their actions from the disk and the SysAid on-prem server web logs. The PowerShell script initializes paths to the SysAidServer’s Tomcat and log directories and defines patterns to identify specific log entries. The script includes a function (cleanLL) that scans and cleans log files in these directories. For each log file, it checks for lines matching the defined patterns. If matches are found, it creates a backup file ($logFile.bck) containing only the lines that do not match the pattern, and then replaces the original log file with this backup.
After an initial 5-second pause, the script continuously monitors the server environment, executing cleanLL under certain conditions. The first condition checks for the existence of the usersfiles.war file in the $tomcat_dir\webapps directory. If the file is not present, and after ensuring the usersfiles directory is removed, it runs the cleanLL function and exits the loop. The second condition monitors for the presence of a “leave” file in the usersfiles directory. If found, the script removes this file, waits for 5 seconds, runs the cleanLL function, and exits the loop. If neither condition is met, it runs the cleanLL function and continues the loop.
Additionally, the script retrieves a value from an environment variable ($env:SehCore), clears it, and executes it as a command (Invoke-Expression $s). This part of the script is unclear as SysAid does not provide additional context, but it likely executes a command or script stored in the environment variable. However, SysAid stated that the threat actors used an invoke expressions” (IEX) cmdlet in a PowerShell command, which downloaded and ran a CobaltStrike Beacon on victim hosts.
Lace Tempest demonstrates a clear intention toward financial gain through sophisticated cyber operations. Their exploitation of the CVE-2023-47246 vulnerability in SysAid on-premise software showcases their objective to infiltrate systems for data exfiltration, leveraging tools such as a WebShell, Cobalt Strike Beacon, and GraceWire trojan. These capabilities facilitate initial unauthorized access and lateral movement within networks and enable them to potentially exfiltrate, disrupt, destroy, or modify sensitive data and systems, primarily to exert pressure in extortion schemes. While their methods indicate a high level of technical expertise and resourcefulness, suggesting potential for broader data collection, the primary driver of their activities appears to be financial extortion, aligning with their known modus operandi in the cybercriminal landscape.
Risk & Impact Assessment
The scope of the risks and impact is notably significant, particularly across sectors such as Higher Education, Healthcare, Manufacturing, Managed Service Providers, and Human Resources, all of which SysAid actively services. The vulnerability’s exploitation by Lace Tempest, known for their mass exploitation campaigns and data exfiltration for extortion purposes, exacerbates the risk. This threat actor’s ability to perform mass exploitation campaigns indicates a heightened risk for organizations relying on SysAid for IT service management.
Given the broad range of industries SysAid caters to, the potential for widespread and diverse impact is considerable. The lack of data on the status of patch deployment among affected users further compounds the risk, leaving numerous organizations potentially vulnerable to data breaches, operational disruptions, and financial extortion. This situation underscores the urgent need for heightened awareness and proactive measures to mitigate the risks posed by this vulnerability.
Source Material: Microsoft Threat Intelligence, Post on X Nov 8, 2023 8:40pm
Atlassian Confluence Data Center and Server Vulnerability (CVE-2023-22518) Exploited to Deliver Cerber Ransomware
Atlassian Confluence CVE-2023-22518 – Cerber Ransomware – PowerShell – Vulnerability Exploitation – Industries/All
Threat Analysis
On 31 October, Atlassian issued a critical security advisory regarding CVE-2023-22518, an improper authorization vulnerability identified in the Atlassian Confluence Data Center and Server. Initially reported as a potential cause of data loss, this vulnerability was later found to allow unauthorized users to reset and create administrator accounts in Confluence instances, granting them extensive administrative privileges. Significantly, the situation escalated when proof-of-concept (PoC) code for exploiting this vulnerability was leaked to the public on 2 November. This leak marked a turning point, as it provided malicious actors with a blueprint to exploit this vulnerability, raising immediate concerns about its potential misuse in cyberattacks, including the deployment of ransomware.
Trend Micro & Qihoo 360 observed a threat actor, after gaining initial access via the Confluence vulnerability, executed a PowerShell command, which connected to one of three command-and-control (C2) servers (193.176.179[.]41, 193.43.72[.]11, 45.145.6.112, and 193.187.172[.]73) and downloaded a malicious text file. This text file contained decimal-encoded values. Once decrypted, the Cerber ransomware payload was executed on the system. VirusTotal lists these command and control servers hosting multiple files, including Linux bash files. Trend Micro states that one of these Linux bash files (bapo.sh) will also deploy the ransomware.
