Critical Apache ActiveMQ Vulnerability, New Millenium RAT & AsyncRAT, Socks5Systemz Botnet, and Gootloader Adds Gootbot.
This week: a new critical vulnerability emerges in Apache ActiveMQ, new RATs are biting victims, the new Socks5Systemz botnet compromises over 10,000 systems, and Gootloader has a new tool to replace CobaltStrike. All this and the latest from data leak sites and three new CVEs.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
As a leading managed security platform, Deepwatch stands at the forefront of delivering actionable intelligence to keep pace with the ever-evolving threat landscape. Through the Deepwatch Adversary Tactics and Intelligence (ATI) team, we arm your organization with essential knowledge, giving you the power to proactively spot and neutralize risks, amplify your security protocols, and shield your financial stability.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Critical Apache ActiveMQ Vulnerability Exploited in Attempt to Deploy Ransomware
- New RAT Discovered, Capable of Data Exfiltration, Keystroke Logging, and Remote System Control
- New Infostealer Claims Data Exfiltration in Under 10 Seconds
- 10,000 Systems Infected With New Botnet to Proxy Malicious Activity
- Recent AsyncRAT Campaign Employs New Infection Chain, Leveraging Diverse File Types and Process Injection
- GootLoader Employs GootBot to Perform Reconnaissance and Lateral Movement to Infect Additional Hosts
- Latest Additions to Data Leak Sites
- CISA Adds 3 New CVEs to its Known Exploited Vulnerabilities Catalog
Critical Apache ActiveMQ Vulnerability Exploited in Attempt to Deploy Ransomware
Apache ActiveMQ CVE-2023-46604 – Exploitation for Client Execution – HelloKitty Ransomware – Industries/All
Threat Analysis
On October 27, Rapid7 observed similar malicious activity in two distinct Rapid7 customer environments that were running vulnerable versions of Apache ActiveMQ. The adversaries attempted to deploy ransomware on the targeted systems. Rapid7 attributes the ransomware to the HelloKitty family based on the ransom note and available evidence. The affected environments utilized outdated versions of Apache ActiveMQ. Rapid7 tested a publicly available proof-of-concept (PoC) exploit code for CVE-2023-46604 on an ActiveMQ version 5.15.3 and confirmed that the activity observed in customer environments is similar to what they would expect from threat actors employing the PoC to exploit CVE-2023-46604.
Apache ActiveMQ is a message broker service designed to act as a communication bridge between disparate services. ActiveMQ can broker multiple protocol formats, such as OpenWire. Vulnerable versions of ActiveMQ use an OpenWire transport connector, enabled by default and listening for TCP connections on port 61616, which contains a remote unauthenticated deserialization vulnerability, tracked as CVE-2023-46604. A threat actor who exploits the vulnerability can execute arbitrary code with the same privileges as the ActiveMQ server. Apache disclosed this vulnerability and released updated versions of ActiveMQ on 25 October 2023.
To exploit the vulnerability for remote code execution, threat actors can use the public exploit against a vulnerable target to serve a malicious XML file over HTTP to execute the command in the malicious XML file on the targeted system. Notably, a threat actor can host the XML file remotely over HTTP. Based on ShadowServer telemetry, there are approximately 3,580 vulnerable instances of ActiveMQ exposed to the internet. Most of these devices are in Asia, with roughly over 600 devices located in the US.
Regarding the observed malicious activity, Rapid7 observed the parent process, D:\Program files\ActiveMQ\apache-activemq-<version number>\bin\win64, in both incidents listed the specific Apache application being targeted. This behavior matches what Rapid7 observed when they tested the PoC. The actor attempted to load remote files M2.png and M4.png using msiexec.exe. However, their attempts at ransomware deployment resulted, in one instance, numerous unsuccessful attempts to encrypt assets.
