Russian Turla Deploys New Arsenal, Attackers Exploit ScreenConnect to Deliver Malware, and Cozy Bear Goes Cloud
This week: Russian APTs Turla and Cozy Bear loom large, the Connectwise ScreenConnect exploit does damage, Gootloader spreads more malware, iSoon leaks data from Asia Pacific governments, and the latest from data leak sites and CISA.
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
- Russian APT Turla Deploys New Arsenal and C2 Mechanism with Web Shell Capabilities
- Threat Actors Exploit ConnectWise ScreenConnect to Deliver Malware
- How APT29 is Adapting to Government and Corporations Move to Cloud Infrastructure
- Gootloader Facilitates Compromise of Domain Controllers, Backup Servers, and Remote File Servers
- i-Soon Data Leak Analysis
- Latest Additions to Data Leak Sites
- CISA Adds CVE-2024-1709 CVEs to Known Exploited Vulnerabilities Catalog
Russian APT Turla Deploys New Arsenal and C2 Mechanism with Web Shell Capabilities
Threat Actor – Cyber Espionage – Malware – WebShell – Command and Control (C2) – Data Theft – Credential Harvesting – TinyTurla-NG – TurlaPower-NG – Chisel – PowerShell – UPX (Ultimate Packer for Executables) – Turla – Industries/All
Threat Analysis
Recently, the Russian nation-state threat actor Turla expanded its arsenal to include two new malware families, TinyTurla-NG and TurlaPower-NG, and a script that establishes a proxy command and control (C2) network, now widening its target set to include non-government organizations (NGOs). Using a massive set of offensive tools, Turla has been known to target entities worldwide, including the US, the European Union, Ukraine, and Asia. They’ve previously used malware families such as CAPIBAR and KAZUAR to target Ukrainian defense forces.
The proxy C2 script enables Turla operators to handle the TinyTurla-NG/TurlaPower-NG implants. It includes a WebShell component that Turla operators can use to execute commands. To date, all known systems that had the proxy C2 script have been compromised WordPress websites.
When the proxy C2 script loads, it performs various actions to establish the file structure that serves the TinyTurla-NG/TurlaPower-NG implants. Upon receiving a request, the script first checks for the existence of the logging directory, creating one if the directory does not exist. The script then verifies a specific COOKIE ID; if present and corresponds to a hardcoded value, the script will function as a WebShell, enabling persistent access to the compromised website.
When used as a WebShell, the script will decode the value of the variable $_COOKIE entry and execute it on the compromised website as a command. It will also check if the variable specified is a resource and read its contents. Once the actions are complete, the output or resource is sent to the operator, and the script stops executing.
If the operator provides an “id” in the HTTP request, the script will treat this as communication with an implant, such as TinyTurla-NG or TurlaPower-NG, which is the same variable passed by the TinyTurla-NG and TurlaPower-NG implants during communication.
Depending on the value accompanying the “id,” the script will perform various actions, such as writing the content sent by the operator to a specific file (<id>/tasks.txt) and recording the operator IP address and timestamp to another file, recording and sending the results of commands executed, save the contents of a file to the compromised website, read a file, and remove or delete a file.
Using the script to communicate with endpoints infected with TinyTurla-NG, Turla operators perform reconnaissance and exfiltration of files of interest, issuing three distinct sets of modular PowerShell commands/scripts, reconnaissance, copy file, and exfiltration.
Reconnaissance commands are used to enumerate files in a directory specified by the operator. The directory listing is returned to the operator to select files that can be exfiltrated. Copy file commands are base64-encoded commands/scripts issued to the infected systems to copy over files of interest from their original location to a temporary directory. Exfiltration commands/scripts, aka TurlaPower-NG, are used to exfiltrate selected files, where they can be retrieved from compromised websites.
All observed commands/scripts used during reconnaissance, copying, and exfiltration tasks contain hardcoded paths for files and folders of interest to Turla. In one known case, these locations contained files and documents used and maintained by Polish non-government organizations (NGOs) to conduct their day-to-day operations. The operators also used these scripts to exfiltrate Firefox profile data, reinforcing the assessment that Turla made attempts to harvest credentials, along with data exfiltration.
While TinyTurla-NG is enough to perform various malicious actions, Turla operators also chose to deploy three more tools to aid their operations, a modified Chisel tool, PowerShell scripts for harvesting Google Chrome or Microsoft Edge’s saved login data, and a tool for executing commands with elevated privileges.
The modified Chisel tool is UPX compressed and contains the command and control (C2) URL, port and communication certificate, and private keys embedded in the sample. Once it decrypts these artifacts, it creates a reverse SOCKS proxy connection to the C2 using the configuration R:5000:socks, where “R” stands for remote port forwarding, “5000” is the port on the adversary machine, and “socks” represents the protocol to use, SOCKS.
The PowerShell scripts for harvesting Google Chrome or Microsoft Edge’s saved login data resided at the location C:\windows\system32\edgeparser.ps1. This specific script is used to find login data from Microsoft Edge. This data file and the corresponding decryption key for the login data extracted from the endpoint are archived into a ZIP file and stored in the temp directory.