According to the Chinese security company Qihoo 360, after the ransomware is executed, it collects various configuration information of instant messaging software. It also attempts to obtain login credentials for local FTP and VNC client software. Afterward, the ransomware checks whether compression software is installed in the current system, obtains the browser history and cookie passwords, and checks whether a mail client is installed. The ransomware intends to use this to mine local communication data.
After all initialization and checks are completed, the ransomware encrypts files on the local disk and network share, appending them with the extension “.L0CK3D,” and simultaneously saves a ransom note to various directories. Qihoo 360 also found that after the ransomware completes everything, it deletes the disk shadow copy in the system to prevent the victim user from recovering the encrypted data. Eventually, the ransomware deletes itself to minimize its presence.
Trend Micro compared the characteristics of older Cerber ransomware samples to the ransomware deployed in the exploitation of CVE-2023-022518, determining that the ransomware is indeed Cerber. Additionally, the payment site listed in the ransom note is similar to Cerber’s old payment site, with identical text used for the site’s interface. However, there are some differences between previous Cerber variants and the one seen in this incident. The ransom note for the older Cerber samples was in HTML format, with the appended string being “.locked,” whereas these new samples append the string “.L0CK3D” to the encrypted files.
Risk & Impact Assessment
The exploitation of CVE-2023-22518 by Cerber ransomware operators represents a significant security threat, primarily due to the vulnerability’s potential to grant unauthorized administrative control over Atlassian Confluence instances. This risk extends beyond data loss, severely threatening system integrity and organizational operations. Threat actors exploiting this vulnerability to deploy Cerber ransomware exacerbates this threat, as evidenced by its encryption of local and network files, leading to operational disruptions and potential financial losses. Moreover, the ransomware’s capability to exfiltrate sensitive data, including instant messaging configurations, login credentials, and browser histories, raises serious concerns about data privacy and security.
The impact of these attacks is further intensified by the ransomware’s ability to delete system shadow copies, significantly hindering recovery efforts and amplifying the damage. Additionally, the discovery of Linux bash files associated with the ransomware indicates a cross-platform threat capability, broadening the potential impact across different operating systems. A comparative analysis with previous Cerber ransomware variants reveals an ongoing evolution in its operational tactics, highlighting its continuous development to exploit new vulnerabilities. This evolving threat landscape underscores the need for heightened vigilance and robust security measures to mitigate these risks.
Source Material: Trend Micro, Cerber Ransomware Exploits Atlassian Confluence Vulnerability CVE-2023-22518; Qihoo 360 (Chinese), Alert! Cerber’s new variant L0CK3D ransomware spreads across multiple platforms using vulnerabilities
MuddyWater Evolves Operational Tactics, Adopting New Command and Control Framework MuddyC2Go
MuddyWater – MuddyC2Go – C2 Framework – Advanced Persistent Threat – Phishing – PowerShell – Information – Public Administration – Critical Infrastructure
Threat Analysis
The MuddyWater APT group, operating under the Iranian Ministry of Intelligence and Security (MOIS), has been identified by Deep Instinct as utilizing a new command and control (C2) framework, MuddyC2Go. This framework, written in the Go programming language, represents a significant evolution in the group’s operational tactics.
Deep Instinct’s analysis of anomalies within the PhonyC2 infrastructure led to the discovery of MuddyC2Go, with IP addresses attributed to MuddyWater using this framework dating back to May 2020, with none geolocating to Iran. The transition to MuddyC2Go, likely driven by the need for enhanced stealth and efficiency, followed the public disclosure of PhonyC2’s source code.
Originally, PhonyC2, uncovered by Deep Instinct in April 2023, was a post-exploitation framework generating various payloads for cyber attacks. MuddyC2Go, while not fully exposed in terms of source code, is believed to operate similarly, generating PowerShell payloads for MuddyWater’s operations. Recent tactical shifts include using password-protected archives and executables with embedded PowerShell scripts, enhancing operational stealth.
Investigations into PhonyC2’s infrastructure revealed MuddyWater’s adoption of a Go-based C2 framework as early as 2020. Servers responding with a “web.go” header and Mandiant’s 2022 report on MuddyWater’s use of Go-written malware corroborate this finding. Several IP addresses have been linked to MuddyWater’s usage of MuddyC2Go, indicating the group’s ongoing adaptation and sophistication.