Rapid7 analyzed the M2.png and M4.png files and found that both files contained a 32-bit .NET executable internally named dllloader, which loads a Base64-encoded payload. This payload was a 32-bit .NET DLL named EncDLL, exhibiting ransomware-like functionality. It searched for specific processes to stop, encrypted specific file extensions, and appended encrypted files with the extension .locked. Additionally, it included a function for communication to an HTTP server (172.245.16[.]125.) and contained the ransomware note directing communications to occur through the email address service@hellokittycat[.]online. Based on the ransom note and available evidence, Rapid7 assesses that the EncDLL file is related to the HelloKitty ransomware family, whose source code was leaked on a forum in early October.
The threat actor behind the attempted exploitation of Apache ActiveMQ CVE-2023-46604 demonstrated clear intentions of financial gain and disruption, as evidenced by their persistent efforts to deploy HelloKitty ransomware and a ransom note despite initial deployment challenges. Their objectives were to gain unauthorized access to networks, disrupt operations, and extort the victims for financial gain. The capabilities of the threat actor, while advanced enough to exploit a known vulnerability and attempt ransomware deployment, were insufficient to overcome multiple failed attempts. These facts support the assessment that the threat actor possesses an operational capability that is opportunistic, and their technical skill level and resource base align with that of an average cybercriminal as opposed to a highly sophisticated actor with a broad spectrum of custom tools and techniques.
It is unknown if the threat actor acquired the M2.png and M4.png files or developed them using the leaked HelloKitty ransomware source code. If the threat actor created the M2.png and M4.png files using the leaked source code of the HelloKitty ransomware, reflecting their capacity to alter and compile intricate malware programs, providing evidence that the threat actor has significantly greater technical expertise and resources. On the other hand, if the threat actor only obtained these files, it strengthens the assessment that their technical skill level and resources are on par with an average cybercriminal.
Risk & Impact Assessment
The exploitation of CVE-2023-46604 grants threat actors the capability to execute arbitrary code on a vulnerable system, which could lead to a full compromise of the organization’s network. Post-exploitation, the most immediate risk is the establishment of persistence, allowing the adversary to maintain a foothold within the environment, potentially through registry modifications or scheduled tasks. With this persistent access, the threat actor could escalate privileges to gain broader access, evade defenses to remain undetected, and access credentials to further their reach within the network. The adversary could then conduct reconnaissance to understand the environment better, move laterally to compromise additional systems and collect sensitive data aligned with their objectives.
Establishing command and control channels would enable ongoing communication and control over the compromised systems. Ultimately, the threat actor could exfiltrate valuable data or execute an attack with significant impact, such as deploying ransomware, which could disrupt operations, manipulate or destroy data, and severely impact the organization’s ability to conduct business. Each of these actions carries its own risks, from operational disruption and data loss to financial and reputational damage, which could have a profound material impact and lasting effect on the organization’s viability and bottom line.
Source Material: Rapid7, Suspected Exploitation of Apache ActiveMQ CVE-2023-46604
New RAT Discovered, Capable of Data Exfiltration, Keystroke Logging, and Remote System Control
Millenium RAT – Remote Access Trojan (RAT) – Telegram-based Command and Control (C2) – Shinyenigma (GitHub account promoting the RAT) – Data Exfiltration, Keystroke Logging, and Remote Control – Malware Sale and Distribution – Industries/All
Threat Analysis
CYFIRMA discovered a GitHub account named “Shinyenigma,” promoting the sale of a new remote access trojan (RAT) dubbed Millenium RAT. This RAT boasts a suite of capabilities, including data exfiltration, keystroke logging, and remote system control, all facilitated through a Telegram-based command and control (C2) infrastructure. Since CYFIRMA’s initial discovery, the Millenium RAT has evolved, with its developers releasing version 2.5, which not only refines its existing functionalities but also introduces new features that enhance its stealth and operational flexibility, signaling a continuous and concerning development in its threat potential.
CYFIRMA was able to obtain and analyze Millenium RAT version 2.4. Their analysis revealed that Millenium RAT version 2.4 exhibits a sophisticated array of functionalities designed for data theft and system manipulation. Upon execution, it seeks out the infected device’s geolocation details via a GET request to ip-api[.]com. It then decodes its configuration from a local file, employing a custom Rot13 encoding to interpret operational parameters critical for its execution.