The tool for executing commands with elevated privileges is a small and straightforward Windows executable to create a new command line process on the system by impersonating the privilege level of another existing process. The tool will accept a target Process Identifier (PID) representing the process whose privilege level is to be impersonated and the command line that needs to be executed. Then, a new cmd[.]exe is spawned and used to execute arbitrary commands on the infected endpoint. The binary was compiled in early 2022 and was likely used in previous campaigns by Turla.
High-level overview of Turla’a communication structure:
- Proxy C2 script > TinyTurla-NG/TurlaPower-NG > proxy C2 script
- Proxy C2 script > TinyTurla-NG/TurlaPower-NG > Chisel client > Chisel C2
- Proxy C2 script > TinyTurla-NG/TurlaPower-NG > Elevated privileges tool > Exfiltrates data (assumed to send stolen credentials to the proxy C2 script)
Risk & Impact Assessment
The deployment of Turla’s newly developed tools, TinyTurla-NG and TurlaPower-NG, along with their script to establish a proxy command and control (C2) network, represents a heightened risk to organizations globally. This risk is particularly significant for non-government organizations (NGOs), which have been identified as new targets in Turla’s expanded operations. The complexity and sophistication of Turla’s arsenal, including WebShell components for persistent access and modular PowerShell commands for reconnaissance and exfiltration, underscore the threat actor’s capability to conduct espionage.
The likelihood of Turla’s operations impacting an organization hinges on several factors, including the organization’s geopolitical significance, sector, and existing cybersecurity posture. Given Turla’s historical focus and recent activities, entities within the US, the European Union, Ukraine, and Asia are at an elevated risk. The potential for adverse outcomes, such as unauthorized access, data theft, and the establishment of a persistent presence within targeted networks, is considerable.
The impact of a cyberattack by Turla, utilizing its latest toolset, can be severe and multifaceted. Financial repercussions may include significant expenditures on incident response, system restoration, and compliance with legal obligations. The operational impact, characterized by downtime and the disruption of services, can hinder an organization’s ability to function effectively, resulting in lost revenue and productivity. Moreover, the theft of sensitive information, such as proprietary data and credentials, threatens the confidentiality and integrity of an organization’s intellectual property and personal information, potentially leading to long-term strategic disadvantages.
Additionally, the reputational damage associated with a breach of this nature can erode stakeholder trust, impacting customer and partner relationships. Aggregating these impacts highlights the critical need for targeted organizations to assess their likelihood of being targeted by Turla and to prioritize implementing robust cybersecurity measures and incident response capabilities.
Source Material: Cisco Talos, TinyTurla-NG in-depth tooling and command and control analysis
Threat Actors Exploit ConnectWise ScreenConnect to Deliver Malware
Vulnerability Exploitation – Malware Deployment – Ransomware -Infostealer – Hacking Tool – ConnectWise ScreenConnect CVE-2024-1709 & CVE-2024-1708 – AsyncRAT – Vidar – Redline – Lockbit 3 (Lockbit Black) – Cobalt Strike – Industries/All
Threat Analysis
Threat actors are exploiting two vulnerabilities (CVE-2024-1709 and CVE-2024-1708) impacting ConnectWise ScreenConnect instances 23.9.7 and prior to deploy malware to servers or workstations with the client software installed. If malware or webshells were deployed before patching, these will not be removed, and any compromised environments must be investigated. See our TLDR blog on these exploits for more details.
CVE-2024-1708 is a path-traversal vulnerability, which may allow a threat actor to execute remote code or directly impact confidential data or critical systems. CVE-2024-1709 is an Authentication Bypass Using an Alternate Path or Channel vulnerability, which may allow a threat actor direct access to confidential information or critical systems.
Before these vulnerabilities became widely known on 19 February, Sophos observed a moderate number of events in which threat actors attempted to deploy malware or run a malicious command on a Sophos customer machine running ScreenConnect. Within days of the disclosure on 21 February, proof of concept (PoC) exploit code was released on GitHub, which, in addition to exploiting these vulnerabilities, adds a new user to the compromised system.
Since the release of the PoC exploit code, Sophos observed that the daily volume of events involving ScreenConnect has more than doubled. While many companies and managed service providers use ScreenConnect, not all behavior Sophos observed came directly from the vulnerabilities being exploited. However, Sophos assesses that a significant number of the current wave of events directly resulted from the increased threat actor attention to ScreenConnect.
Threat actors have been leveraging the exploits against ScreenConnect to launch various attacks and deliver a range of malware families to targeted machines. Beginning 22 February, at least one threat actor deployed a ransomware executable. Sophos suspects it is the same threat actor or group as an identical payload was discovered in more than 30 different Sophos customer networks. The distribution pattern strongly indicates the threat actor delivered the payload from a compromised server.
The ransomware executable was built using the Lockbit 3 (Lockbit Black) ransomware builder tool, which was leaked in 2022. However, the ransomware note did not state LockBit but “buhtiRansom.” Due to the leaking of the builder tool, this sample may not have originated with the operators of LockBit. The threat actors deploying this ransomware executable have consistently used the filename of “enc.exe” or “upd.exe” in the following locations:
- \Windows\Temp\ScreenConnect\23.9.6.8787\upd.exe
- \Windows\Temp\ScreenConnect\23.9.6.8787\enc.exe
- \users\[username]\temp\enc.exe
However, the “buhtiRansom” LockBit variant was not the only variant Sophos observed in the wild. A different threat actor attempted to drop another Lockbit ransomware payload using the certutil utility to download it from a web address, write it to the root of the C:\ drive with the filename svchost.exe, and execute it. While it failed to deploy on the Sophos customer environment, when Sophos analyzed the sample, it dropped an unidentifiable ransom note and changed the desktop background, which included the heading “LockBit Black.”