In 2023, MuddyWater demonstrated its evolved tactics through a series of attacks. In July, an attack against a Jordanian company involved “offtec.exe,” connecting to a MuddyC2Go server via dynamic DNS. September saw an attack on Iraqi telecommunications provider Korek, using password-protected archives and PowerGUI-created executables. In October, a MuddyC2Go URL scan from Israel in VirusTotal suggested an attack against Israeli targets. These incidents highlight MuddyWater’s operational deployment of MuddyC2Go in diverse geopolitical contexts.
The shift from PhonyC2 to MuddyC2Go underscores MuddyWater’s continuous evolution. Deep Instinct’s findings, including identifying MuddyC2Go servers hosted at “Stark Industries,” a VPS provider known for malicious activities, reflect the group’s sophisticated approach to cyber espionage.
Risk & Impact Assessment
The adoption of the MuddyC2Go framework by MuddyWater represents a significant escalation in both the sophistication and potential impact of their cyber operations. The primary risk lies in MuddyWater’s enhanced ability to conduct espionage and potentially disruptive cyber activities with increased stealth and efficiency. The shift in tactics, such as using password-protected archives and executables with embedded PowerShell scripts, further complicates detection efforts.
Organizations in sectors historically targeted by MuddyWater, particularly those in telecommunications, government, and critical infrastructure, face a heightened risk of infiltration and data exfiltration. The geopolitical focus of MuddyWater’s activities suggests that critical entities in Israel are at an exceptionally high risk. However, the global nature of cyber threats means that organizations worldwide should not discount the possibility of being targeted. The impact of these threats includes potential loss of sensitive information, disruption of critical services, and damage to organizational reputation.
Source: Deep Instinct, MuddyC2Go – Latest C2 Framework Used by Iranian APT MuddyWater Spotted in Israel
How Batloaders Deliver Malware
Batloader – Malware Loading – AgentTesla – InfoStealer – Phishing – PowerShell – Industries/All
Threat Analysis
Batloaders, a batch file designed to load an embedded payload (loader) or fetch the payload from a command and control (C2) server (downloader), have become a prevalent method for delivering various malware types, notably AgentTesla, a well-known InfoStealer. Batloaders are incredibly versatile and can distribute various malware families, including Ransomware, RATs, and cryptojackers, making them a significant threat in the cyber landscape.
The initial stage often relies on various phishing techniques to trick victims into downloading either a loader or a downloader. A loader directly embeds the malicious payload, while a downloader is a program that fetches the payload from a remote command and control (C2) server. The complexity of this process may vary, depending on how challenging the threat actors want it to be for malware analysts and researchers to dissect the sample.
In the batloader sample analyzed by Seqrite, the batch script initially copies a PowerShell executable and the batch file itself to the temp directory, then executes a PowerShell command with a custom parameter to process a Base64-encoded string. This decoded string further reveals a PowerShell script designed for dynamic code loading and execution, utilizing the last Base64-encoded string in the batch script. The process involves decoding the Base64 string, GZIP decompression, and reversing the output, which unveils a .NET executable. This executable is a variant of AgentTesla. However, it could be other malware that either establishes a connection with a Command and Control server for additional payload or directly infects the machine.
While batloaders may exhibit minor code variations across different attacks, their underlying methodology remains consistent. This consistency highlights their adaptability and widespread use in malicious activities. The design and implementation of batloaders make them ideal for orchestrating multi-staged cyber attacks. Their discreet delivery mechanism ensures the successful execution of the attack’s objectives, making them a formidable tool in the arsenal of cyber threat actors.
Risk & Impact Assessment
Batloaders represent a severe cybersecurity threat due to their versatility in delivering a range of malware, including AgentTesla, ransomware, and remote access trojans, posing significant risks to the confidentiality, integrity, and availability of organizational data. The ease of deployment and evasion techniques of batloaders heighten their threat profile, necessitating focused cybersecurity efforts. Given their potential, organizations should prioritize threats like batloaders to ensure that these threats are addressed promptly and efficiently.
Source: Seqrite, Casting Light on Batloader: An Insight into its Role in Malware Delivery
Threat Activity Cluster Uses Consistent TTPs While Deploying Two Ransomware Families
TAC5729 – Vice Society – Rhysida – Valid Credentials – Microsoft’s Netlogon Remote Protocol CVE-2020-1472 – Public Administration – Transportation and Warehousing – Educational Services – Manufacturing
Threat Analysis
A threat activity cluster Sophos tracks as TAC5279 has demonstrated unique adaptability by shifting from deploying Vice Society to Rhysida ransomware variants. Despite variations in ransomware, their tools, tactics, and procedures remain consistent, including gaining network access via VPNs without MFA. Once inside, they employ various tools such as SystemBC, PortStarter, occasionally Cobalt Strike, Advanced Port/IP Scanner, AnyDesk, PuTTY, and MegaSync. Their operations also involve meticulous data collection using 7zip, followed by data exfiltration through MegaSync, WinSCP, and custom PowerShell scripts. Notably, they have exploited critical vulnerabilities like ZeroLogon, leveraged tools such as Secretsdump for credential harvesting, and dumped the ntds.dit database. They utilize Remote Desktop Protocol (RDP) and PSExec for internal network maneuvering and ransomware distribution.
