State-Sponsored Intrusions, Cloud-Targeting Malware, and Rising Ransomware: China and ELF-Based Threats Dominate the Cyber Landscape
In our latest Cyber Intelligence Brief, Deepwatch ATI looks at new threats and techniques to deliver actionable intelligence for SecOps organizations.
Each week, we look at in-house and industry threat intelligence and provide ATI analysis and perspective to shine a light on a spectrum of cyber threats.
Contents
State-Sponsored Cyber Attacks: China’s Persistent Threat to Global Industries
The Rundown
Recent cyber espionage activities attributed to Chinese threat actors, primarily linked to two attack clusters—PurpleHaze and ShadowPad—targeting various industries, including government and cybersecurity vendors like SentinelOne. These operations, spanning from 2024 to early 2025, include sophisticated attacks on critical infrastructure and data exfiltration campaigns. One of the most alarming findings is the continuous targeting of cybersecurity firms, which are high-value targets due to their access to sensitive client data and their role in protecting digital ecosystems. SentinelOne’s internal investigations successfully thwarted some of these operations, including reconnaissance on their own servers, although the full extent of the threat remains under scrutiny.
The Chinese-nexus actors behind these attacks employed various tactics, techniques, and procedures (TTPs), including the deployment of malware like the modular ShadowPad backdoor and the GOREshell backdoor. These tools were used in targeted intrusions across sectors such as manufacturing, government, finance, and telecommunications. One notable intrusion in January 2025 involved an IT logistics provider managing SentinelOne’s hardware, although the firm’s internal security measures ensured no compromise occurred. However, persistent reconnaissance and malware infections across other organizations revealed an extensive global campaign, with over 70 entities affected by these cyber espionage activities.
The findings emphasize the growing threat posed by state-sponsored cyber actors, particularly those linked to China’s cyber operations, who are adapting to increasingly sophisticated defense measures. The article urges greater transparency and collaboration within the cybersecurity industry to enhance collective defenses, given that these attackers aim not only to infiltrate targeted organizations but also to undermine the trust and security of the broader cybersecurity ecosystem. This disclosure aims to spur more proactive intelligence sharing and improve defenses against the evolving cyber threat landscape.
Source Material: SentinelOne
Evolving ELF-Based Malware: A New Era of Cloud Security Risks
The Rundown
Unit 42 researchers have uncovered a rising threat targeting cloud environments: ELF-based malware that is specifically crafted to exploit Linux systems within cloud infrastructures. These ELF malware families, including backdoors, remote access Trojans (RATs), and data-wiping binaries, are increasingly used by threat actors to infiltrate and manipulate cloud services. With Linux-based systems making up 70-90% of cloud computing instances, attackers are adapting existing Linux malware to cloud environments, improving and evolving their methods to target these systems. This growing trend signals that ELF binaries will be pivotal in future cloud security breaches.
The investigation highlights five major ELF-based malware families, such as NoodleRAT, Winnti, and SSHdInjector, all of which have been actively updated and used over the past year. These malware families leverage techniques like dynamic linker hijacking to inject malicious code into critical Linux services, enabling persistent access, remote command execution, and data exfiltration. Their continuous development and use in attacks demonstrate their evolving sophistication, especially in exploiting vulnerabilities within cloud workloads and containers.
With cloud-based alerts increasing by 388% in 2024, the threat landscape has significantly shifted. As organizations continue to move operations to the cloud, there is an urgent need for enhanced security measures, including robust endpoint detection and prevention systems. These systems, especially those leveraging machine learning, can identify and neutralize these evolving ELF malware threats. Cloud service providers and enterprises must act now to protect their cloud infrastructures from this growing and highly adaptable threat.