In addition to the ransomware activity Sophos observed, they also observed threat actors exploiting ScreenConnect to deliver AsyncRAT, Vidar/Redline infostealers, SimpleHelp remote access client followed by ransomware, InVentry Remote Support, Cobalt Strike payloads, Xworm, and SafeMode RAT, which was used to deliver a new instance of ScreenConnect.
Furthermore, WithSecure detected a threat actor exploiting ScreenConnect to deploy a new Windows variant of the KrustyLoader malware to download and launch a second-stage payload. KrustyLoader was first observed in January 2024 when threat actors exploited Ivanti ConnectSecure to deploy KrustyLoader Linux variants.
Risk & Impact Assessment
The exploitation of CVE-2024-1709 and CVE-2024-1708 presents a considerable risk to organizations using ScreenConnect versions before 23.9.8. The nature of these vulnerabilities—allowing for malware deployment and unauthorized access—significantly increases the likelihood of a successful cyberattack. Given the observed exploitation in the wild, including the deployment of various malware families post-exploitation and the availability of exploit code, the risk is real and immediate, increasing the probability of adverse outcomes. The availability of the exploit code also lowers the barrier of entry for threat actors of lower skill levels to leverage these vulnerabilities.
The impact of an attack exploiting these vulnerabilities on an organization could be multifaceted and severe. Financial repercussions may include direct costs associated with incident response, malware removal, system restoration, and potential ransom payments in cases where ransomware is successfully deployed. Operational impacts could see critical systems or data access disrupted, leading to significant downtime and loss of productivity. Moreover, the breach of sensitive or proprietary information could result in legal consequences, regulatory fines, and a loss of customer trust, culminating in long-term reputational damage.
The deployment of malware such as AsyncRAT, Vidar/Redline infostealers, or LockBit variants underlines the severity of potential data theft, unauthorized access, and further network compromise. The cumulative impact of these factors emphasizes the critical need for affected organizations to assess their exposure, prioritize mitigation efforts, and enhance their defensive postures against such sophisticated threats.
Source Material: Sophos, ConnectWise ScreenConnect attacks deliver malware
How APT29 is Adapting to Government and Corporations Move to Cloud Infrastructure
Threat Actor – APT29 – Cloud Service Targeting – Access Token Utilization – MFA Fatigue – Residential Proxies – Transportation and Warehousing, Educational Services, and Public Administration
Threat Analysis
APT29 (Midnight Blizzard, the Dukes, or Cozy Bear) has adapted to government and public organizations’ continuous modernization and move to cloud-based infrastructure, moving beyond traditional means of initial access, such as exploiting software vulnerabilities in an on-premises network, to target cloud services, employing various TTPs. Additionally, APT29 has expanded its targeted sectors to include aviation, education, law enforcement, local and state councils, government financial departments, and military organizations. Previously, they have targeted government, think tanks, healthcare, and energy for intelligence collection.
Various national government security organizations, including the NSA, the FBI, the UK National Cyber Security Centre (NCSC), the Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC), the Canadian Centre for Cyber Security (CCCS), and New Zealand Government Communications Security Bureau (GCSB), assess that APT29 is a cyber espionage group, almost certainly part of the Russian intelligence service (SVR).
To gain initial access to cloud services, APT29 operators target service accounts and dormant accounts belonging to users who no longer work at a victim organization but whose accounts remain on the system.
Account access is typically authenticated by username and password credentials or system-issued access tokens. APT29 operators use tokens to access their victims’ accounts without a password.
On multiple occasions, APT29 operators have successfully bypassed password authentication on personal accounts using password spraying and credential reuse. APT29 operators have also bypassed MFA through an “MFA bombing” or “MFA fatigue,” repeatedly pushing MFA authentication requests to a victim’s device until the victim accepts the notification.
Notably, following incident response eviction activities where the victim enforced password resets for all users, APT29 operators have been observed logging into inactive accounts and following password reset instructions, allowing the operator to regain access.
Once the operator has gained access to the cloud environment, if device validation rules are not established, they register their own device as a new device on the cloud tenant. However, if device enrollment policies have been established, there have been instances where these policies have denied APT29 operators access to the cloud tenant.
As network-level detection of suspicious activity has improved, APT29 operators have employed tactics, techniques, and procedures (TTPs) to avoid detection. One such TTP used by APT29 operators is the use of residential proxies.
Once APT29 gains initial access, operators can deploy highly sophisticated post-compromise capabilities, such as MagicWeb malware, as reported in 2022. Therefore, mitigating against the APT29’s initial access vectors is particularly important for network defenders.
Risk & Impact Assessment
APT29 (also known as Midnight Blizzard, the Dukes, or Cozy Bear) poses a substantial risk to various sectors, including Transportation and Warehousing (aviation), Educational Services, and Public Administration (law enforcement, local and state councils, government financial departments, and military organizations), by evolving their strategies to target cloud-based infrastructures. The risk emanates from APT29’s sophisticated tactics, techniques, and procedures (TTPs) tailored to compromise cloud services, bypassing traditional security measures. Given their strategic targeting and the advanced nature of their operations, the likelihood of APT29 impacting an organization is significant, particularly for entities within their expanded target sectors. Their history of evolving tactics indicates a persistent threat that organizations must actively guard against.