Sophos has tracked TAC5279 to numerous incidents, allowing them to identify the threat activity cluster’s operational consistency and target diversity. Sophos observed this cluster deploying Vice Society ransomware in various sectors, including public administration, transportation and warehousing, educational services, and manufacturing, before transitioning to Rhysida ransomware in June 2023. The first observed activity in these incidents predominantly involved exploiting VPN accounts without multi-factor authentication (MFA). The dwell times within the targeted networks varied significantly, ranging from a mere four days to over three months, indicating a strategic flexibility in their approach. The malware tools employed in these operations were notably consistent, with PortStarter (to establish C2 communications) being a common element across different incidents. Other tools such as Advanced IP Scanner, PuTTY, temp_l0gs (for credential dumping), RDP, AnyDesk, MegaSync, and exploitation of the ZeroLogon vulnerability were also recurrently used.
TAC5279’s methods for gaining initial access to target networks have been notably consistent, primarily leveraging valid credentials to access VPN accounts without multi-factor authentication (MFA). This approach underscores the importance of robust authentication mechanisms in network security.
In the one incident with a three-month dwell time, TAC5729 first gained access to the network in late October 2022 via valid VPN credentials and immediately executed a Zerologon exploit against the organization’s domain controller using the Mimikatz tool. Following the Zerologon exploit, the cluster went dormant before evidence of lateral movement began in early February 2023.
Once inside the network, the threat actors predominantly used Remote Desktop Protocol (RDP) to move laterally within the network. In one case, the cluster used RDP more than 300 times. In addition to RDP, the cluster also employed tools like PuTTY for SSH connections and PsExec for executing processes remotely. In most cases, the cluster dropped the binary into the network in a tactic known as “Bringing-Your-Own-Binary” (BYOBins) rather than leveraging native Binaries (LOLBins). Furthermore, the cluster was commonly observed using the Advanced Port Scanner and Advanced IP Scanner to identify additional devices within the network to which they could move laterally. Common discovery commands and executables such as whoami, nltest.exe /dclist, quser.exe, query.exe, net.exe, and tracert.exe were also observed.
TAC5729 demonstrated a focused approach to credential access and establishing robust Command-and-Control (C2) channels in their operations. The group frequently exploited the Active Directory environment to access credentials, often using tools like temp_l0gs to dump the ntds.dit database, allowing them to harvest a wide range of user credentials to escalate their access. For C2 communications, TAC5729 consistently used PortStarter and SystemBC. SystemBC has become their primary method for C2, while PortStarter has not yet been observed in any subsequent activities since switching to Rhysida ransomware. In several incidents, the cluster was observed running commands to install AnyDesk on multiple systems within a network for remote access.
TAC5729’s operations also exhibited a systematic approach in the exfiltration and ransomware deployment phases. The cluster prioritized data collection for double-extortion purposes, gathering sensitive data before deploying the ransomware. They commonly used tools like 7zip to compress collected data. The exfiltration process often involved using MegaSync and WinSCP, which enabled large volumes of data to be exfiltrated. Following the data exfiltration, TAC5729 deployed the ransomware to encrypt files within the network, typically executed using PSExec or similar tools, distributing the ransomware payload across multiple systems simultaneously. As previously stated, the choice of ransomware switched from Vice Society to Rhysida ransomware beginning in June 2023.
Based on the comprehensive analysis of TAC5729’s operations, there is high confidence in the transition of this threat cluster to deploying Rhysida ransomware. While marking a change in the ransomware, this transition does not signify a deviation in their overall tactics. TAC5729 has maintained a consistent approach across different attacks and organizations, leveraging similar tools, tactics, and procedures. Despite the change in ransomware, this consistency in their operational methodology indicates a deep-rooted operational doctrine that prioritizes efficiency, stealth, and adaptability. The shift to Rhysida ransomware could be attributed to various factors, including its potential effectiveness, operational convenience, or strategic alliances within the cybercriminal ecosystem. This evolution in their ransomware choice while retaining their core TTPs underscores the human nature of cyber threat actors and highlights that organizations may observe similar modus operandi across various ransomware families.