The RAT adeptly avoids detection through various evasion techniques, including virtual environment detection and debugger interference, while simultaneously gathering antivirus information to tailor its infiltration. It ensures persistence through registry modifications for autorun capabilities and meticulously manages its presence on the system by installing itself in a specified location and removing traces post-operation. The RAT employs a Telegram bot for executing commands, including downloading files, executing a file, copying a file from one location to another, taking screenshots of the desktop, stealing specified files, and harvesting browser data, which it organizes, compresses, and exfiltrates to an external server via the Telegram API.
Since CYFIRMA discovered the RAT, the developer has updated the version to 2.5, showcasing the malware developer’s commitment to enhancing its efficacy and evasiveness. The GitHub account directs parties interested in purchasing lifetime access or older versions of the RAT to contact @shinyenigma on Telegram.
The Millenium RAT’s structure and modules resemble an archived RAT named ToxicEye RAT, which hasn’t received updates for approximately the last three years. According to CYFIRMA, the code, namespaces, function names, and arguments are similar to those used in ToxicEye RAT across the various modules.
Risk & Impact Assessment
Millenium RAT poses severe risks, with the potential to precipitate a cascade of detrimental impacts on an organization’s operations and financial health. The RAT’s sophisticated data exfiltration and system manipulation capabilities could lead to substantial data breaches, compromising sensitive information and intellectual property, resulting in material financial losses, operational disruptions, and erosion of customer trust.
Such incidents could further incur regulatory fines, legal costs, and necessitate significant resource allocation for incident response and system remediation. The organization’s reputation could suffer lasting damage, potentially affecting net sales, revenues, and competitive positioning. Collectively, these factors underscore the criticality of robust cybersecurity defenses to mitigate the risks associated with the Millenium RAT and safeguard the organization’s continuity and integrity.
Source Material: Cyfirma, Unveiling a New RAT: Millenium RAT
New Infostealer Claims Data Exfiltration in Under 10 Seconds
Trap Stealer – Infostealer – Discord Webhooks (data exfiltration method) – Data Exfiltration and Credential Theft – Industries/All
Threat Analysis
Trap Stealer, identified by Cyble on October 25th on VirusTotal, is a multifaceted, Python-based data-stealing malware publicly available on GitHub. This Stealer can exfiltrate a broad spectrum of sensitive information from compromised systems in 6 to 10 seconds, as claimed on the GitHub repository.
The malware’s functionalities are extensive, including the theft of cookies, browsing histories, Discord tokens, clipboard contents, cryptocurrency wallet data, WhatsApp files, and more. It transmits the stolen data to threat actors (TAs) via Discord webhooks at predetermined intervals. Trap Stealer can even cause a Blue Screen of Death (BSOD) after data exfiltration.
The malware’s stealth is further augmented by its ability to hide behind seemingly innocuous tools and its injection into Discord’s core files to monitor user actions. It ensures persistence through startup mechanisms and employs anti-debugging techniques to evade detection. Trap Stealer also limits its operations to avoid triggering security systems, and it can self-delete after completing its data theft operation.
The malware’s data theft process is comprehensive, targeting a wide range of information from credentials and data stored in browsers to private Discord information. It can terminate processes, copy and compress files, and steal sensitive data based on customizable keywords. Trap Stealer’s ability to steal and transmit files related to gaming applications, crypto wallets, and browser extensions makes it a significant threat. It even manipulates the Discord application’s core component to harvest user data, including sensitive financial information.
Risk & Impact Assessment
Trap Stealer, particularly the theft of credentials, highlights a grave concern for future malicious activities such as ransomware attacks or further data theft. The credentials harvested from browsers provide cybercriminals deeper access to corporate networks. Once inside, they can deploy ransomware, locking critical files and systems and demanding hefty ransoms for their release. This not only disrupts operations but also places sensitive data at risk of being stolen and sold or used as leverage in negotiations. The stolen credentials also open the door for more targeted and sophisticated data theft, enabling attackers to bypass security perimeters and access restricted areas undetected.