The impact of an APT29 operation on an organization could be severe and multifaceted. Successful infiltrations can lead to unauthorized access to sensitive information, data exfiltration, and potentially the deployment of malware like MagicWeb. Financial repercussions may include substantial costs associated with incident response, data recovery, legal liabilities, and potential fines for regulatory non-compliance. The reputational damage from an association with a high-profile compromise could lead to a loss of stakeholder trust, negatively affecting customer and partner relationships. Additionally, compromising sensitive or proprietary information could have lasting effects on competitive positioning and operational integrity. Given these potential impacts, understanding and mitigating the risks associated with APT29 is crucial for network defenders and organizational leadership.
Source Material: CISA, SVR Cyber Actors Adapt Tactics for Initial Cloud Access
Gootloader Facilitates Compromise of Domain Controllers, Backup Servers, and Remote File Servers
Malware – Gootloader – SystemBC – Cobalt Strike – Advanced IP Scanner – SEO Poisoning – JavaScript – PowerShell Execution – Scheduled Task Creation – Windows Management Instrumentation (WMI) – LSASS Memory – Windows Remote Management – Industry/All
Threat Analysis
In February 2023, a user searched for “Implied Employment Agreement” on an unidentified search engine, encountering an SEO-poisoned search result. Clicking on the search result directed the user to a compromised website, which displayed a fake user forum, employing a forum style known to be used by Gootloader. On this webpage, a deceptive link enticed the user to download what was supposed to be an implied employment agreement file. However, clicking the link downloads a zip archive.
The zip archive contained a JavaScript file bearing a name similar to their initial search term (implied employment agreement 24230.js). Clicking on this file triggered the Gootloader malware’s infection chain, dropping a heavily obfuscated JavaScript file, Frontline Management.js, within the user’s AppData folder. A scheduled task, InfrSiRfucture Technologies, was created to run this JavaScript file, incorporating a logon trigger for persistence to ensure its continuous operation. The sequence ends with the execution of an obfuscated PowerShell script, which calls another PowerShell script. This script performs information discovery about the host using built-in PowerShell Cmdlets and WMI queries.
The script then reaches out to a rotating list of remote endpoints. Approximately nine hours later, one of these remote endpoints responded with a download containing three components, Gootloader Stage 1 and 2, and a script. Gootloader Stage 1 was an obfuscated DLL, and Gootloader Stage 2, when deobfuscated, was an executable file. The script wrote Stages 1 and 2 into the registry before deobfuscating Stage 1 and loading it into memory. Stage 1 then deobfuscated Stage 2, the final Gootloader payload, and loaded a Cobalt Strike Beacon.
Next, an instance of process injection into dllhost was observed, accompanied by network connections to several remote hosts checking for LDAP and SMB. LDAP network traffic to a domain controller was also observed, indicating discovery operations targeting various groups, including Domain Users, Administrators, RDP Users, and Domain Administrators.
Approximately ten minutes later, the threat actor laterally moved within the network, creating a remote service to disable Windows Defender’s Real-Time Monitoring. Subsequently, they transferred a Cobalt Strike beacon executable over SMB and executed it as a service. Following this, additional process injections and access to the LSASS memory were observed on the compromised hosts.
The threat actor continued trying this technique to move to various workstations and domain controllers. However, on the domain controllers, Windows Defender remained operational and successfully blocked the attempts to launch the beacons. Despite these setbacks, the threat actor continued their efforts from a compromised workstation, utilizing PowerView to conduct additional discovery tasks.
Due to Windows Defender blocking their efforts to compromise the domain controller, the threat actor was forced to adjust their strategy. They executed a PowerShell script implementation of SystemBC onto a workstation. This script initiated communication with a command and control server and established persistence by creating a registry run key. Following this, the threat actor executed multiple commands through remote services on the domain controller to ensure RDP was enabled. Once RDP access was verified, they logged into the domain controller over RDP by routing the connection through the infected workstation using SystemBC.
With access to the domain controller, the threat actor transferred a text file containing a series of commands through their RDP session, aimed at further attempts to disable Windows Defender. Despite these efforts, their deployment of a PowerShell beacon seemed to be unsuccessful. Despite this setback, the threat actor installed Advanced IP Scanner on the domain controller and initiated a network scan. While that was running, they explored a remote file share, accessing a document containing password-related information.
The threat actor then utilized Windows Remote Management (WinRM) to execute multiple commands on a backup server, ensuring that RDP access was enabled and open. After ensuring RDP was available, they connected to the server via RDP, reviewed the backup configurations for the environment, and deployed the SystemBC PowerShell script on the server.
After this activity, there was a noticeable lull in the threat actor’s actions, with no significant activities recorded for the next five hours. Upon their return, they resumed accessing hosts over RDP, searching for sensitive information and looking through file shares for documents about passwords while operating from the backup server. Additionally, they executed Advanced IP Scanner again, this time from the backup server. Throughout their RDP session, they interactively viewed data. Yet, no direct signs of data exfiltration were observed during this phase of activity. After this, the threat actor’s presence on the network ceased, and they were not detected again before being evicted from the network.