Risk & Impact Assessment
The activities of TAC5729 pose significant risks and impacts to organizations, transcending traditional quantitative measures and extending into areas of material concern for stakeholders and investors. The consistent use of tools, tactics, and procedures, particularly their shift to deploying Rhysida ransomware, indicates a high risk of operational disruption and financial loss. The cluster’s focus on double-extortion tactics, involving data exfiltration before ransomware deployment, amplifies the risk of sensitive data breaches. This double-extortion tactic poses direct financial risks and carries substantial reputational harm, potentially affecting investor confidence and market perception. The theft or compromise of customer or employee data further escalates these risks, potentially leading to legal liabilities and loss of trust among stakeholders.
Additionally, the cluster’s ability to adapt and maintain persistence within networks suggests a long-term threat to organizational cybersecurity resilience. While the immediate financial impact of an incident might be quantifiable, the broader implications, such as the erosion of customer trust, competitive disadvantage, and regulatory scrutiny, are more challenging to measure but equally critical. These factors collectively contribute to a material impact and should be considered in organizational risk assessments and disclosures.
Source: Sophos, Same threats, different ransomware
Latest Additions to Data Leak Sites
Manufacturing – Educational Services – Professional, Scientific, and Technical Services – Public Administration – Health Care and Social Assistance
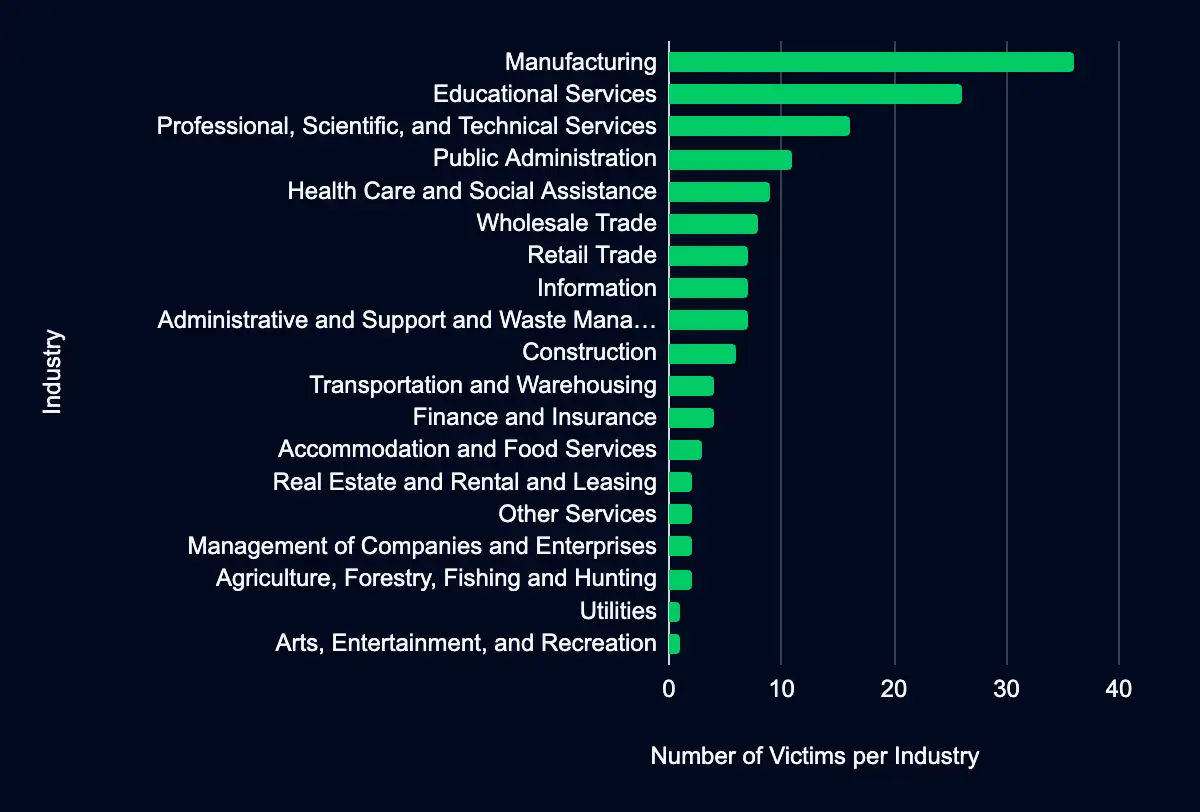
Monitored data extortion and ransomware threat groups added 154 victims to their leak sites in the past week. Among these, 68 victims are located in the USA. The Manufacturing industry suffered the most, with 36 victims. The Educational Services industry comes next with 26 victims, while the Professional, Scientific, and Technical Services sector reported 16 victims. The Public Administration had 11 victims, and Health Care and Social Assistance had nine victims.