Source Material: PaloAlto Unit42
Ransomware and Data Extortion Trends (June 3 – 9)
The Rundown
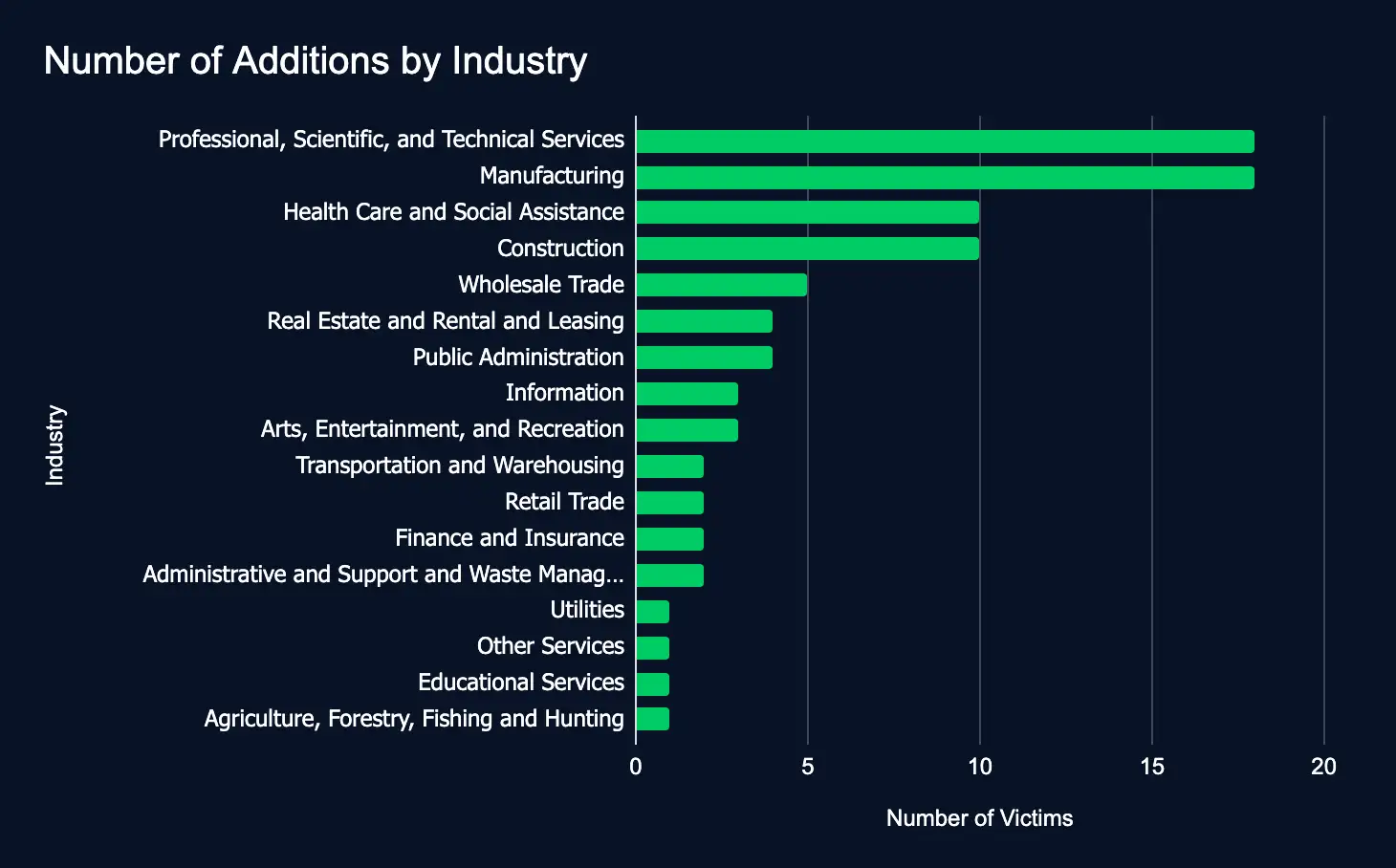
Between June 3 and 9, ransomware and data extortion activity saw a slight increase, with more victim organizations appearing on leak sites. A total of 87 organizations across 17 industries were listed on 20 ransomware and extortion platforms, up from 78 the previous week. This small rise indicates a stabilization in threat actor behavior rather than a significant surge in overall activity.
Adversaries continue to target high-value sectors such as Professional Services, Manufacturing, Healthcare, and Construction. The majority of affected organizations are based in key markets, including the United States, Canada, and Australia. This pattern reflects a continued strategic focus on specific industries and regions.
For business leaders, this trend highlights an ongoing and sustained threat landscape. While activity levels may fluctuate, attackers remain concentrated on high-value industries. Organizations should take this as an opportunity to consistently assess and strengthen their cybersecurity posture, ensuring risk mitigation, detection, and response strategies remain aligned with the evolving threat environment.
Key Trends:
- Most affected industries:
- Professional, Scientific, and Technical Services
- Manufacturing
- Health Care and Social Assistance
- Construction
- Most affected countries:
- United States
- Canada
- Australia
- Most active leak sites:
- Akira
- Qilin
- Sarcoma
Exploited Vulnerabilities in Google, Roundcube, Erlang, Microsoft and Wazuh Products Added to CISA’s Catalog
The Rundown
Between June 5th and 11th, five high-impact vulnerabilities affecting products from Google, Roundcube, Erlang, Microsoft, and Wazuh were added to CISA’s Known Exploited Vulnerabilities (KEV) catalog.
Left unaddressed, these flaws present a serious risk to organizational security, creating opportunities for active exploitation. Due to the widespread use of these technologies across industries, the potential impact is both far-reaching and severe.
The likelihood of exploitation by state-sponsored threat actors and financially motivated attackers is significantly elevated. Immediate remediation is essential to sustaining operational resilience and safeguarding critical systems from compromise.