Based on previous intelligence conducted by Kroll, ransomware payloads were not deployed and requests for extortion were not observed, even in cases with significant exfiltration. Additionally, stolen data was not leaked or discussed on the dark web or other threat actor websites. Kroll assesses that the goal of these attacks is for corporate espionage, which aligns with our assessment that Gootloader’s targeting aspect seems to align with a nation-state threat actor(s) using it as an initial access method.
Risk & Impact Assessment
This Gootloader infection chain poses a considerable risk to organizations, characterized by its sophisticated evasion techniques and the ability to facilitate further malicious activities. This risk is amplified by Gootloader’s distribution method, primarily through SEO poisoning, which preys on users’ trust in search engine results. Given the stealthy nature of Gootloader’s infection process, there is a possibility that an organization will be impacted. The infection’s complexity, combined with this threat actor’s persistence and capability to adapt strategies, heightens the risk of successful penetration and subsequent network compromise.
The impact of a cyberattack leveraging Gootloader can be severe for any organization. If the initial infection is not promptly detected and mitigated, threat actors can gain deep network access, as illustrated by the progression of this attack to domain control. This could lead to substantial financial repercussions, encompassing immediate incident response costs and long-term consequences like regulatory fines and litigation expenses due to potential data breaches. The reputational damage from such an attack could lead to diminished customer trust and loss of business, which may be exacerbated if sensitive or proprietary information is exfiltrated. Moreover, the operational disruption and the resources allocated for remediation could detract from an organization’s strategic objectives and growth. Therefore, understanding and mitigating the risks associated with Gootloader are crucial for maintaining organizational resilience against such sophisticated threats.
Source Material: The DFIR Report, SEO Poisoning to Domain Control: The Gootloader Saga Continues
i-Soon Data Leak Analysis
i-Soon Data Leak – Cyber Espionage – Hardware-based Hacking Device – Remote Access Trojans – DDoS Botnet – Public Administration – Information – Critical Infrastructure
Threat Analysis
The leaked data can be organized into groups, such as complaints, chat records, financial information, products/tools, employee information, and details about foreign infiltration. Based on a preliminary analysis of the leaked data, i-Soon appears to have compromised several government departments, including those from India, Thailand, Vietnam, South Korea, and NATO.
Victim data and targeting lists, as well as names of the clients who requested them, show a company that competes for low-value hacking contracts, revealing the maturing nature of China’s cyber espionage ecosystem. It demonstrates how the Chinese government’s targeting requirements drive a competitive marketplace of independent contractor hackers-for-hire. However, historical targeting by Advanced Persistent Threats, assessed as PRC contractors, does not provide a solid basis for determining future targets.
One document lists targeted organizations and the fees i-Soon earned by compromising them. One contract to collect data from Vietnam’s Ministry of Economy paid out $55,000; other ministries were worth less. Another leaked document shows an employee compromising a university not on the target list, which their supervisor deemed an accident. According to a Unit 42 analysis, i-Soon has targeted India, Thailand, Vietnam, South Korea, and NATO governments. We found documents mentioning various UK government entities, such as “British Treasury,” “Department for Business, Energy and Industrial Strategy,” and “Department for Brexit.” However, it’s not clear whether these were proposed targets, actual victims, or something else.
Within the leak are several manuals related to various tools and platforms, which, based on our analysis, appear to be usage documentation intended for end-users. One document contains a footer that translates to “Anxun Information Technology Co., Ltd.” It seems to be a product manual for various tools sold by i-Soon. However, it’s unclear whether i-Soon are these tools’ developers, resellers, or end-users.
During our analysis, we found spreadsheets noting “product sales contract” and “technical service contract.” Based on this evidence, we speculate that i-Soon develops or resells tools to third parties. However, the majority of the items in the spreadsheets are from 2021. One line in a screenshot of a spreadsheet noted “Public Security Bureau Special Attack and Defense Project.” Still, it’s not clear what this project is. Based on this notation, we speculate that it’s a contract to carry out an attack on behalf of the Chinese Public Security Bureau.
One manual describes the usage of a Twitter (X) Tool (Twitter Public Opinion & Control Guidance System), which can obtain the user’s Twitter email and phone number, perform real-time monitoring, read personal messages, and publish tweets on the user’s behalf.
Other manuals relate to custom Remote Access Trojans (RATs). One is a Windows version (HECTOR) that includes features for process/service/registry management, remote shell, keylogging, file access logging, obtaining system information, disconnecting remotely, and uninstallation. A Linux version (TracedStone) supports outdated CentOS 5/6/7 & Ubuntu 12/14 versions. Features include remote shell, file management, Socks5 proxy via SocksCap64, and port reuse. A 2019 US indictment directly references Treadstone, stating that it is used to control the Winnti malware. The Mac version (Mac Remote Control Management System) also has a remote shell, file management, screenshots, and keylogging features.