The aftermath of such incidents can be devastating, leading to prolonged downtime, financial losses, and a tarnished reputation. Moreover, using stolen credentials in subsequent attacks complicates attribution, hinders legal proceedings, and challenges compliance with regulatory standards, further exacerbating the impact on victims. The potential for such credentials to be used in various criminal activities makes Trap Stealer a particularly insidious threat in the cyber landscape.
Source Material: Cyble, New Open Source ‘Trap Stealer’ Pilfers Data in Just 6 Seconds
10,000 Systems Infected With New Botnet to Proxy Malicious Activity
Socks5Systemz – PrivateLoader – Amadey – Proxy Botnet – Industries/All
Threat Analysis
Socks5Systemz is an emergent proxy service that leverages a network of infected computers, which serve as nodes to route malicious traffic. Its primary purpose is to obscure the origins of cyber attacks and illicit activities by funneling them through these compromised systems, effectively masking the actual IP addresses of threat actors. The service utilizes the SOCKS5 protocol, known for its ability to handle various traffic types and protocols, providing a versatile and resilient platform for cybercriminals. By infecting machines with the proxy bot payload through various methods, Socks5Systemz operators can expand their botnet infrastructure, enabling a distributed and hard-to-trace network that complicates attribution and hinders cybersecurity efforts.
Bitsight observed the Socks5Systemz distributed by PrivateLoader and Amadey, two malware distribution systems. PrivateLoader is a pay-per-install (PPI) scheme that cybercriminals use to disseminate various types of malware by bundling it with legitimate software downloads or updates. Amadey, on the other hand, is a straightforward malware loader capable of delivering a range of payloads.
The technical analysis of Socks5Systemz reveals a sophisticated loader and proxy bot payload designed for stealth and persistence. The loader, which initiates the infection and injects the proxy bot payload in memory, gives users an install and start option. The install option is responsible for setting up the persistence on the system by copying the loader and creating a Windows service to run the copied loader. The start option will create a new thread to launch the loader’s main function, loading the resource and decoding it, which is a valid DLL file containing the proxy bot that will be injected in memory.
The proxy bot payload, approximately 300 KB, is initialized by setting system architecture flags and generating a unique client ID from the system’s Windows directory creation date. On its first run, it records the system’s current time in a file, revealing the time of infection. It also attempts to fetch a PDF from an actor-controlled domain. Bitsight speculates that this PDF is for system infection validation and telemetry purposes. The payload then seeks to establish communication with a command and control (C2) server, first by generating domain names through an algorithm and resolving them via hardcoded threat actor-controlled DNS servers or by sending a GET request to a specific endpoint. The HTTP response is the IP address of an active C2 server after RC4 encryption processes. After getting the IP address of an active command and control server, the bot is ready to start the C2 communications by sending another HTTP GET request to the C2 server.
Once connected to the C2 server, the bot receives HTTP responses with commands encrypted with the same RC4 key, the most critical being the ‘connect’ command. This command instructs the bot to join the backconnect server on TCP port 1074, integrating it into the proxy network. The bot, now functioning as a proxy, is assigned a unique server port to channel traffic from clients, who must have their IP whitelisted or possess login credentials to utilize the service. This sophisticated mechanism allows the bot to serve as a node in the larger proxy infrastructure, facilitating anonymous traffic routing for the clients of the Socks5Systemz service.
Bitisght identified at least 53 servers related to this botnet, all located in Europe and distributed across France, Bulgaria, Netherlands, and Sweden. The infrastructure is made up of servers with several purposes, including Proxy bot C2 servers, Backconnect servers, custom DNS servers (hardcoded in the proxy bot samples), the server used by the bots to get the online C2 server address, and the proxy checker application.
During the investigation, Bitsight discovered a Telegram user selling access to a complete proxy service called BoostyProxy that matches the Backconnect IP addresses employed by Socks5Systemz. The service has two subscription options: standard and VIP. The difference is the standard subscription only allows one proxy type and does not support multithreading. The VIP subscription, on the other hand, supports multiple proxy types and multithreading.