Our analysis strives to be comprehensive, utilizing the most current data available from our dark web monitoring platform. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed. Additionally, we conduct manual analysis to provide additional data points (country and industry), and we omit victims that we could not verify or collect the additional data. We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
CISA Adds 9 CVEs to Known Exploited Vulnerabilities Catalog
Microsoft Windows CVE-2023-36036, CVE-2023-36025, & CVE-2023-36033 – Juniper Junos OS CVE-2023-36851, CVE-2023-36847, CVE-2023-36846, CVE-2023-36845, & CVE-2023-36844 – SysAid Server CVE-2023-47246
In the last week, CISA added nine new CVEs to the Known Exploited Vulnerabilities catalog. Vulnerabilities this week affect Microsoft, Juniper, and SysAid products, and it’s unknown if any are linked to any ransomware campaigns.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2023-36036 | Microsoft | Windows Cloud Files Mini Filter Driver | Microsoft Windows Cloud Files Mini Filter Driver contains a privilege escalation vulnerability that could allow an attacker to gain SYSTEM privileges. | 2023-12-05 | Unknown |
| CVE-2023-36025 | Microsoft | Windows SmartScreen | Microsoft Windows SmartScreen contains a security feature bypass vulnerability that could allow an attacker to bypass Windows Defender SmartScreen checks and their associated prompts. | 2023-12-05 | Unknown |
| CVE-2023-36033 | Microsoft | Windows Desktop Window Manager (DWM) Core Library | Microsoft Windows Desktop Window Manager (DWM) Core Library contains an unspecified vulnerability that allows for privilege escalation. | 2023-12-05 | Unknown |
| CVE-2023-36851 | Juniper | Junos OS SRX Series | Juniper Junos OS on SRX Series contains a missing authentication for critical function vulnerability that allows an unauthenticated, network-based attacker to cause limited impact to the file system integrity. With a specific request to webauth_operation.php that doesn’t require authentication, an attacker is able to upload arbitrary files via J-Web, leading to a loss of integrity for a certain part of the file system, which may allow chaining to other vulnerabilities. | 2023-11-17 | Unknown |
| CVE-2023-36847 | Juniper | Junos OS EX Series | Juniper Junos OS on EX Series contains a missing authentication for critical function vulnerability that allows an unauthenticated, network-based attacker to cause limited impact to the file system integrity. With a specific request to installAppPackage.php that doesn’t require authentication, an attacker is able to upload arbitrary files via J-Web, leading to a loss of integrity for a certain part of the file system, which may allow chaining to other vulnerabilities. | 2023-11-17 | Unknown |
| CVE-2023-36846 | Juniper | Junos OS SRX Series | Juniper Junos OS on SRX Series contains a missing authentication for critical function vulnerability that allows an unauthenticated, network-based attacker to cause limited impact to the file system integrity. With a specific request to user.php that doesn’t require authentication, an attacker is able to upload arbitrary files via J-Web, leading to a loss of integrity for a certain part of the file system, which may allow chaining to other vulnerabilities. | 2023-11-17 | Unknown |
| CVE-2023-36845 | Juniper | Junos OS EX Series and SRX Series | Juniper Junos OS on EX Series and SRX Series contains a PHP external variable modification vulnerability that allows an unauthenticated, network-based attacker to control an important environment variable. Using a crafted request, which sets the variable PHPRC, an attacker is able to modify the PHP execution environment allowing the injection and execution of code. | 2023-11-17 | Unknown |
| CVE-2023-36844 | Juniper | Junos OS EX Series | Juniper Junos OS on EX Series contains a PHP external variable modification vulnerability that allows an unauthenticated, network-based attacker to control certain, important environment variables. Using a crafted request an attacker is able to modify certain PHP environment variables, leading to partial loss of integrity, which may allow chaining to other vulnerabilities. | 2023-11-17 | Unknown |
| CVE-2023-47246 | SysAid | Server | SysAid Server (on-premises version) contains a path traversal vulnerability that leads to code execution. | 2023-12-04 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share