There are also versions for mobile devices. The iOS version (iOS Remote Control Management System) is claimed to support all iOS device versions without jailbreaking, with features ranging from hardware information, GPS data, contacts, media files, and real-time audio records as an extension. However, this document dates back to 2020. The Android version (Android Remote Control Management System) can dump messages from all popular Chinese chatting apps, such as QQ, WeChat, Telegram, and MoMo. It can elevate the system app for persistence against internal recovery.
i-Soon also acquired or manufactured hardware-based portable Hacking Devices. One device, a WiFi-capable device (Wifi Sensorless Implantable Device), can perform injection into targeted Android devices. The device is portable, plug-and-play, and supports 3G and 4G. After a successful injection, it can get device info, GPS, SMS, contacts, call logs, and files.
There is also a “WiFi Proximity Attack System” with Standard and Mini editions. The standard version, disguised as a Xiaomi battery, can be installed on a specifically crafted device and be used to infiltrate the internet network. However, the leaked documents do not explain how. It can crack WiFi passwords, LAN port sniffing, SOCKS tunnel, port projection, remote shell, file management, and remote detonation (self-destruct). The Mini version is a plain, printed control board (PCB) disguised as a power strip, power adapter, etc, but can be installed inside anything. It can be set up to connect to the target’s WiFi and establish a SOCKS tunnel with the internal network.
There is a specialized hardware device that alerts operatives when a device with a specific WiFi MAC address is in range, disrupts WiFi signals, and can be controlled with a dedicated smartphone. Operatives working abroad can use a dedicated Tor-like device to hop between endpoints to establish safe communication. Operatives also have access to a user lookup database, which lists user data, including phone number, name, and email, which can be correlated with social media accounts. There is also an email text search platform. Emails can be automatically imported via SMTP, POP3, iMAP, and Exchange. An Exchange server can be configured to add “non-plaintext” transfer during transport.
i-Soon also acquired or developed a targeted “automated penetration testing platform.” The framework supports Windows, Linux, web services, and networking equipment with support for various pen-testing frameworks. It also supports specialized APT attack scenarios, including generating email templates, browser-based attacks, malicious Office document generation, and more.
There is also a DDoS Botnet Client. The botnet client is 29kb sized and can be deployed to Windows, Linux, or generic IoT devices with a total throughput of 10~100 Gbps or GBps.
Risk & Impact Assessment
Based on the i-Soon data leak, the organization poses a considerable risk to various organizations worldwide, particularly those identified within the leaked documents as past or potential targets. The availability of detailed information regarding i-Soon’s operational tactics, techniques, and procedures may elevate the risk profile for similar entities. Dissemination of this information sheds light on China’s cyber espionage threat landscape, showing how, at least in part, it’s corporation-driven.
The risk is exacerbated by the leak of specific tools and platforms, which could be, to an extent, reverse-engineered by other threat actors. Given i-Soon’s historical targeting of critical sectors and government entities, there is a likelihood that these tools or newer variants will be used against similar targets. While the exact scope of i-Soon’s tool proliferation is challenging, the nature of the leaked information suggests that these tools may be widely used within China’s cyber espionage operations.
Source Material: SentinelOne, MalwareBytes, Palo Alto Unit 42, and @AzakaSekai_
Latest Additions to Data Leak Sites
Manufacturing – Professional, Scientific, and Technical Services – Information – Health Care and Social Assistance – Retail Trade – Transportation and Warehousing – Real Estate and Rental and Leasing – Finance and Insurance – Construction
Analysis
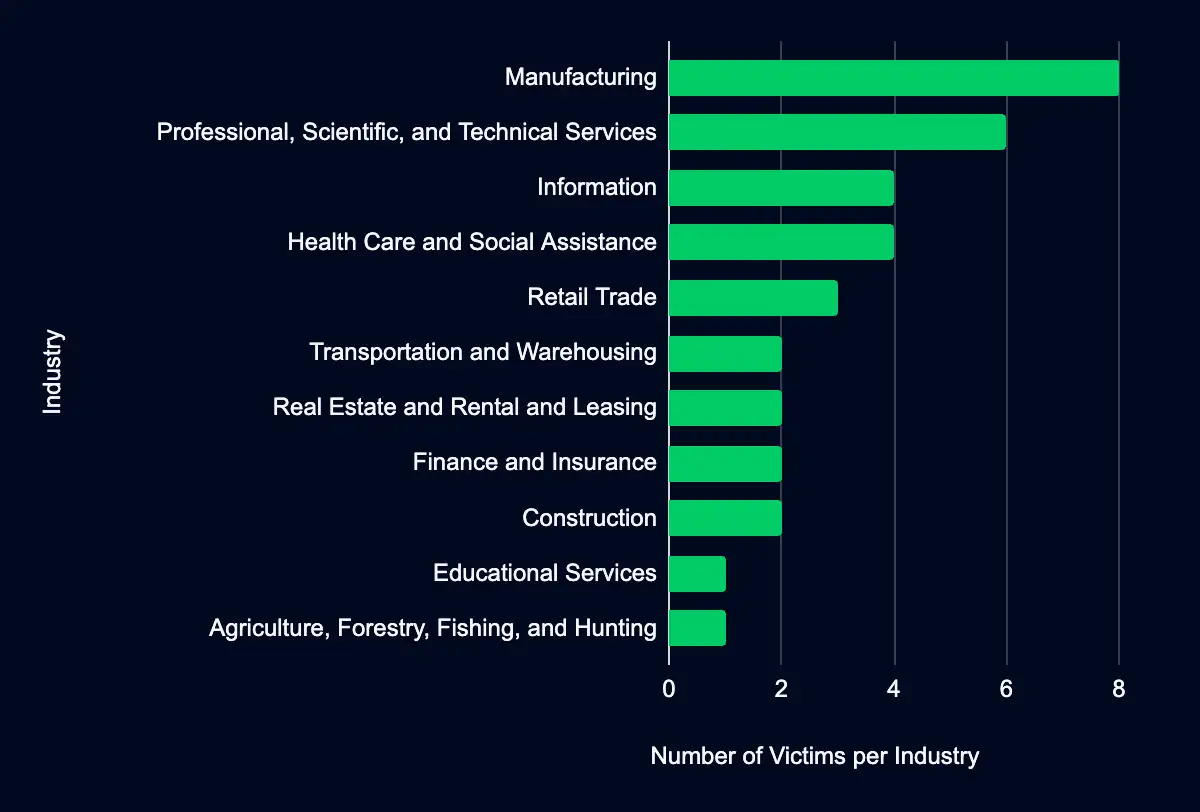
Recent data from data leak sites presents a compelling picture of ransomware and data extortion activities. In the past week, 35 organizations have been listed as victims, with a marked concentration in the United States, accounting for 57% of the total victims listed. This geographic focus may indicate a higher targeting preference in this region due to the large base of potential victims or perhaps specific vulnerabilities associated with the region’s cyber infrastructure or prevalent business practices.