Prices for the standard proxy range from $1 for a single day to $28 for three months, while the VIP service ranges from $22 for 100 threads for a single day to $4,000 for 5,000 threads for three months. While subscribing to the service, users must provide the IP address from where they will access the proxies. Once the subscription process is complete, the user’s IP address will be whitelisted across the botnet, and users can download the list of available Backconnect servers and the TCP ports assigned to the infected systems.
Since the beginning of October, Bitsight has observed approximately 10,000 systems communicating with the Backconnect servers. The top 10 most affected countries are, in order, India, Brazil, Colombia, South Africa, Bangladesh, Argentina, Angola, United States, Suriname, and Nigeria.
Risk & Impact Assessment
In assessing the risks and impacts of Socks5Systemz, customers should prioritize this threat due to its multifaceted implications. The proxy service’s ability to anonymize malicious traffic poses a significant risk by complicating the attribution of cyber attacks, potentially allowing threat actors to bypass geo-restrictions and defenses with relative impunity. The widespread distribution of the botnet indicates a high impact, with a diverse victim profile spanning numerous countries. This global reach suggests that various sectors could be at risk.
Furthermore, BoostyProxy’s low cost and ease of access amplify the risk by lowering the barrier to entry for cybercriminals. The botnet’s robust infrastructure adds to the urgency of addressing this threat. Customers should weigh these risks against their current security posture and resource allocation to ensure a focused and effective response, recognizing that failing to prioritize this threat could lead to significant operational disruptions and reputational damage.
Source Material: Bitsight, Unveiling Socks5Systemz: The Rise of a New Proxy Service via PrivateLoader and Amadey
Recent AsyncRAT Campaign Employs New Infection Chain, Leveraging Diverse File Types and Process Injection
AsyncRAT – Remote Access Trojan (RAT) – Infostealer – PowerShell Execution – Phishing – Process Injection – Credential Theft – Industries/All
Threat Analysis
McAfee Labs recently identified and analyzed a sophisticated campaign involving AsyncRAT, a type of malware known as an Asynchronous Remote Access Trojan, employing a new infection chain. The infection chain is notable for its stealthy approach, utilizing a variety of file types and obfuscation techniques to bypass antivirus solutions and establish persistent remote access to the infected systems.
The infection process begins with an email that contains a malicious URL. When the recipient clicks on this link, an HTML file is downloaded. This file embeds an ISO image with a Windows Script File (WSF). The WSF contains tags, which are responsible for establishing a connection to a domain, setting the stage for the next phase of the infection.
Once the connection is established, the WSF file fetches a text file that contains a PowerShell command. This command subsequently retrieves a second PowerShell script from another URL. This second script drops four files (xral.ps1, hrlm.ps1, xral.vbs, and 1.bat) onto the system. The contents of these four files are embedded within the second PowerShell script. The script then proceeds to create a folder named “xral” in the ProgramData directory, where it writes and extracts these files, facilitating the next steps of the infection.
One of the PowerShell scripts (xral.ps1) creates a scheduled task to ensure the malware’s persistence on the system. It also executes the VBS file (xral.vbs), which triggers the BAT file (1.bat), which is responsible for executing the final PowerShell script (hrlm.ps1). This chain of executions is strategically designed to circumvent static and behavior-based antivirus detections. The execution chain of these scripts is as follows: xral.ps1 > xral.vbs > 1.bat > hrlm.ps1.
The final PowerShell script (hrlm.ps1) contains a Portable Executable (PE) file in hexadecimal format, which is injected into the legitimate process “RegSvcs.exe” using the PowerShell script’s Reflection Assembly load functionality. This technique allows the threat actors to covertly operate within the system by hijacking a trusted application.
After the successful injection, the compromised RegSvcs.exe connects to the AsyncRAT server. This connection is used to control the infected system remotely and to exfiltrate data. This AsyncRAT sample logged keystrokes, exfiltrated credentials and browser-related data, and searched for cryptocurrency-related information, which is sent to the IP address 45[.]12.253.107 on port 8808.