Google | Chromium V8 CVE-2025-5419
- Vulnerability Description: Google Chromium V8 contains an out-of-bounds read and write vulnerability that could allow a remote attacker to potentially exploit heap corruption via a crafted HTML page. This vulnerability could affect multiple web browsers that utilize Chromium, including, but not limited to, Google Chrome, Microsoft Edge, and Opera.
- Exploitation Details: The vulnerability involves out-of-bounds memory access in the V8 engine, which can be triggered via malicious JavaScript or WebAssembly code embedded in web pages. Exploitation can lead to heap corruption, enabling attackers to execute arbitrary code
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-05
- Recommended Mitigation Due Date: 2025-06-26
Roundcube | Webmail CVE-2024-42009
- Vulnerability Description: RoundCube Webmail contains a cross-site scripting vulnerability. This vulnerability could allow a remote attacker to steal and send emails of a victim via a crafted e-mail message that abuses a Desanitization issue in message_body() in program/actions/mail/show.php.
- Exploitation Details: Attackers exploit this vulnerability by sending an email containing malicious HTML and JavaScript code. When a user opens the email in Roundcube Webmail, the embedded script executes in the browser context.
- Exploited in a Ransomware attack? Unknown
- Public Proof-of-Concept (PoC): Yes
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-09
- Recommended Mitigation Due Date: 2025-06-30
Erlang | Erlang/OTP CVE-2025-32433
- Vulnerability Description: Erlang Erlang/OTP SSH server contains a missing authentication for critical function vulnerability. This could allow an attacker to execute arbitrary commands without valid credentials, potentially leading to unauthenticated remote code execution (RCE). By exploiting a flaw in how SSH protocol messages are handled, a malicious actor could gain unauthorized access to affected systems. This vulnerability could affect various products that implement Erlang/OTP SSH server, including—but not limited to—Cisco, NetApp, and SUSE.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-09
- Recommended Mitigation Due Date: 2025-06-30
Web Distributed Authoring and Versioning (WebDAV) CVE-2025-33053
- Vulnerability Description: Web Distributed Authoring and Versioning (WebDAV) contains an external control of file name or path vulnerability. This vulnerability could allow an unauthorized attacker to execute code over a network. This vulnerability could affect various products that implement WebDAV, including but not limited to Microsoft Windows.
- Exploitation Details: The exploitation involves a malicious .url file crafted to exploit the vulnerability. When a user opens this file, it triggers the execution of a legitimate Windows utility with a manipulated working directory pointing to a malicious WebDAV server. This causes the system to execute a malicious file from the attacker’s server instead of the legitimate system file.
- Exploited in a Ransomware attack? Unknown
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-10
- Recommended Mitigation Due Date: 2025-07-01
Wazuh | Wazuh Server CVE-2025-24016
- Vulnerability Description: Wazuh contains a deserialization of untrusted data vulnerability that allows for remote code execution on Wazuh servers.
- Exploitation Details: An attacker with API access can send a specially crafted JSON payload to vulnerable endpoints, such as /security/user/authenticate/run_as, to trigger code execution.
- Exploited in a Ransomware attack? Unknown
- Public Proof-of-Concept (PoC): Yes
- Action: Apply updates per vendor instructions.
- Date Added to catalog: 2025-06-10
- Recommended Mitigation Due Date: 2025-07-01
Recommendations
ATI recommends mitigative action occur according to the mitigation “Due Date” recommended by CISA.
Source: CISA
What We Mean When We Say
Estimates of Likelihood
We use probabilistic language to reflect the Intel Team’s estimates of the likelihood of developments or events because analytical judgments are not certain. Terms like “probably,” “likely,” “very likely,” and “almost certainly” denote a higher than even chance. The terms “unlikely” and “remote” imply that an event has a lower than even chance of occurring; they do not imply that it will not. Terms like “might” reflect situations where we are unable to assess the likelihood, usually due to a lack of relevant information, which is sketchy or fragmented. Terms like “we can’t dismiss,” “we can’t rule out,” and “we can’t discount” refer to an unlikely, improbable, or distant event with significant consequences.
Confidence in Assessments
Our assessments and projections are based on data that varies in scope, quality, and source. As a result, we assign our assessments high, moderate, or low levels of confidence, as follows:
High confidence indicates that our decisions are based on reliable information and/or that the nature of the problem allows us to make a sound decision. However, a “high confidence” judgment is not a fact or a guarantee, and it still carries the risk of being incorrect.
Moderate confidence denotes that the information is credible and plausible, but not of high enough quality or sufficiently corroborated to warrant a higher level of assurance.
Low confidence indicates that the information’s credibility and/or plausibility are in doubt, that the information is too fragmented or poorly corroborated to make solid analytic inferences, or that we have serious concerns or problems with the sources.
Share