Regarding industry targeting, the data reveals a diverse range of sectors being affected, with Manufacturing leading the list at 23%, followed by Professional, Scientific, and Technical Services (17%), Information (11%), Health Care and Social Assistance (11%), and Retail Trade (9%). This spread across various industries suggests that the actors are not discriminating much regarding the sector, aiming for a wide range of targets. It could also reflect the opportunistic nature of these actors, who may target organizations perceived as more likely to pay a ransom, regardless of their industry. The significant impact on the Manufacturing sector could suggest a higher susceptibility or perhaps a higher likelihood of paying ransoms due to the critical nature of manufacturing operations and the high cost of downtime.
Another possibility is that many organizations fall under these sectors, providing a broad and diverse target base. The fact that industries like Health Care and Social Assistance are also significantly targeted underscores the critical impact of ransomware attacks on public services and the potential for these incidents to have far-reaching consequences beyond financial loss, including impacts on health and safety.
The focus on industries like Professional, Scientific, and Technical Services, Information, and Retail Trade indicates a range of motives and methods among threat actors, possibly reflecting the varying levels of cybersecurity maturity and the differing value of data organizations hold in these sectors. The data underscores the need for heightened cybersecurity vigilance and preparedness across all sectors, particularly those identified as top targets.
Recent data highlights the activities of several prominent ransomware actors, with Black Basta, ALPHV, Bianlian and 8base, Qilin and Cactus, and Monti and Medusa standing out due to the number of victims listed on their leak site. A notable omission to our data set is Lockbit, who has averaged about 18 new victims per week. Notably there are reports that Lockbit is attempting to relaunch their operations following an international law enforcement takedown operation.
Black Basta has emerged prominently, affecting 8 organizations, accounting for 23% of the incidents. This group’s targeting strategy seems geographically focused, with a significant preference for the USA (50%) and a notable presence in Switzerland (25%). Industry-wise, Black Basta shows a broad targeting range but has a particular focus on Professional, Scientific, and Technical Services (38%). The diversity in their targeting, including sectors like Retail Trade, Real Estate, and Manufacturing, indicates a versatile and opportunistic approach, aiming at industries where they can likely cause significant disruption or extract valuable data.
ALPHV (BlackCat), with 5 victims and 14% of the incidents, predominantly targets the USA (80%), suggesting an operational focus or success rate within this region. The Health Care and Social Assistance sector appears to be a significant target for ALPHV, comprising 40% of its attacks. This could indicate a strategy of exploiting healthcare data’s critical and sensitive nature for higher ransom demands. Other targeted sectors include Transportation and Warehousing, as well as Professional Services and Information, showcasing a varied interest likely driven by the perceived value of the data or potential for disruption.
Bianlian & 8base, combined, have impacted 8 organizations. Their focus, especially in the USA (63%), aligns with the overall trend of heightened ransomware risks in this country. Manufacturing is particularly affected, with 50% of their attacks targeting this industry, possibly due to its lower tolerance for operational downtime. Other sectors like Retail Trade and Information reflect their broader strategic interests in sectors with valuable data or critical operational uptime requirements.
Qilin & Cactus appear to operate more globally, with their activities spread across multiple countries, including the USA, Switzerland, Netherlands, Italy, France, and Chile. This global footprint might reflect a more scattered or opportunistic targeting approach or a sophisticated capability to engage diverse targets. Manufacturing again stands out as a primary industry of focus, suggesting a consistent pattern among threat actors recognizing the sector’s vulnerabilities.
Lastly, Monti & Medusa have a more limited impact than the others but still present a significant threat, especially in the USA and Germany. Their targeting across Transportation, Real Estate, Manufacturing, and Health Care shows no specific industry preference, perhaps indicating a more opportunistic approach or a testing phase of their capabilities.