In summary, the infection chain observed by McAfee begins with a malicious link in a spam email. Once the recipient clicks the URL, it will download an HTML file containing an ISO. Within the ISO file, a WSF script connects to an external URL, downloading a PowerShell script, which, in turn, initiates a series of file executions and ultimately injects a PE file into the legitimate “RegSvcs.exe.” This final process connects to an AsyncRAT server. The malware exhibits keylogging capabilities, records user activities, and steals credentials, browser data, and crypto-related information. The data is exfiltrated to 45[.]12.253.107 over port 8808. This intricate chain leverages diverse file types and obfuscation methods to avoid detection, ultimately resulting in the threat actor gaining remote control and successfully stealing data.
Risk & Impact Assessment
The discovery of AsyncRAT’s new infection chain signals a considerable risk to organizations, primarily due to its advanced evasion capabilities and the multifaceted nature of its attack vector. The risk is heightened by the RAT’s functionality to stealthily exfiltrate credentials and sensitive data, which could be exploited directly or monetized on the dark web. The unauthorized access gained by AsyncRAT can serve as a gateway for secondary attacks, such as ransomware deployment or further data breaches. The compounded impact of these risks includes not only immediate data loss and system compromise but also the long-term ramifications of enabling subsequent cybercriminal activities. This cascading effect underscores customers’ need to prioritize this threat, focusing their resources on mitigating the risks associated with AsyncRAT to prevent a chain reaction of cyber threats that could lead to severe operational, financial, and reputational harm.
Source Material: McAfee, Unmasking AsyncRAT New Infection Chain
GootLoader Employs GootBot to Perform Reconnaissance and Lateral Movement to Infect Additional Hosts
GootLoader – GootBot – SEO Poisoning – Compromised Websites – Industries/All
Threat Analysis
IBM X-Force has observed a significant evolution in GootLoader campaigns by deploying a new payload called GootBot that causes GootLoader to move laterally within a network, infecting additional hosts. Initially observed as initial access malware, Gootloader’s primary function was to facilitate the entry of threat actors into a network. However, with the advent of GootBot, the threat actors have augmented their arsenal with a tool designed explicitly for lateral movement and post-exploitation activities.
GootLoader initiates the infection process through SEO poisoning, with the user visiting a compromised site and downloading a malicious archive file. This file typically contains a heavily obfuscated JavaScript file, which marks the first stage of a GootLoader infection. Upon execution, this JavaScript file strategically drops another JavaScript file into an existing subfolder within the %APPDATA% directory using a non-descript English filename. The subfolder selection is not random but is calculated based on the number of subfolders present. Please see the Adversary Tactics and Intelligence team’s Threat Activity Intel Report for a more detailed analysis of the infection chain.
Rather than directly executing the second-stage JavaScript, GootLoader establishes persistence by scheduling a task to run the second-stage JavaScript file. This scheduled task contains parameters that ensure its execution while maintaining a low profile within the system. Once the second stage is initiated, it executes a PowerShell script that represents the third stage of the infection. This third-stage script gathers system information and uploads it to any of its ten hardcoded C2 servers. Gootloader uses hacked WordPress sites to run their C2 servers, leading to C2 URL paths ending with “/xmlrpc.php.” The malware expects the C2 to respond with data that contains a PowerShell script that Gootloader executes in an endless loop, giving the actor the ability to make the C2 respond with varying PowerShell payloads.
X-Force has observed C2 servers responding with a new payload they call GootBot, with a single C2 server address. GootBot will first send a GET request to its C2 server, requesting PowerShell tasks. In response, the C2 server will send a string consisting of a Base64-encoded payload, with the last eight characters being the task name. GootBot will decode the payload and inject it into a simple scriptblock before executing it in a new background job. This injection allows the PowerShell payload to run asynchronously without creating a child process, potentially resulting in fewer EDR detections.
Once GootBot receives a task from the C2, the next loop iteration will start by querying the task result for every child job requested by the C2 server. If the job has been completed, it will return the job results. If it has not been completed yet, it will send the string “E1” or the string “E2” if the job cannot be found. The job results are then concatenated for all requested tasks. The resulting string is obfuscated using a technique from previous Gootloader JavaScript samples. GootBot will then send a POST request to its C2 server, expecting a response containing the next task.