Our analysis strives to be comprehensive, utilizing the most current data available. However, it is crucial to acknowledge this data set’s inherent discrepancies. Despite our best efforts, the data set may include victims who are not listed on leak sites or were previously listed. Additionally, we may have omitted victims we could not verify. Additionally, victims are classified based on the NAICS industry classification system. While we only list one industry classification per victim, it’s possible that a victim could fall under multiple industries classification, which may inadvertently skew results.
We also recognize that our data set does not represent the full scope of ransomware victims, as it only reflects those listed on leak sites, and groups do not list every victim they attacked on their sites. As such, while we believe our analysis provides valuable insights, it should be considered with an understanding of these potential discrepancies.
CISA Adds CVE-2024-1709 CVEs to Known Exploited Vulnerabilities Catalog
ConnectWise ScreenConnect CVE-2024-1709
Threat actors are exploiting a vulnerability in ConnectWise ScreenConnect, causing CISA to add it to their Known Exploited Vulnerabilities catalog. They exploit this vulnerability to perform authentication bypass and deploy ransomware and other malware families.
Analysis
CVE-2024-1709 targets ConnectWise ScreenConnect, commonly used in corporate environments for remote monitoring and management of IT systems. With a CVSS v3 score of 10.0, this vulnerability signifies a critical severity, allowing authentication bypass and may allow a threat actor direct access to confidential information or critical systems. Notably, this vulnerability has been actively exploited in the wild, as detailed in our report titled “Threat Actors Exploit ConnectWise ScreenConnect to Deliver Malware.” ConnectWise’s response, involving the release of a patched firmware version 23.9.8 or higher, highlights the urgency and necessity of timely updates in response to emerging threats.
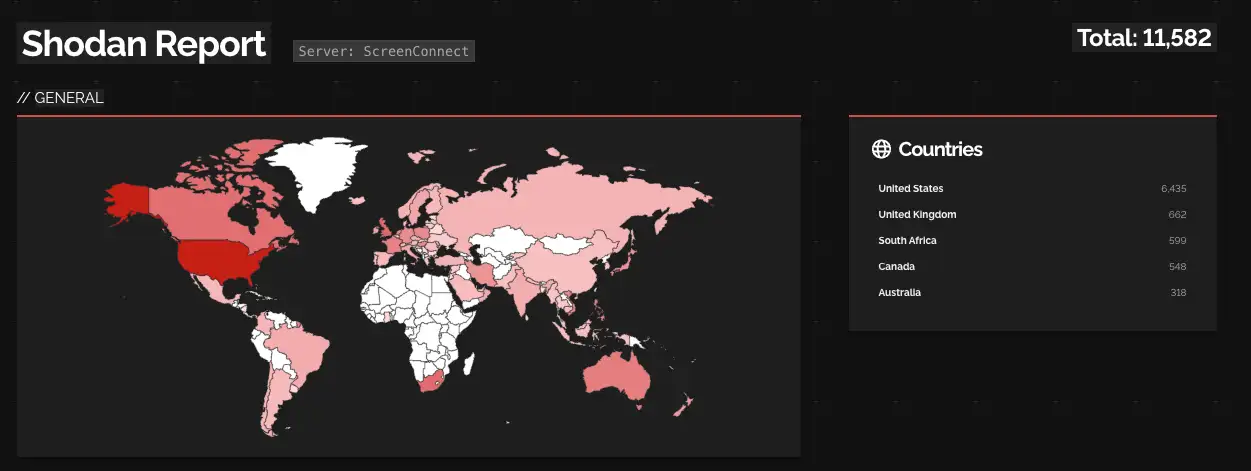
A Shodan search shows over 11,500 ScreenConnects exposed to the internet, with almost 6,500 in the US. However, not all of these are vulnerable to CVE-2024-1709 or CVE-2024-1708.
The discovery and subsequent mitigation of this vulnerability demonstrate a persistent challenge in network security: the need for constant vigilance and prompt response to emerging threats. The active exploitation of CVE-2024-1709 is a stark reminder of the real-world implications of such vulnerabilities, necessitating a robust and agile security posture from vendors and users alike.
In conclusion, the addition of this CVE to CISA’s catalog highlights specific risks associated with ConnectWise ScreenConnect but also underscores the broader theme of proactive security management in an ever-evolving digital landscape. Regular updates, strong authentication practices, and timely responses to identified vulnerabilities remain paramount in safeguarding against potential exploits and maintaining the integrity of networked systems.
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
| CVE ID | Vendor | Product | Description | CISA Due Date | Used in Ransomware Campaigns |
|---|---|---|---|---|---|
| CVE-2024-1709 | ConnectWise | ScreenConnect | ConnectWise ScreenConnect contains an authentication bypass vulnerability that allows an attacker with network access to the management interface to create a new, administrator-level account on affected devices. | 2/29/2024 | Known |
Source Material: CISA
Let’s Secure Your Organization’s Future Together
At Deepwatch, we are committed to helping organizations like yours navigate the intricate world of cyber threats. Our cybersecurity solutions are designed to stay ahead of the curve, providing you with the proactive defenses needed to protect your organization from these threats.
Our team of cybersecurity professionals is ready to evaluate your systems, provide actionable insights, and implement robust security measures tailored to your needs.
Don’t wait for a cyber threat to disrupt your operations. Contact us today and take the first step towards a more secure future for your organization. Together, we can outsmart the threats and secure your networks.
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.

Share