One of the first tasks GootBot runs is a reconnaissance script containing the unique GootBot ID for the host. System information, like the domain user name, hostname, and IP address, is collected and returned to the job handler.
GootBot is also designed to spread laterally throughout the environment. Once an initial host is infected, GootBot receives several scripts enumerating the host and the domain. GootBots’ C2 infrastructure can generate large numbers of GootBot payloads to be disseminated, each with a different C2 address to contact. These payloads are deployed in an automated fashion by lateral-movement scripts, which may lead to the reinfection of the host multiple times. Lateral-movement scripts use WinRM in PowerShell, either via WMI or the “Invoke-Command” Cmdlet. Other samples include copying payloads via SMB and using WinAPI calls to SCM (Service Control Manager) to create remote services and scheduled tasks. In some cases, GootBot also uses exfiltrated credentials to spread.
A Gootloader infection may quickly lead to deploying additional tools such as Cobalt Strike, SystemBC, and domain compromise scripts, including Kerberoasting attacks. Another observed behavior is the exfiltration of sensitive information, including the LSASS process dump using Procdump or the Minidump functionality of “comsvcs.dll” and SAM, SYSTEM, and SECURITY registry hives. In addition, Gootloader infections have led to ransomware deployment.
Risk & Impact Assessment
The emergence of GootBot as an evolution of GootLoader represents a heightened risk to organizations due to its sophisticated mechanisms for stealth and lateral movement, which can lead to widespread network compromise before detection. The risk is compounded by Gootloader’s ability to execute various disruptive actions, from data exfiltration to ransomware deployment. The impact of such a breach is multifaceted, affecting not only the immediate security posture but also having potential regulatory, reputational, and financial repercussions.
Given these factors, prioritizing mitigating threats posed by GootLoader is crucial; failure to do so could result in significant operational disruption and compromise of sensitive information. In the context of resource allocation and threat prioritization, GootLoader’s new capabilities warrant a high-priority response to ensure that defenses are calibrated to the subtleties of its TTPs and the broader implications of its deployment within targeted networks.
Source Material: IBM XForce, GootBot – Gootloader’s new approach to post-exploitation
Latest Additions to Data Leak Sites
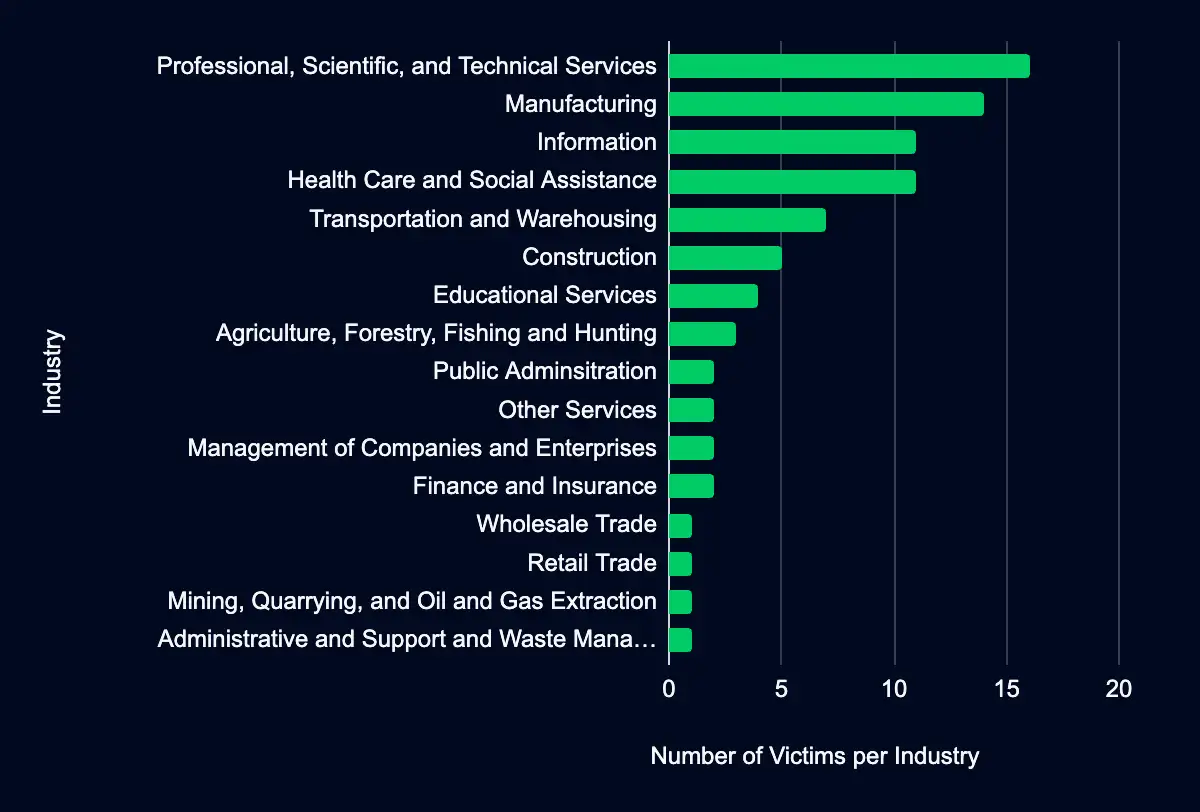
Manufacturing – Professional, Scientific, and Technical Services – Public Administration – Health Care and Social Assistance – Finance and Insurance
In the past week, ransomware groups monitored data extortion and ransomware threat groups have added 83 victims. Among these, 36 victims are located in the USA. The Professional, Scientific, and Technical Services industry suffered the most, with 16 victims. The Manufacturing industry comes next with 14 victims, while the Information sector and Health Care and Social Assistance each reported 11 victims. The Transportation and Warehousing industry had seven victims.
Our analysis strives to be comprehensive, utilizing the most current data available from dark web monitoring tools. However, it is crucial to acknowledge this data set’s inherent limitations and uncertainties. Despite our best efforts, there may be instances where the data includes organizations not actually listed on leak sites or, conversely, omits victims that we could not verify at the time of our review.
Additionally, our analysis may not encompass all affected entities, particularly those whose country or industry could not be confirmed. We also recognize that our data set may not represent the full scope of ransomware victims, as it primarily reflects those who have been targeted and potentially compromised, excluding those who chose not to engage or pay the demanded ransom. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
CISA Adds 3 CVEs to Known Exploited Vulnerabilities Catalog
IETF Service Location Protocol (SLP) CVE-2023-29552 – Atlassian Confluence Data Center and Server CVE-2023-22518 – Apache ActiveMQ CVE-2023-46604
In the past week, CISA added three CVEs to its Known Exploited Vulnerabilities Catalog, impacting IETF, Atlassian, and Apache products. These vulnerabilities can have severe consequences, including denial-of-service, data loss, and running of shell commands. It is currently unknown if these vulnerabilities are linked to any ransomware campaigns.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor/Project | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2023-29552 | IETF | Service Location Protocol (SLP) | Service Location Protocol (SLP) Denial-of-Service VulnerabilityThe Service Location Protocol (SLP) contains a denial-of-service (DoS) vulnerability that could allow an unauthenticated, remote attacker to register services and use spoofed UDP traffic to conduct a denial-of-service (DoS) attack with a significant amplification factor. | 2023-11-29 | Unknown |
| CVE-2023-22518 | Atlassian | Confluence Data Center and Server | Atlassian Confluence Data Center and Server contain an improper authorization vulnerability that can result in significant data loss when exploited by an unauthenticated attacker. There is no impact on confidentiality since the attacker cannot exfiltrate any data. | 2023-11-28 | Unknown |
| CVE-2023-46604 | Apache | ActiveMQ | Apache ActiveMQ contains a deserialization of untrusted data vulnerability that may allow a remote attacker with network access to a broker to run shell commands by manipulating serialized class types in the OpenWire protocol to cause the broker to instantiate any class on the classpath. | 2023-11-23 | Unknown |
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share